Before diving into this month's Known Exploited Vulnerabilities update, I'd like to note that this post covers data from June, July, and August so we are calling it a Summer report. This is due prioritizing other research over the last few month that we’ve been focused on publishing, which are worth a read:
- State of Exploitation 1H-2024
- Taking an Evidence Based Approach to Prioritization
- Weaponized Vulnerabilities Deserve a Seat at the Prioritization Table
Key Takeaways
- VulnCheck captured exploitation evidence for 158 vulnerabilities with initial evidence emerging during June, July and August.
- The evidence of known exploitation was collected from over 35 different sources.
- Software that topped the list of new Known Exploited Vulnerabilities (KEVs) includes Microsoft Windows, Apache OFBiz, PHP Everywhere, OSGeo GeoServer, ServiceNow, Google Chromium, and the Linux Kernel.
- CISA added 42 CVEs to their KEV list during June, July and August. For 71.4% (30/42) of those vulnerabilities, VulnCheck provided evidence earlier than CISA.
Summer Vendor and Product Breakdown

The 158 CVEs with known exploitation evidence were associated with 119 software suppliers across 136 unique products. The following software topped the list with two or more CVEs with known exploitation:
- Microsoft Windows (10)
- Apache OFBiz (3)
- PHP Everywhere (3)
- OSGeo GeoServer (3)
- Totolink (2)
- ServiceNow (2)
- Google Chromium (2)
- Linux Kernel (2)
Summer Trends in Vulnerability Exploitation Disclosure
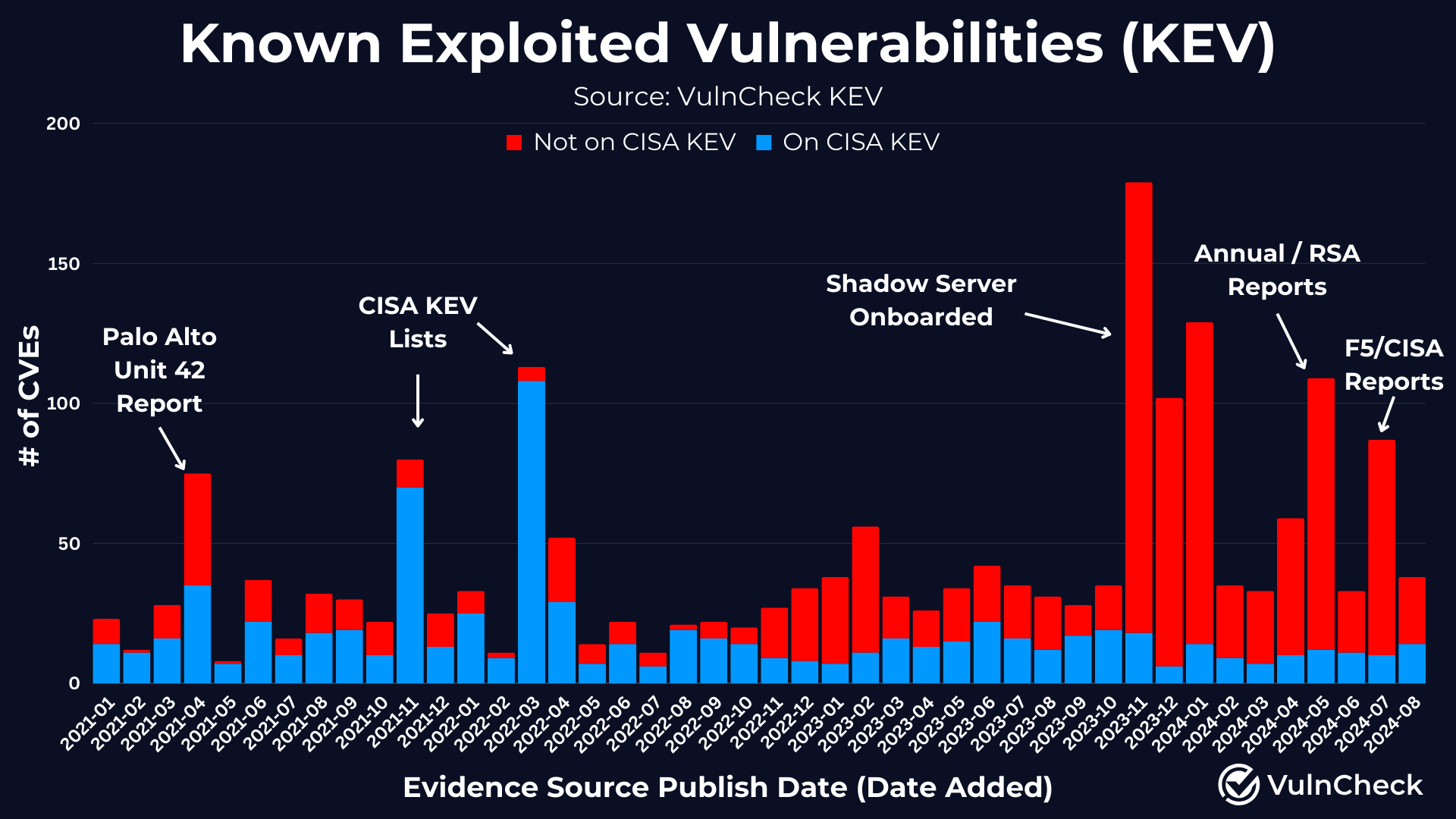
Vulnerability exploitation disclosure occasionally appears to spike, as evidence of exploitation is reported publicly at different times or when we onboard new sources like ShadowServer.
We expect the baseline of new KEVs to range between 30-50 vulnerabilities per month, with occasional spikes around quarterly reports in October/November and the start of the new year. A increasing trend towards an increase in public disclosure of exploitation evidence appears to be continuing along with the growth in vulnerability disclosure, which we encourage, as it enhances organizations' visibility into vulnerability exploitation.
If you use VulnCheck KEV, you might have noticed an overall increase in the total number of Known Exploited Vulnerabilities beyond just the new evidence we captured. This is due to our ongoing efforts to capture historical exploitation evidence. We hope to write more about this soon to provide some clarity on this topic.
Who Was the First to Report the Exploited Vulnerabilities?
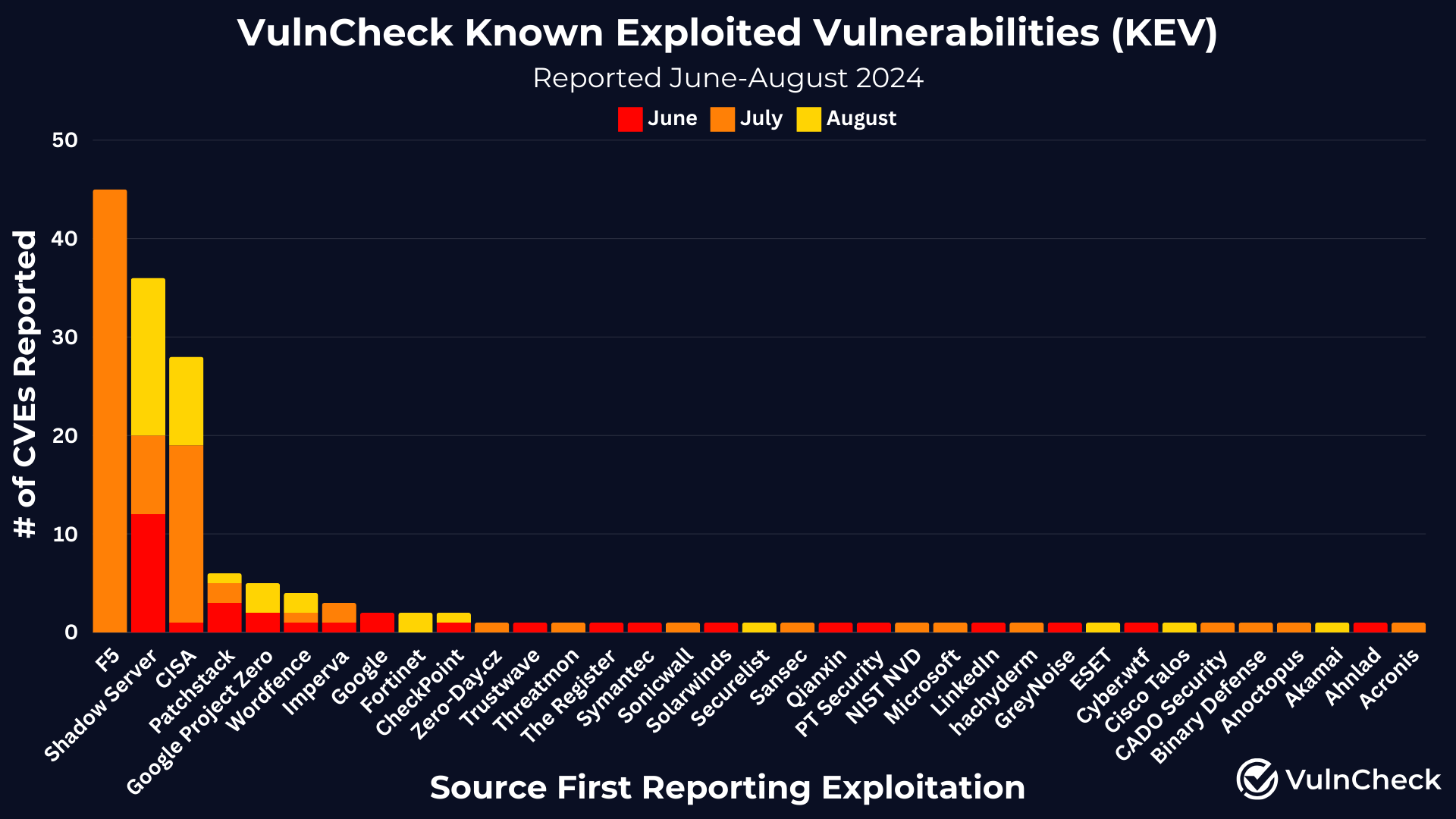
