In this series, we explore vulnerability disclosure and exploitation, drawing insights from VulnCheck’s Exploit and Vulnerability Intelligence services. VulnCheck leverages automated and scalable processes to collect and analyze data from various sources, providing a comprehensive overview of the threat landscape. Our goal in this article is to provide valuable perspectives for the security community focused on what we can observe from trends in vulnerability disclosure, exploitation, weaponization, and exploit availability during the first half of 2024 (Jan-June).
Previously we provided insights on the last decade of vulnerability exploitation here.
A look into 1H-2024 Vulnerability Exploitation
Overview
In the first half of 2024, we observed consistent public disclosure of exploitation in the wild from product companies, security firms, researchers, government agencies, and the broader security community. These disclosures provide defenders with crucial visibility into threats to their environments, allowing for timely action. It’s common for security teams to use this knowledge for vulnerability prioritization and security product teams to use this shared knowledge to prioritize building detection capabilities among many other purposes. We strongly advocate for the public disclosure of exploitation, as it highlights real threats posed to organizations that can be addressed. It is clear that the exploitation of vulnerabilities remains a persistent threat to organizations as the 2024 Verizon DBIR highlighted earlier this year.
Key Findings
Known Exploited Vulnerability Trends
- VulnCheck added 390 vulnerabilities to VulnCheck Known Exploited Vulnerabilities (KEV) Catalog that we identified for the first time as being exploited in the wild in 2024, compared with 73 exploited vulnerabilities captured by CISA KEV.
- The Known Exploited Vulnerabilities span across 235 software suppliers across 310 products and services.
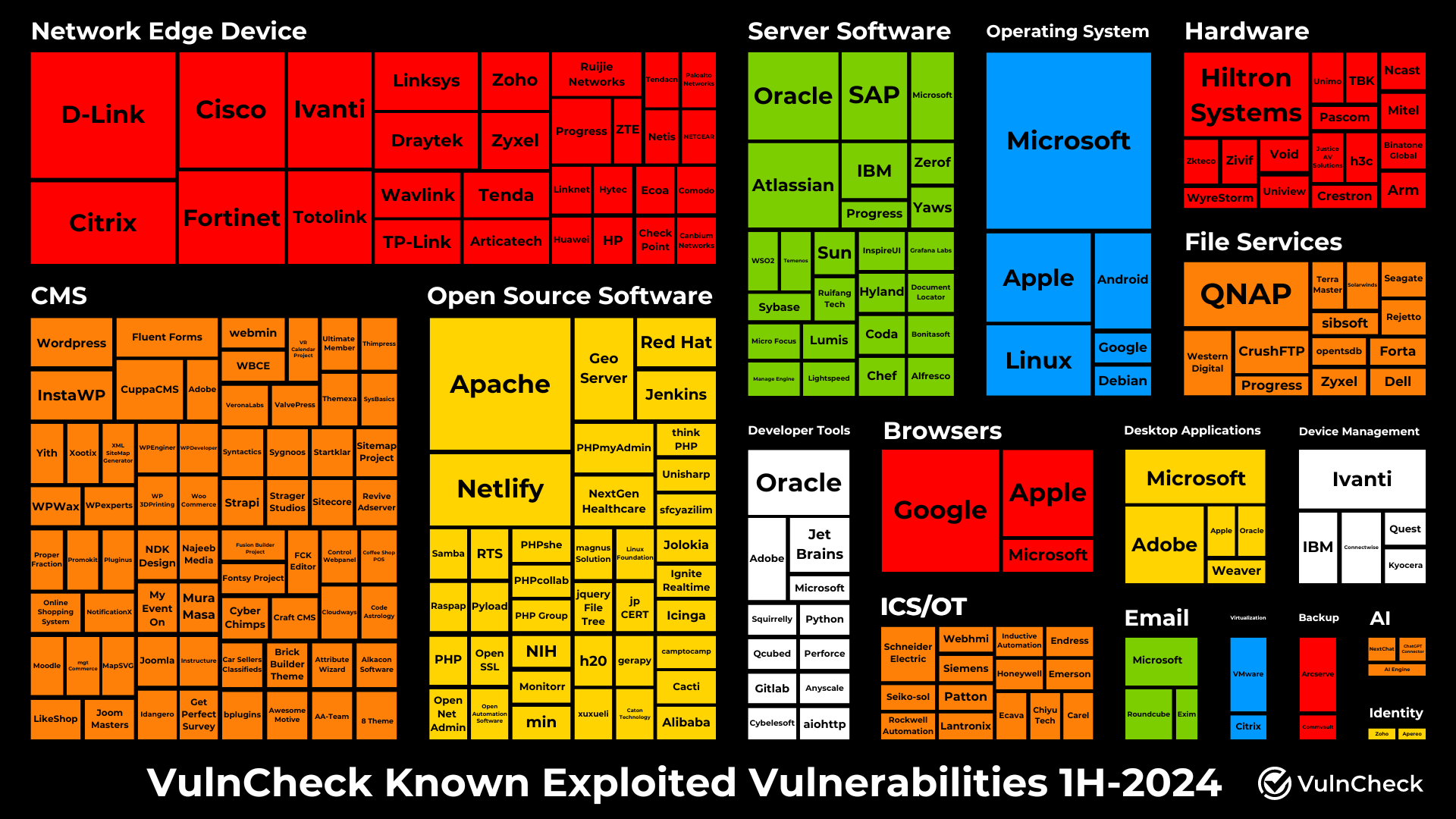
- The top five Product Categories with known exploited vulnerabilities include: Network Edge Devices, Content Management Systems (CMS), Open Source Software, Server Software, and Operating Systems
- 68 different sources provided the earliest reported exploitation of one or more vulnerabilities in the wild in the first half of 2024.
Zero-day, Botnet and Exploit Trends
- In the first half of 2024, we captured evidence of 53 zero-day vulnerabilities, with exploitation evidence available at or before the public disclosure of the vulnerabilities. This represents 13.6% 2 of the Known Exploited Vulnerabilities (KEVs) added to the VulnCheck KEV catalog during this period.
- During the first half of 2024, we observed 92 vulnerabilities being weaponized for the first time, with 50 confirmed as exploited in the wild. Of these 50 vulnerabilities, 58% (29/50) were weaponized before their exploitation was disclosed.
