According to the Verizon DBIR, vulnerability exploitation in breaches is up 180% from last year. More unfortunate news for defenders? One of the most significant challenges security teams face today is knowing which vulnerabilities to prioritize.
Security practitioners have long struggled to make informed decisions due to limited exploit evidence and threat context. Having the right threat context is critical for driving effective remediation outcomes, especially with limited resources.
At VulnCheck, we deliver the necessary threat context and intelligence teams need to make smarter, faster and better informed decisions about which vulnerabilities to remediate first.
To help security practitioners prioritize vulnerabilities using exploit evidence, we've outlined key considerations and strategies in this blog. Alongside exploit intelligence, it’s crucial to incorporate environmental and asset context using decision-based frameworks such as Stakeholder-Specific Vulnerability Categorization.
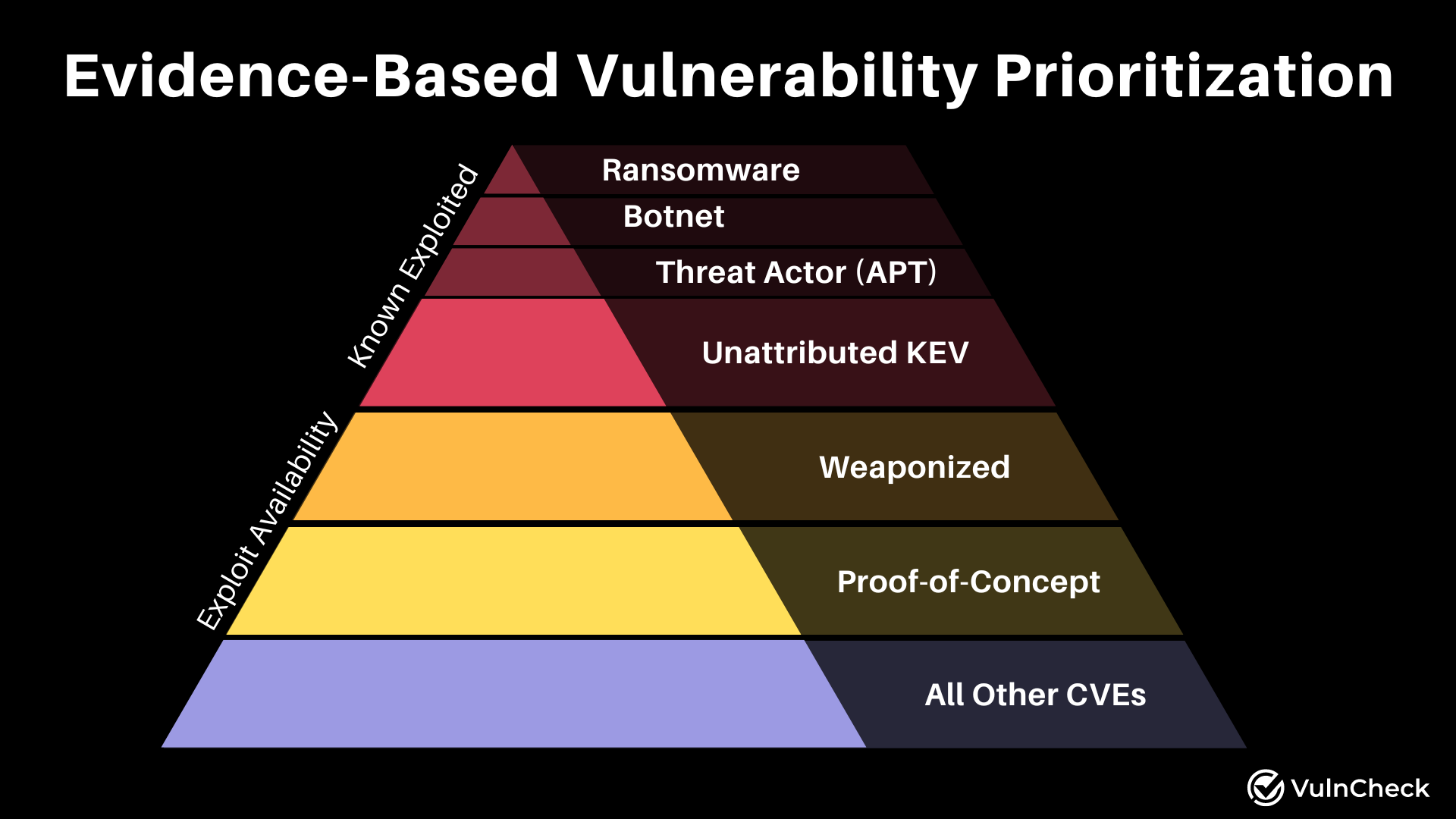
What Exploit Evidence Should Be Prioritized First?