We collected exploitation evidence from over 35 sources. Notably, F5 published two reports, and CISA released a report titled "North Korea Cyber Group Conducts Global Espionage Campaign," both with significant numbers of CVEs. Additionally, several vulnerabilities on the CISA KEV list were disclosed simultaneously with the vendors, such as Microsoft. For a deeper dive into these details, you can access the full dataset of the VulnCheck KEV here.
It's worth noting that we audited and added evidence from Patchstack and Wordfence over the last few months. Both these projects track wordpress plugin vulnerabilities and exploitation so VulnCheck KEV now has much better coverage for wordpress plug-ins thanks to these sources.
How did VulnCheck KEV do compared with CISA KEV?
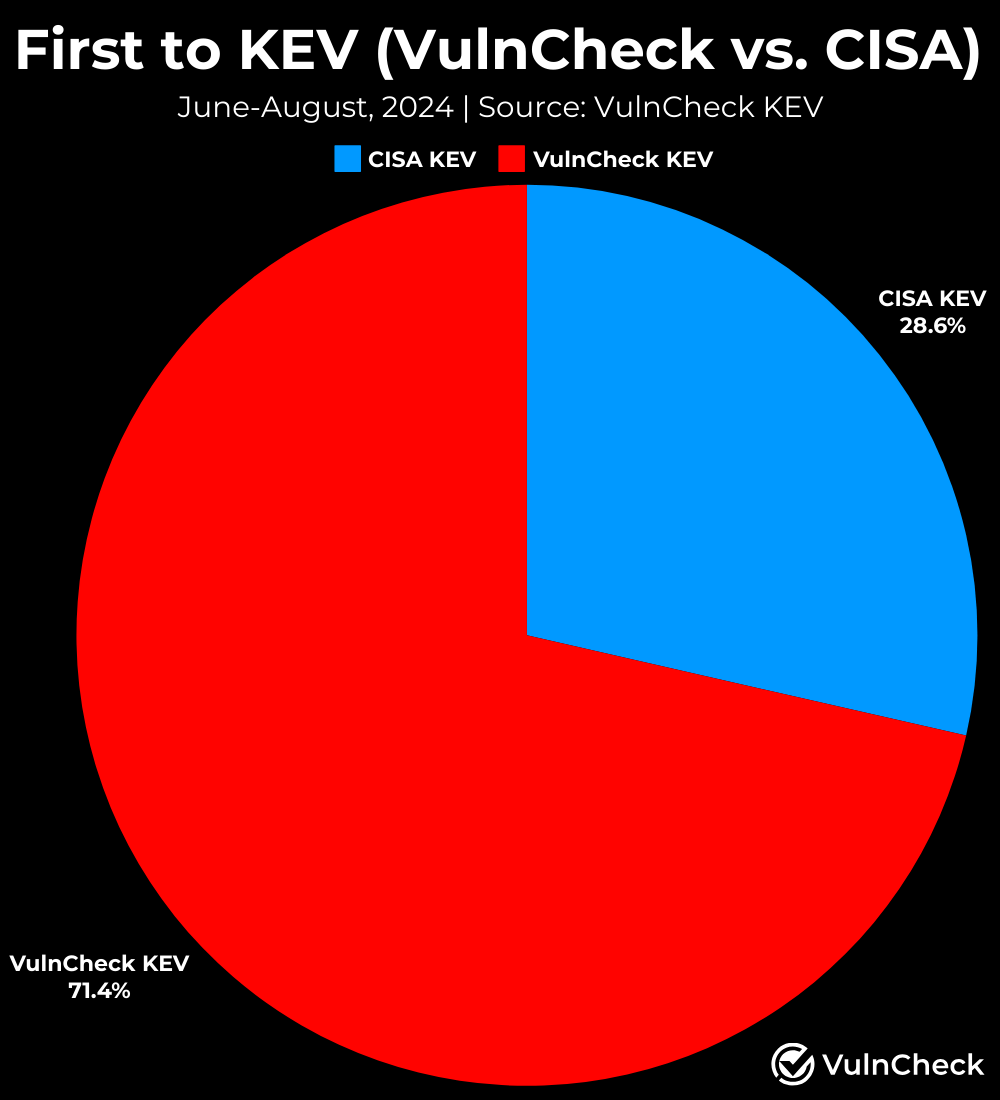
Between June and August, VulnCheck added 158 CVEs to its Known Exploited Vulnerabilities (KEV) list, while CISA added 42 CVEs to their KEV list. For 30 of these 42 (71.4%) vulnerabilities, VulnCheck provided evidence earlier than CISA, enabling organizations to gain early visibility into vulnerabilities that later appear on the CISA KEV list.
The 12 vulnerabilities disclosed by CISA KEV included OSgeo GeoServer, Dahua IP Camera, Microsoft Project, Microsoft Windows (7),Versa Director (1) and Roundcube (1). With the exception of Dahua, OSgeo