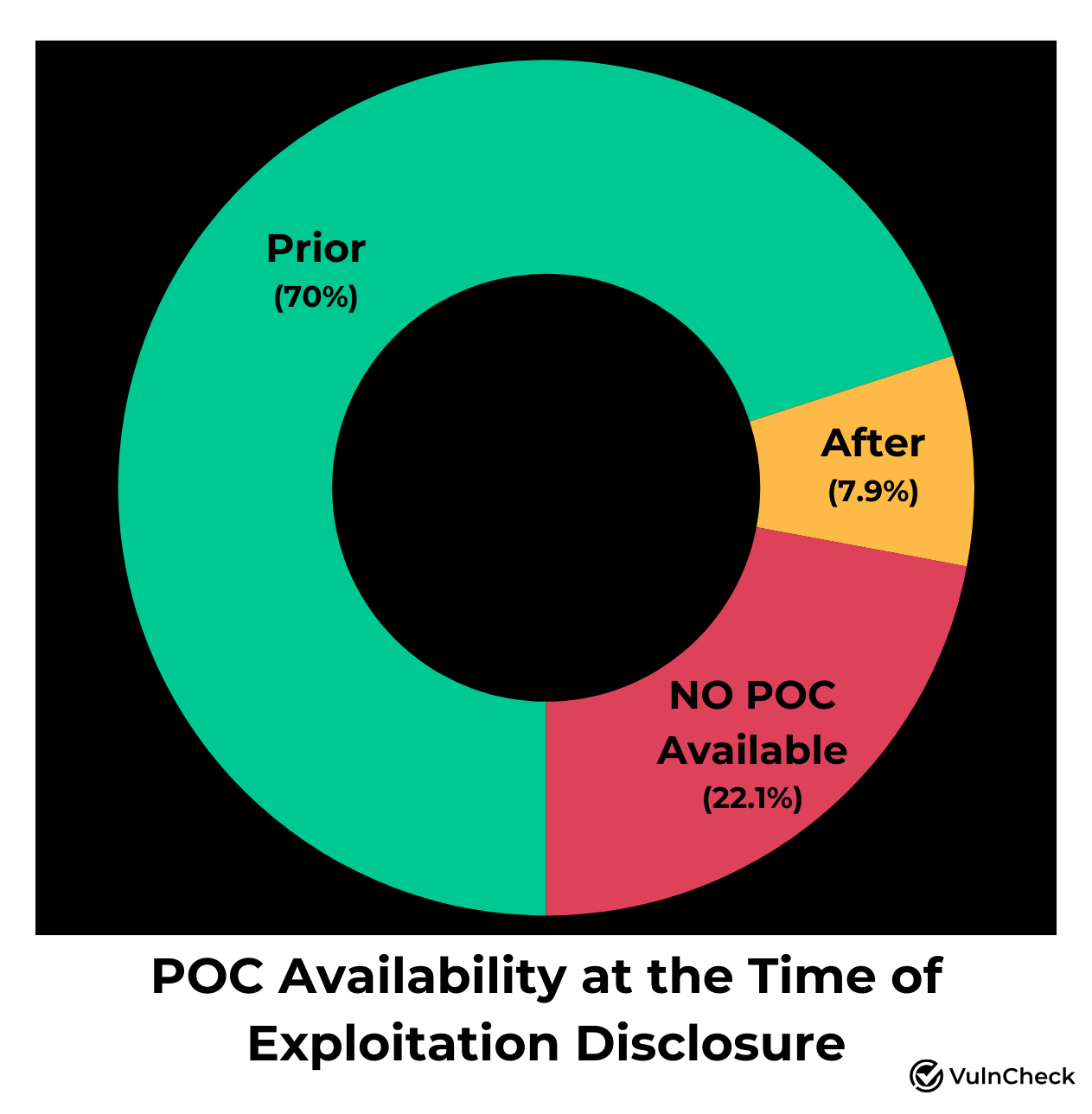
- 70% of vulnerabilities had one or more POC available prior to exploitation disclosure.
Known Exploited Vulnerabilities
During the 1H-2024, VulnCheck added 390 vulnerabilities to VulnCheck Known Exploited Vulnerabilities (KEV) Catalog that were identified for the first time as being exploited in the wild in 2024 compared with 73 exploited vulnerabilities captured by CISA KEV. 1

The 390 KEVs added to VulnCheck, covered 235 software suppliers across 310 products and services. Software suppliers topping the list include Microsoft, Apple, Ivanti, Google, Oracle, D-Link, Apache, Adobe and Hiltron Systems. Products topping the list include Microsoft Windows, Apple OS/IOS/Safari, Netlify OpenMetadata, Citrix Netscaler, Linux Kernel, Hiltron DVR, Ivanti Connect Secure and Google Chrome.
Product Categories for Known Exploited Vulnerabilities
For the first time, we categorized the 1H-2024 KEVs to better understand which product categories are most impacted by known exploited vulnerabilities. This categorization helps security practitioners identify the product categories most commonly associated with new known exploitation. This information is particularly useful in thinking about how an organization might consider reducing their attack surface and automating vulnerability management and patch management processes across their technology stack. We plan to explore several of these categories further the future.