Known Exploited Vulnerabilities (KEV)
A Known Exploited Vulnerability is a one with confirmed exploitation evidence. Depending on the asset context, these should be treated with urgency and remediated as soon as possible..
The importance of remediating Known Exploited Vulnerabilities is underscored by CISA’s BOD 22-01, which mandates federal agencies address such vulnerabilities. CISA states, “Known exploited vulnerabilities should be the top priority for remediation.”
In our State of Exploitation Report published in May, we observed that 1.1% of vulnerabilities over the past decade are known to be exploited in the wild.
If you’re looking for insight beyond CISA’s KEV, the VulnCheck KEV is a community resource that offers organizations expanded visibility into more than 2,500 known exploited vulnerabilities. That’s a 130% increase over CISA’s (KEV) catalog with data from hundreds of sources worldwide.
What Evidence Can Be Used to Further Prioritize Known Exploited Vulnerabilities?
Additional evidence can help determine the prioritization of a known exploited vulnerability. Organizations may consider:
- Ransomware: Vulnerabilities used in ransomware campaigns are often prioritized due to their widespread impact.
- Botnets: Vulnerabilities exploited by botnets, a collection of infected computers controlled by a common attacker, are critical to address.
- Threat Actors: Specific vulnerabilities exploited by known threat actors pose increased risks and should be prioritized.
It’s also critical to take immediate action when a known exploited vulnerability is exposed on the internet.
What Vulnerabilities Should Be Considered After Known Exploited Vulnerabilities?
Weaponized Vulnerabilities
Weaponized vulnerabilities are those with explicit malicious intent or reported exploitation. These include exploits within malware or those facilitating easy exploitation (Projects such as: MetaSploit, VulnCheck IAI, CANVAS, Core Impact). Weaponized exploits often have secondary payloads, droppers, or implants.
In our State of Exploitation Report published in May, we observed 2% of vulnerabilities over the past decade that have been weaponized.
How Does Exploit Code Availability Factor into Prioritization?
Proof of Concept (POC) exploit code demonstrates exploitation and indicates risk. POC exploits, such as blog posts, curl requests, or Python scripts, are often used in real-world attacks. The number of POC exploits associated with a vulnerability correlates with its likelihood of being weaponized or exploited.
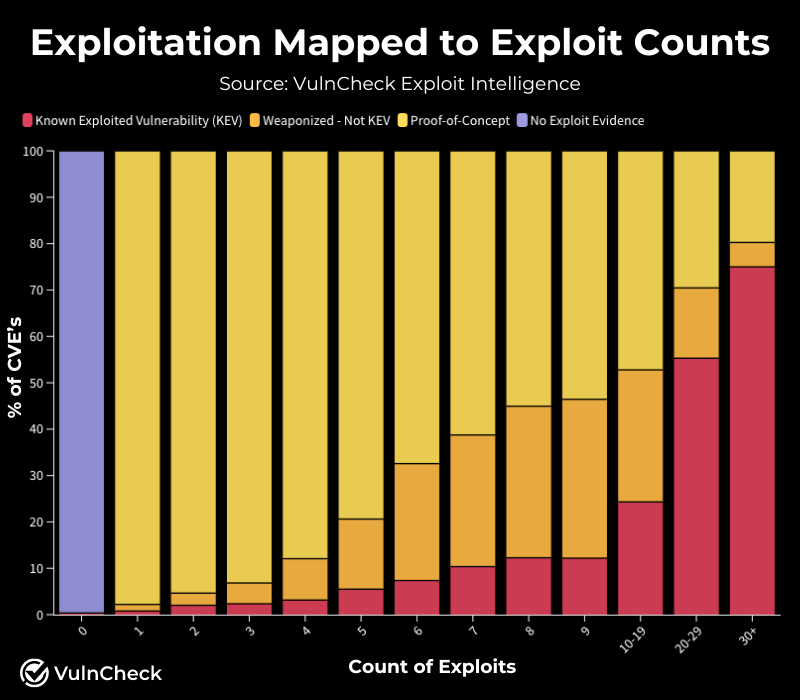
Another consideration for using POC exploit’s for vulnerability prioritization is ensuring that the POCs are validated to ensure they are actually real POCs. It’s not uncommon for code to be posted claiming to be an exploit when, in fact, the code does not contain an exploit or, even worse, it contains malware. VulnCheck validates POC exploits to ensure they are legitimate POC exploits.