GeoServer and Roundcube, these vulnerabilities were disclosed within 2 days of the exploitation evidence. The Microsoft vulnerabilities were also disclosed at the same time through Microsoft MSRC which we also capture in VulnCheck KEV.
A Quick peek into Scoring Systems Mapped to Known Exploitation
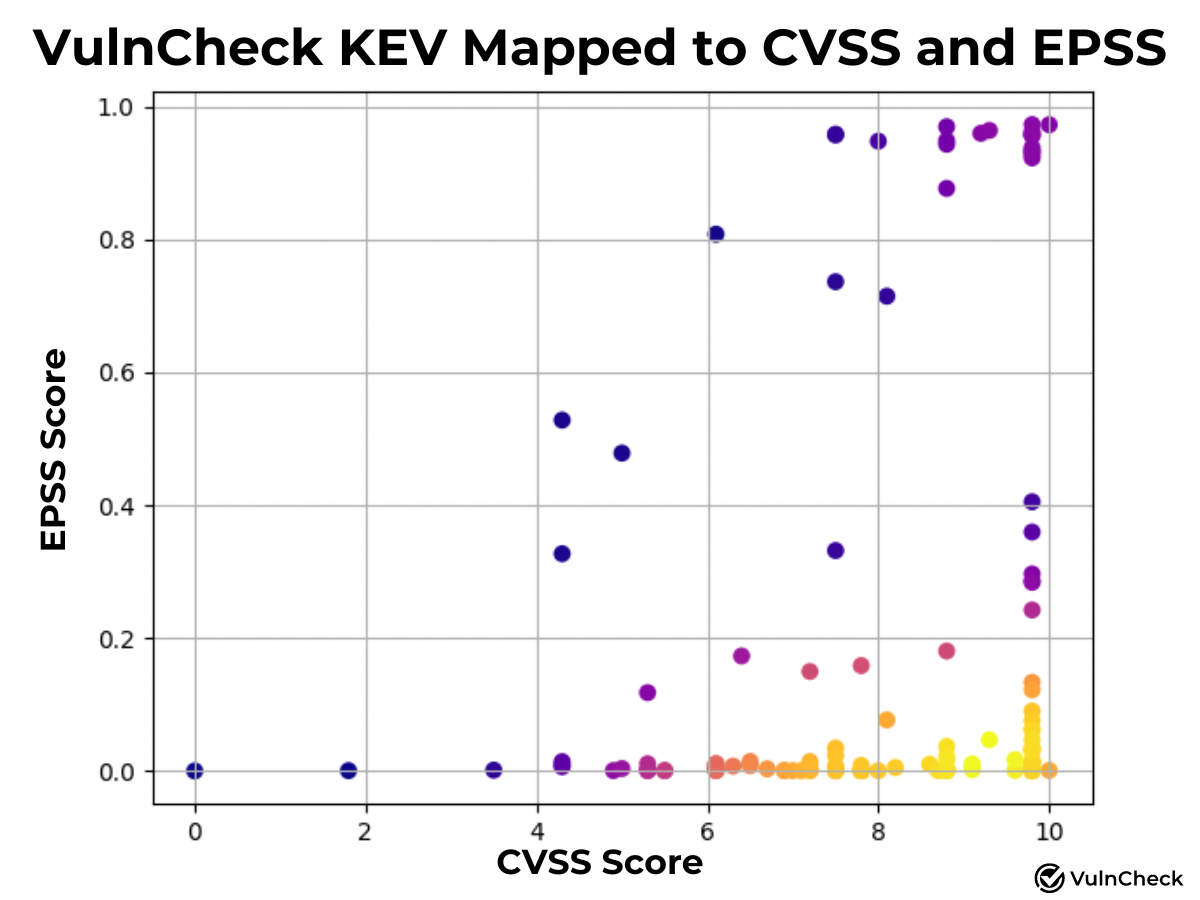
We've continued to analyze Known Exploitation in relation to vulnerability scoring systems, specifically CVSS and EPSS. Our goal is to gain insights into how these scoring systems can better reflect known exploitation and emerging threats.
To enhance visibility into CVSS and EPSS, I created a plot of known exploitation mapped to these systems. Yellow indicates higher density, while purple represents lower density of CVEs associated with known exploitation. By applying an EPSS score (Early September scoring) of 0.1 or a 10% probability of exploitation or higher, we find that 40 CVEs (25.3%) align with Known Exploitation captured for the first time during June, July and August. With a CVSS-BT score of 9 or higher, 57 CVEs (36.1%) map to Known Exploitation. We plan to explore scoring systems further to provide deeper insights when we have more time.
Related to the topic of vulnerability prioritization, ee suggest exploring these articles on the topic of vulnerability prioritization:
- Taking an Evidence Based Approach to Prioritization: https://vulncheck.com/blog/vulnerability-prioritization
- Do We Need Yet Another Vulnerability Scoring Systems? (Ben Edwards, Bitsight): https://www.bitsight.com/blog/do-we-need-yet-another-vulnerability-scoring-system-if-its-ssvc-thats-resounding-yass
Access VulnCheck Known Exploited Vulnerabilities (KEV) Catalog
For those eager to dive deeper into known exploited vulnerabilities, you can start by utilizing VulnCheck Community a free resource including VulnCheck KEV and VulnCheck NVD++.
About VulnCheck
VulnCheck is helping organizations not just to solve the vulnerability prioritization challenge - we’re working to help equip any product manager, CSIRT/PSIRT or SecOps team and Threat Hunting team to get faster and more accurate with infinite efficiency using VulnCheck solutions.
We knew that we needed better data, faster across the board, in our industry. So that’s what we deliver to the market. We’re going to continue to deliver key insights on vulnerability management, exploitation and major trends we can extrapolate from our dataset to continuously support practitioners.
Are you interested in learning more? If so, VulnCheck's Exploit & Vulnerability Intelligence has broad threat actor coverage. Register and demo our data today.