For this report, we categorized the 1H-2024 Known Exploited Vulnerabilities into 18 product categories:
| Category | # of Exploited Vulnerabilities |
|---|---|
| Network Edge Device | 70 |
| CMS | 70 |
| Open Source Software | 56 |
| Server Software | 35 |
| Operating System | 29 |
| Hardware | 21 |
| File Sharing | 19 |
| Developer Tools | 17 |
| Browser | 16 |
| ICS/OT | 15 |
| Desktop Application | 12 |
| Device Management | 9 |
| 6 | |
| Virtualization | 4 |
| Backup | 4 |
| AI | 3 |
| Security Tools | 2 |
| Identity | 2 |
The main objective of categorizing these vulnerabilities is to provide greater visibility into new exploitation evidence, helping to ensure that security practitioners monitor the most at-risk product categories for new exploited vulnerabilities. Note that some products could be associated with multiple categories; however, for this visualization, we focused on using a single primary category for each product.
First Source to Disclose Known Exploitation

For the 390 vulnerabilities first identified in the first half of 2024, VulnCheck collected 10,611 references of exploitation in the wild. From hundreds of reputable sources, we identified 68 different sources that were the earliest reporters of exploitation during this period. The chart above demonstrates the number of unique exploited vulnerabilities reported first by a source. 2
Evidence of vulnerability exploitation is broadly distributed across many sources, which is one reason we focus on automated and scalable processes at VulnCheck. Coordinated disclosure or copy/paste practices often create discrepancies in who reported exploitation first. Particularly in the cases of CISA, Microsoft, Google, Google Project Zero, and Apple who consistently disclose exploitation evidence at roughly the same time, contributing to these discrepancies.This is a good thing as it demonstrates the proliferation of exploitation evidence.
