On the weekends, I often dive into vulnerability data, searching for new sources of known exploitation. This process frequently leads to uncovering evidence of vulnerabilities being exploited in the wild that haven't been documented before. As I comb through older security advisories, blogs, and forums, I often encounter familiar mentions of HD Moore and the Metasploit project.
Given this, I set out to highlight in this research the importance of prioritizing and remediating weaponized vulnerabilities by mapping Metasploit modules with Known Exploited Vulnerabilities to provide deeper insight.
What is a Weaponized Vulnerability?
Weaponized vulnerabilities are those with explicit malicious intent, historic malware usage, prior reports of exploitation, or inclusion in point-and-click exploitation frameworks or kits. Projects facilitating point-and-click exploitation could include malicious exploit kits, such as those previously tracked by Contagio, or open source or commercial offerings like Metasploit, VulnCheck Initial Access Intelligence, CANVAS, or Core Impact. Additionally, weaponized exploits often have secondary payloads, droppers, or implants. In our State of Exploitation Reportpublished in May, we observed 2% of vulnerabilities over the past decade that have been weaponized.
Observations from Mapping Known Exploitation to the Metasploit Project
A First Look at Metasploit Modules Mapped to Known Exploited Vulnerabilities
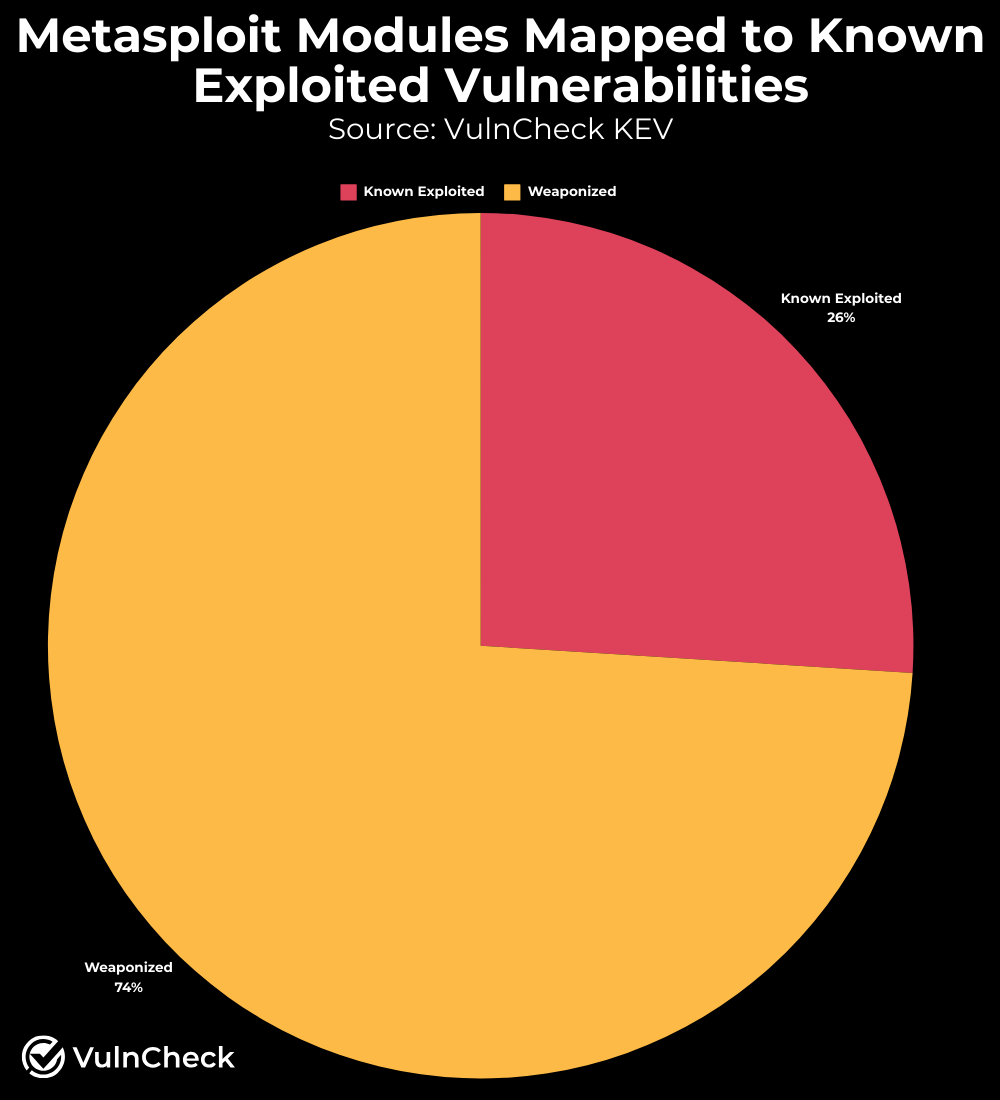
Initially, I explored existing vulnerabilities with a Metasploit module that mapped to a Known Exploited Vulnerability (KEV) in VulnCheck KEV. I also considered breaking out CISA KEV, which is included in VulnCheck KEV, for this analysis. The data revealed that 26% of Metasploit modules are associated with a Known Exploited Vulnerability. This percentage seemed lower than expected, prompting further investigation.
