In September, VulnCheck identified evidence of 78 CVEs that were publicly disclosed for the first time as exploited in the wild. The disclosure of known exploited vulnerabilities was from 21 different sources including a detailed flax typhoon botnet report from the five eyes agencies which we covered in detail last month.
Key Takeaways
- In September, VulnCheck identified 78 CVEs that were publicly disclosed for the first time as exploited in the wild
- Software / Product Categories that topped the list included Network Edge Devices, Open Source Software, Server Software and Desktop Applications.
- 29.5% of September’s KEVs had exploitation evidence within one month of their CVE publication date, while 53.9% were exploited within a year.
- As of October 9th, 9 of the 78 Known Exploited Vulnerabilities are still awaiting analysis by NIST NVD.
September Product Categories and Vendors
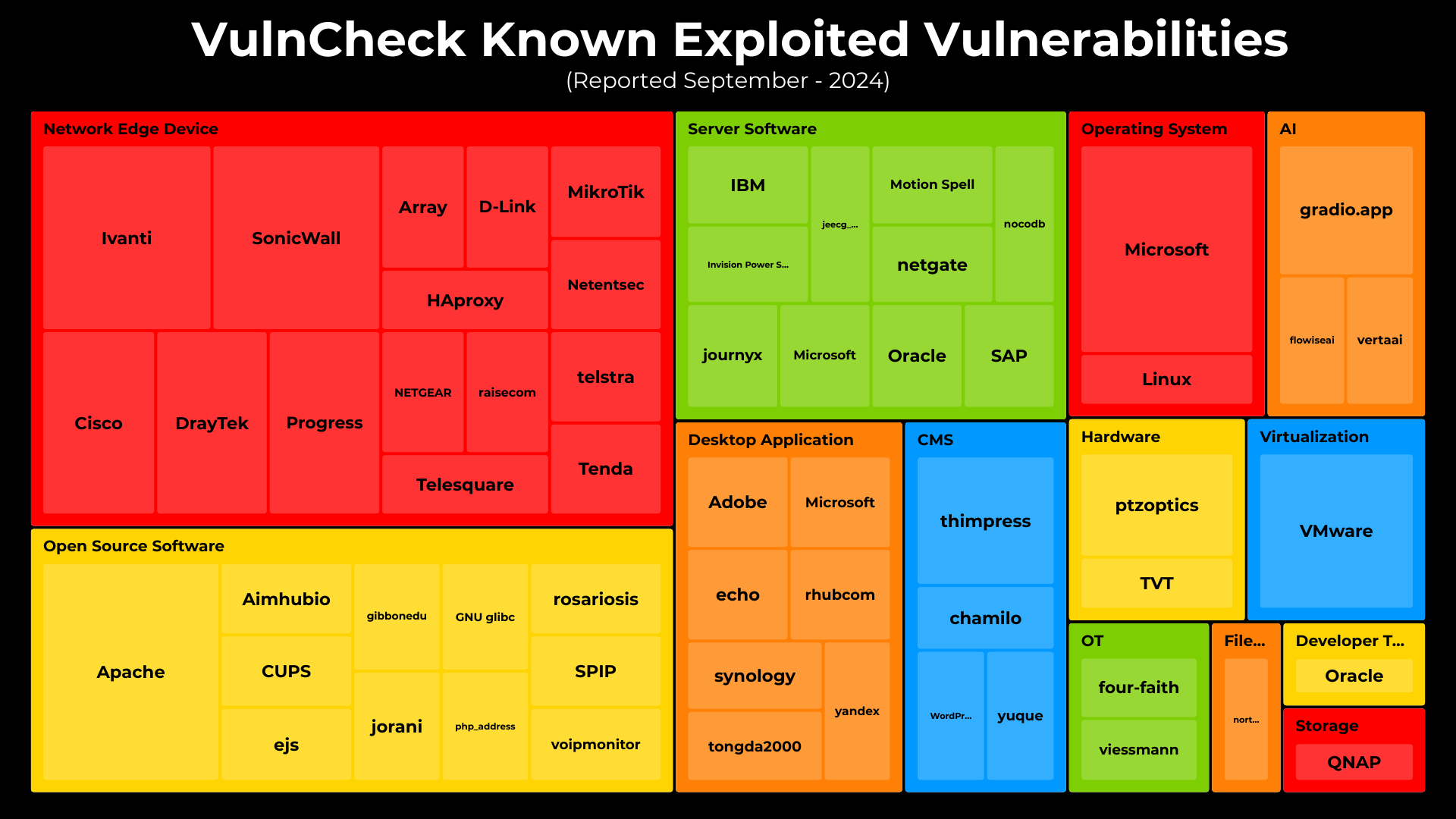
In September, I explored the product categories and vendors associated with known exploitation disclosed during the month. The top targeted categories were Network Edge Devices (28.2%), Open Source Software (16.7%), and Service Software (12.8%).