Top Vulnerabilities by the number of sources reporting known exploitation
The number of unique references reporting known exploitation is often a good indicator for widely exploited vulnerabilities. The top 10 vulnerabilities by the number of unique sources referencing exploitation in the first half of 2024 include:
| Vulnerability | Vendor | Product | # of References |
|---|---|---|---|
| CVE-2024-21887 | Ivanti | Connect Secure and Policy Secure | 51 |
| CVE-2023-46805 | Ivanti | Connect Secure and Policy Secure | 47 |
| CVE-2024-1709 | ConnectWise | ScreenConnect | 29 |
| CVE-2024-3400 | Palo Alto Networks | PAN-OS | 22 |
| CVE-2024-21893 | Ivanti | Connect Secure, Policy Secure, and Neurons | 20 |
| CVE-2024-1708 | ConnectWise | ScreenConnect | 19 |
| CVE-2024-27198 | JetBrains | TeamCity | 18 |
| CVE-2023-22527 | Atlassian | Confluence Server and Data Center | 18 |
| CVE-2024-21412 | Microsoft | Windows | 11 |
| CVE-2024-4577 | PHP Group | PHP | 11 |
Exploring CISA KEV
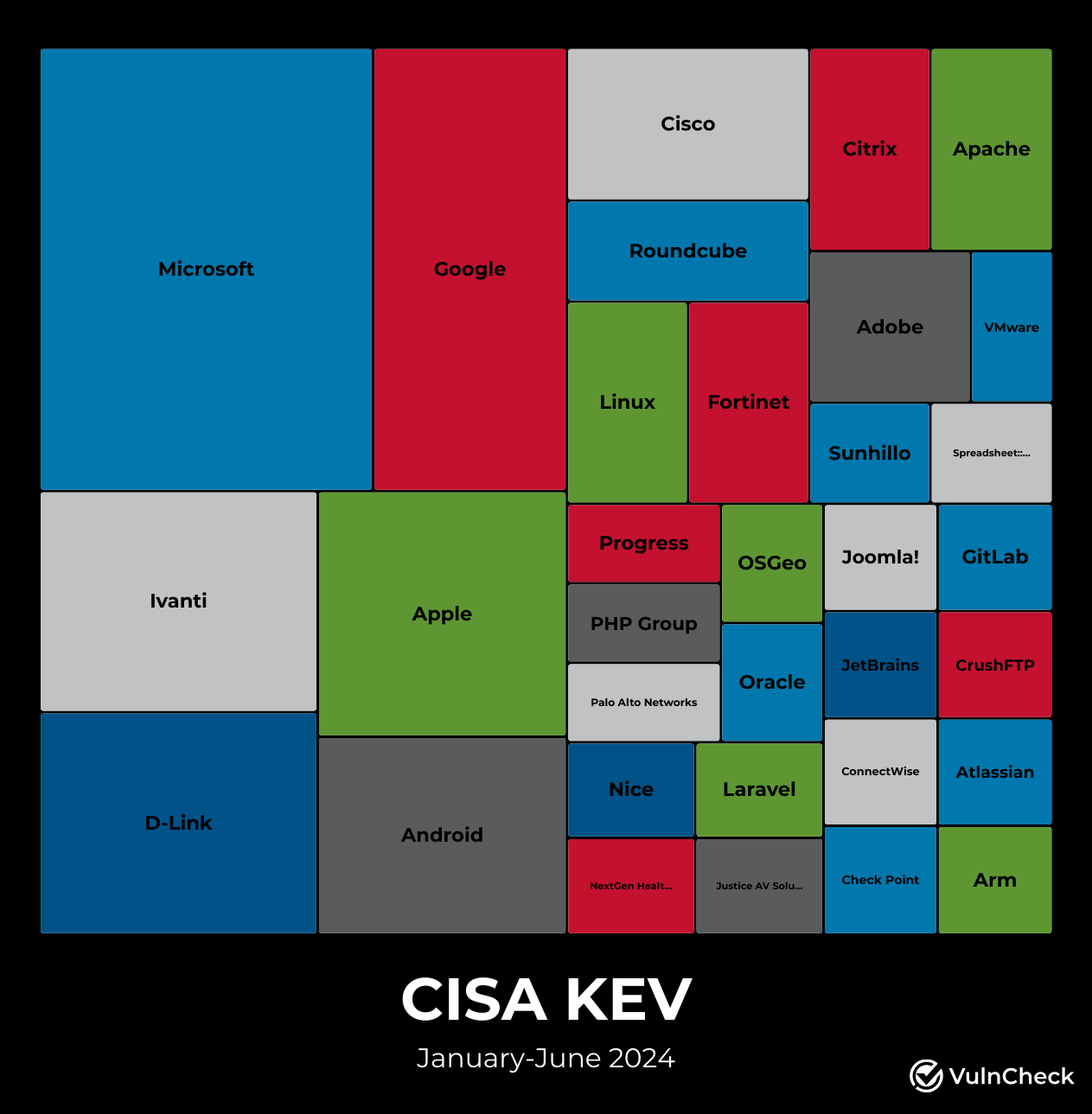
During the first half of 2024, CISA added 73 vulnerabilities to the CISA KEV catalog, covering 33 software suppliers. Of these, 53 vulnerabilities had exploitation evidence captured in the VulnCheck KEV catalog before they were added to CISA KEV. Many of these were also disclosed by the vendor on the same day. Additionally, 16 of the 53 vulnerabilities had exploitation evidence dating back to before 2024. As shown in the visual above, CISA KEV has primarily focused on widely adopted technologies, including internet-facing technologies, operating systems, and client-side software.
Zero Days
The term "zero-day" is often used in various ways across the security industry. For this research, we define a zero-day simply as a vulnerability for which evidence of exploitation in the wild is published on or before the vulnerability itself is publicly disclosed.