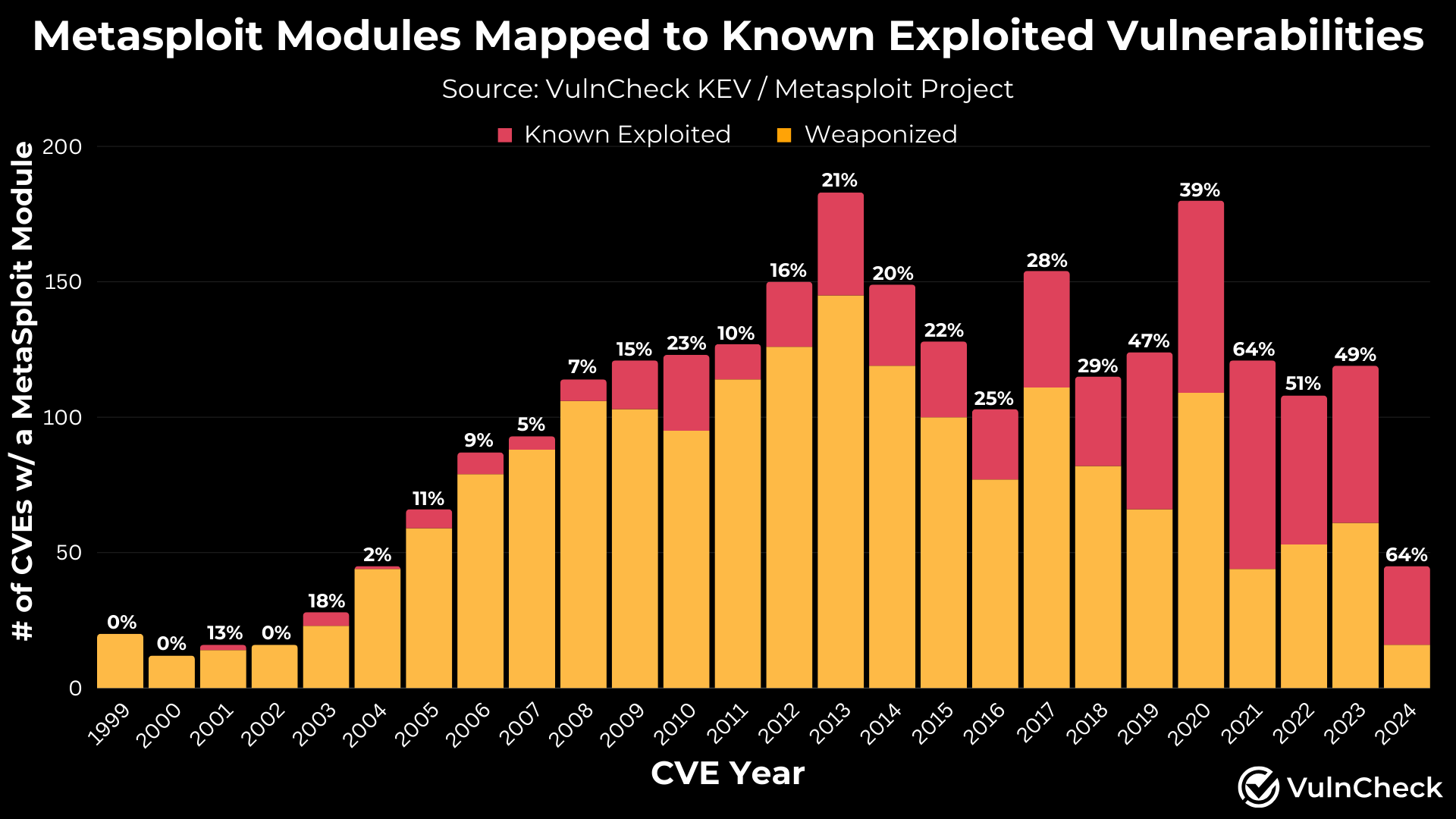
Exploring Metasploit Modules Mapped to Known Exploited Vulnerabilities by Year

Next, I analyzed the Metasploit data by CVE-Year (not the CVE publish date). The results showed a high percentage of relatively newer vulnerabilities with known exploitation and much lower percentages for older vulnerabilities. From 2020 to 2024 (to date), 56% of Metasploit modules have been associated with known exploitation. Prior to 2020, this ratio drops to 19% across vulnerabilities from 1999 to 2019. This trend aligns with the timing of when we began collecting evidence of known exploitation and when CISA launched the CISA KEV. It suggests that older vulnerabilities may have been exploited, but evidence is less readily available.