In our State of Exploitation Report published in May, we observed 31% of vulnerabilities over the past decade that have proof-of-concept exploit code.
What Other Considerations Should I Use When Prioritizing Vulnerability Remediation?
While this post primarily focuses on prioritizing vulnerabilities based on evidence of exploitation, there are additional factors to consider. Incorporating these factors within decision-based frameworks like Stakeholder-Specific Vulnerability Categorization (SSVC) can provide a more comprehensive approach. Often, vulnerability attributes beyond threat intelligence can help provide further visibility into the risk a vulnerability might pose. Attributes such as CVSS metrics, CAPEC, CWE, MITRE ATT&CK, threat actors, targeted industries, targeted countries, and categorizations are frequently used by VulnCheck customers to determine the risk a vulnerability poses within their environment.
Beyond exploitation evidence, consider asking the following questions:
- Is the device/application connected to the internet?
- Is the device/application used for initial access?
- Is the device/application controlled by a user and susceptible to phishing attacks?
- Is the vulnerability remotely exploitable?
- Is the vulnerability automatable?
- Is the vulnerability reachable?
- Are there mitigations in place for the vulnerability?
When Should I Use a Scoring System such as CVSS or EPSS?
VulnCheck provides CVSS and EPSS scoring systems as data points for decision-making.
There are important considerations:
- CVSS: Base scores do not account for exploitation evidence without enrichment (CVSS-BT). Organizations required to use CVSS should enrich scores with exploit intelligence and environmental context. VulnCheck provides automated CVSS-BT enrichment. Organizations that are in highly regulated industries often opt to use CVSS-BT and are required to use CVSS scoring.
- EPSS: The Exploit Prediction Scoring System predicts the likelihood of exploitation within the next 30 days. While helpful in identifying vulnerabilities that could pose a threat to an organization, the score lacks any context and often overlooks known exploitation, weaponized vulnerabilities and vulnerabilities with high exploit counts. EPSS should be used as a supplementary data point for longer-tail prioritization after addressing higher-risk vulnerabilities such as known exploitation, weaponization and vulnerabilities with higher exploit counts. If you plan to use EPSS with a decision-based framework with SSVC, you can also consider defining thresholds within your prioritization schema.
Taking The Next Steps in Evidence-Based Prioritization
Prioritizing vulnerabilities effectively requires a comprehensive approach that integrates exploit evidence, environmental context, and additional risk factors. By utilizing threat intelligence and vulnerability attributes, organizations can make informed decisions in prioritizing vulnerabilities and reducing an organization's overall risk.
At VulnCheck, we provide the tools and intelligence necessary to navigate the complex landscape of vulnerability management. Our resources, such as the VulnCheck KEV and Exploit & Vulnerability Intelligence, empower security practitioners to prioritize and remediate vulnerabilities effectively.
About VulnCheck
VulnCheck is helping organizations not just to solve the vulnerability prioritization challenge - we’re working to help equip any product manager, CSIRT/PSIRT or SecOps team and Threat Hunting team to get faster and more accurate with infinite efficiency using VulnCheck solutions.
We knew that we needed better data, faster across the board, in our industry. So that’s what we deliver to the market. We’re going to continue to deliver key insights on vulnerability management, exploitation and major trends we can extrapolate from our dataset to continuously support practitioners.
Are you interested in learning more? If so, VulnCheck's Exploit & Vulnerability Intelligence has broad threat actor coverage. Register and demo our data today.