In the first half of 2024, we captured evidence of 53 zero-day vulnerabilities, with exploitation evidence available at or before the public disclosure of the vulnerabilities. This represents 13.6% 3 of the Known Exploited Vulnerabilities (KEVs) added to the VulnCheck KEV catalog. In comparison, 130 zero-days were identified in 2023 which could mean we might see less in total during 2024. This could be due to multiple factors such as improvements in vulnerability disclosure timelines. Defenders should expect a relatively consistent number of zero-days, many of which are high-impact vulnerabilities affecting internet-facing network devices, web services, operating systems, and browsers. Google's Zero Day Trends Report observed 97 zero-day vulnerabilities exploited in the wild, providing a comparative data point.
Comparing Zero-days with CISA KEV
Notably, 33 of the 53 zero-days VulnCheck captured in the first half of 2024 were also added to the CISA KEV catalog, representing 45% of CISA KEV additions for 2024. These zero-days often involve major government suppliers such as Microsoft, Google, Apple, Citrix, Fortinet, Palo Alto Networks, Cisco, and CheckPoint, which typically disclose exploitation at the time of patch release and CVE issuance. It would be great to see more technology vendors disclosing when they have knowledge of exploitation.
Ransomware & Botnets, Oh my!
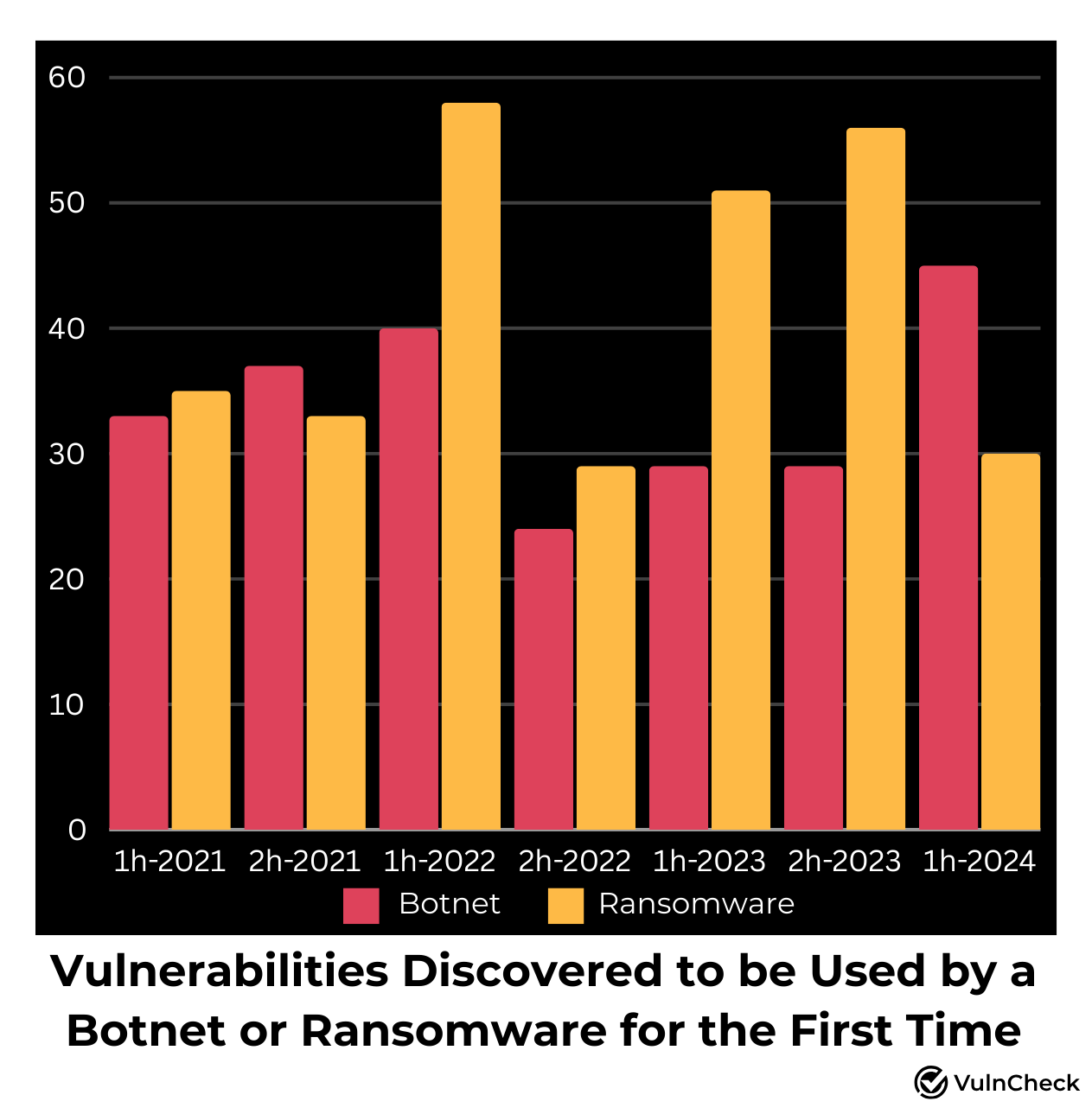
Botnets and ransomware pose a significant risk to organizations due to their use of automated attack techniques that opportunistically target victims. During the first half of 2024, VulnCheck captured evidence of vulnerabilities being associated with ransomware and botnets for the first time. This included 30 vulnerabilities linked to ransomware and 46 vulnerabilities linked to botnets.
Weaponization & Proof-of-Concept Availability Associated w/ KEVs
During the first half of 2024, we observed 92 vulnerabilities being weaponized for the first time, with 50 confirmed as exploited in the wild. Of these 50 vulnerabilities, 58% (29/50) were weaponized before their exploitation was disclosed.
Regarding Proof-of-Concept (PoC) availability, 304 of the 390 Known Exploited Vulnerabilities (KEVs) had one or more PoCs available when this report was compiled. Among these, 273 (70%) had PoCs available prior to the disclosure of exploitation. It’s also worth considering the 53 zero-days, where POC or weaponization of a vulnerability is rare prior to disclosure. This underscores Weaponization and PoC availability as a reliable indicator that a vulnerability is more likely to be exploited in the wild.