Metasploit Module Availability Related to VulnCheck KEV
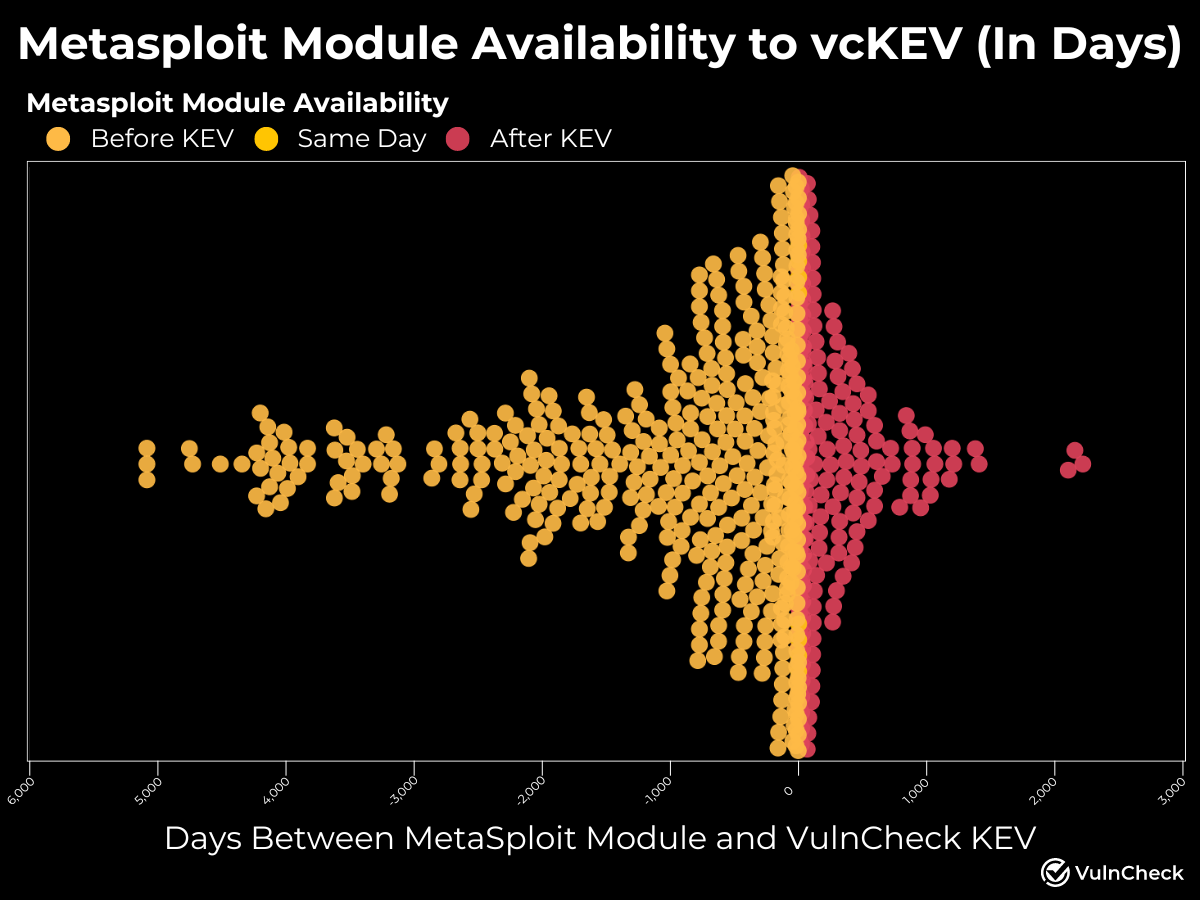
Another important consideration is the availability of Metasploit modules in relation to when a vulnerability was added to VulnCheck KEV. The data shows that 66.6% (443 out of 665) of the Metasploit modules with known exploitation evidence were available on or before the date of the indexed exploitation evidence.
Using Known Exploitation and Weaponization in an Evidence-Based Approach to Vulnerability Prioritization
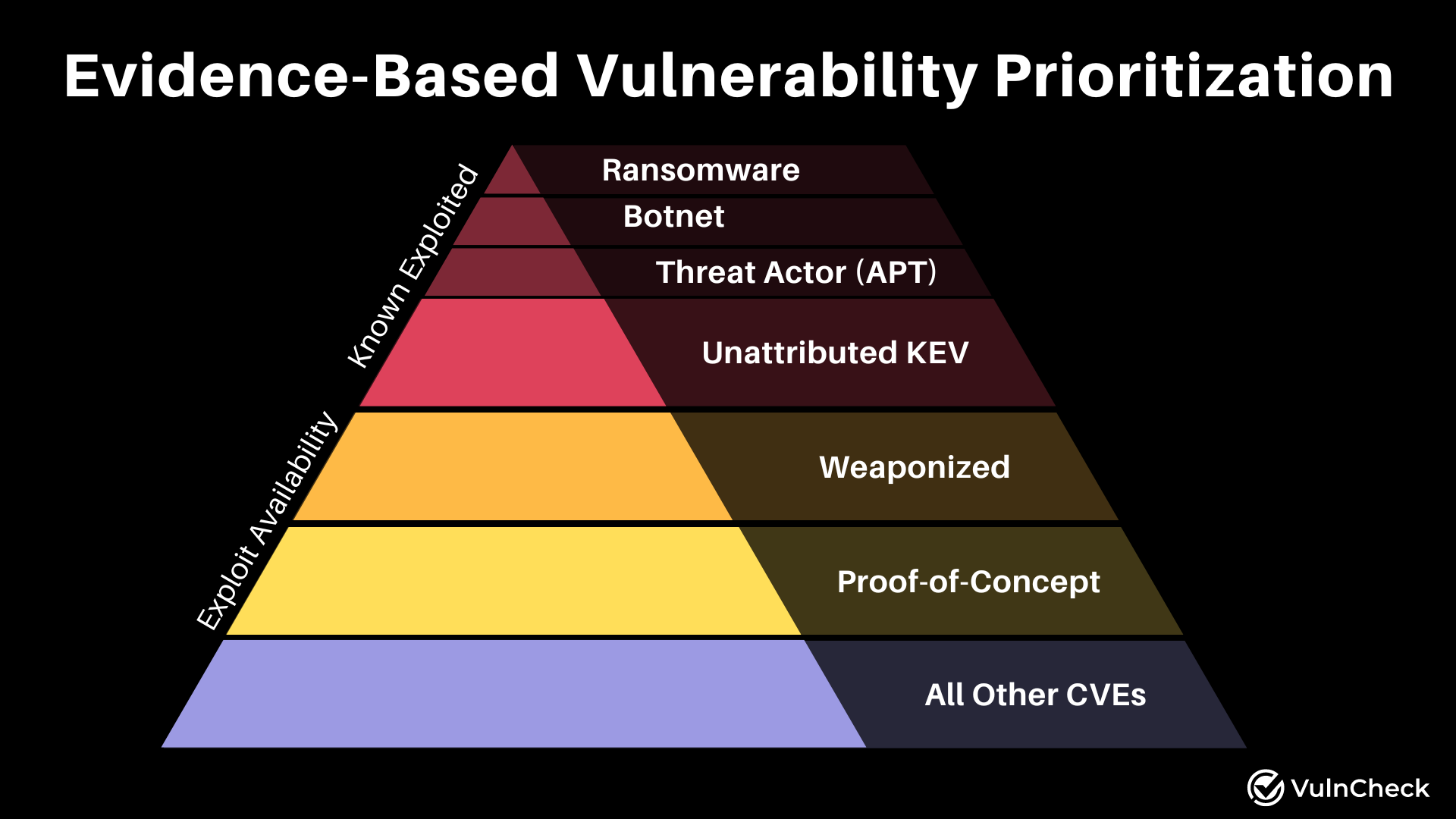
Security practitioners have long struggled to make informed decisions due to limited exploit evidence and threat context. By giving weaponized vulnerabilities such as Metasploit Modules, a seat at the prioritization table, in addition to known exploited vulnerabilities, security practitioners can get to vulnerabilities faster that are likely to be exploited.
Learn more about how VulnCheck can help you take an evidence-based approach to Vulnerability prioritization here: https://vulncheck.com/blog/vulnerability-prioritization
About VulnCheck
VulnCheck is helping organizations not just to solve the vulnerability prioritization challenge - we’re working to help equip any product manager, CSIRT/PSIRT or SecOps team and Threat Hunting team to get faster and more accurate with infinite efficiency using VulnCheck solutions.
We knew that we needed better data, faster across the board, in our industry. So that’s what we deliver to the market. We’re going to continue to deliver key insights on vulnerability management, exploitation and major trends we can extrapolate from our dataset to continuously support practitioners.
Are you interested in learning more? If so, VulnCheck's Exploit & Vulnerability Intelligence has broad threat actor coverage. Register and demo our data today.