Evidence of weaponization and POC vulnerabilities is useful when building out evidence-based prioritization using a framework such as Stakeholder-Specific Vulnerability Categorization. We initially explored weaponization and PoC availability in our recent state of exploitation article.
Considerations For This Report
[1] We continue to expand historical exploitation evidence for hundreds of CVEs from previous years in addition to the new evidence collected. From the time we cut off the data for this report which was July 22, 2024 to the time of publish, we added over 100 new KEVs from multiple sources. Our priority remains in provideing broad and timely access to exploit intelligence.
[2] There is a bias towards Shadow Server during the 1h-2024 as we onboarded the source in November which has trailed into January and February of this year. We expect Shadow Server to continue to be one of the leading sources to be the first to report known exploitation but it’s likely their representation will be smaller during future periods.
[3] Analyzing past years' data, we observed that zero-days comprised 25% of all Known Exploited Vulnerabilities as we noted in our previous report which looked at 2014 to 2023. The lower percentage observed in the first half of 2024 is likely due to the short-term impact of onboarding ShadowServer as a new source of exploitation evidence.
About VulnCheck
VulnCheck is helping organizations not just to solve the vulnerability prioritization challenge - we’re working to help equip any product manager, CSIRT/PSIRT or SecOps team and Threat Hunting team to get faster and more accurate with infinite efficiency using VulnCheck solutions.
We knew that we needed better data, faster across the board, in our industry. So that’s what we deliver to the market. We’re going to continue to deliver key insights on vulnerability management, exploitation and major trends we can extrapolate from our dataset to continuously support practitioners.
Are you interested in learning more? If so, VulnCheck's Exploit & Vulnerability Intelligence has broad threat actor coverage. Register and demo our data today.