Network Edge Devices, consistently targeted by threat actors, highlight the importance of maintaining timely patch management processes, especially for internet-facing devices like network routers, modems and firewalls.
Who Reported Known Exploited Vulnerabilities
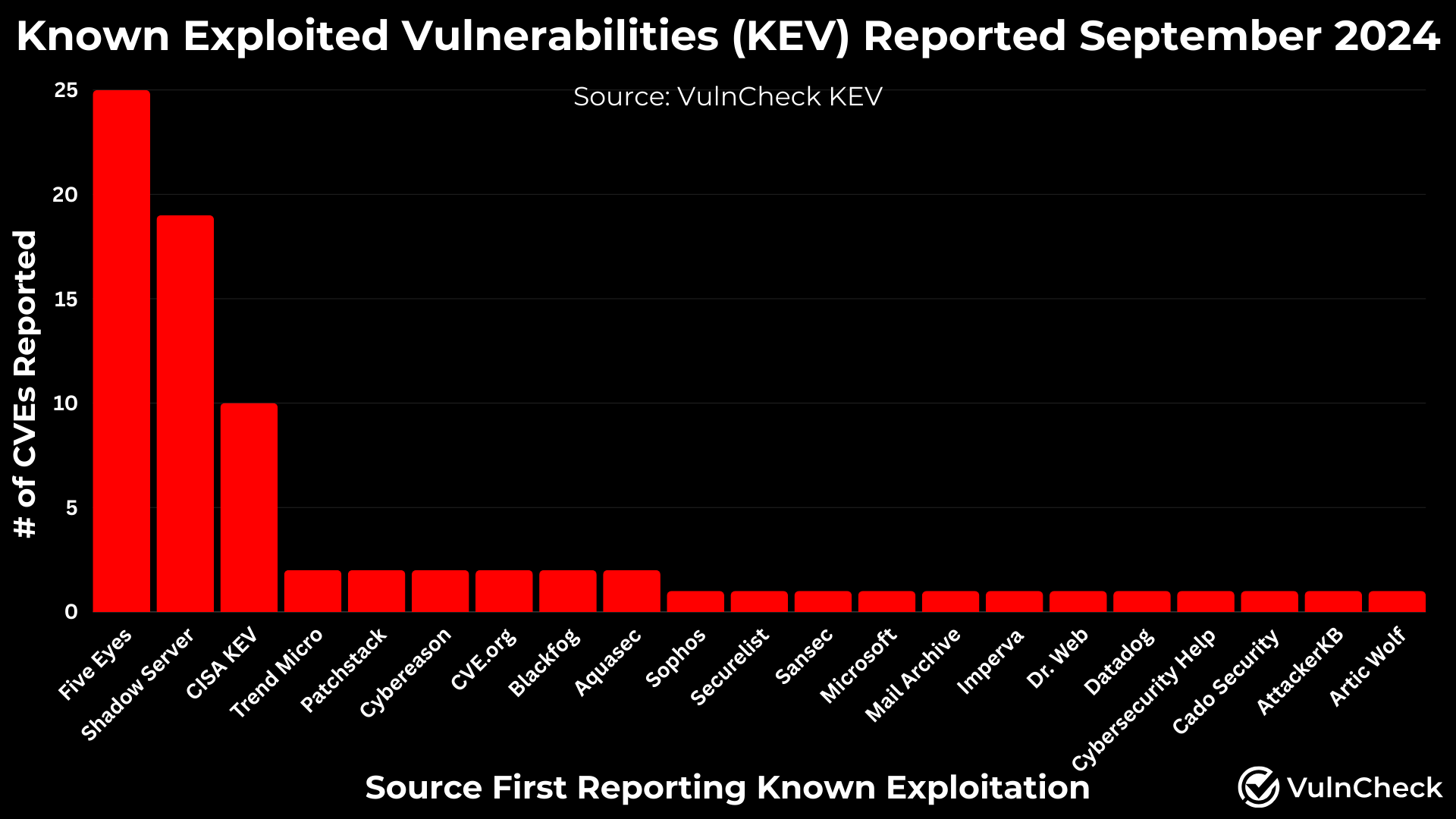
In September, 21 different sources disclosed known exploited vulnerabilities (KEVs). Notably, the Five Eyes agencies released a detailed report on the Flax Typhoon botnet, uncovering exploitation evidence for 25 CVEs that previously lacked public reports of exploitation.
Shadowserver has shown a noticeable increase in disclosed exploitation activity. Additionally, CISA KEV added four older vulnerabilities in September from Draytek, Oracle (2), and SAP, marking the first public exploitation evidence for these products.
Time to Publicly Reported Exploitation
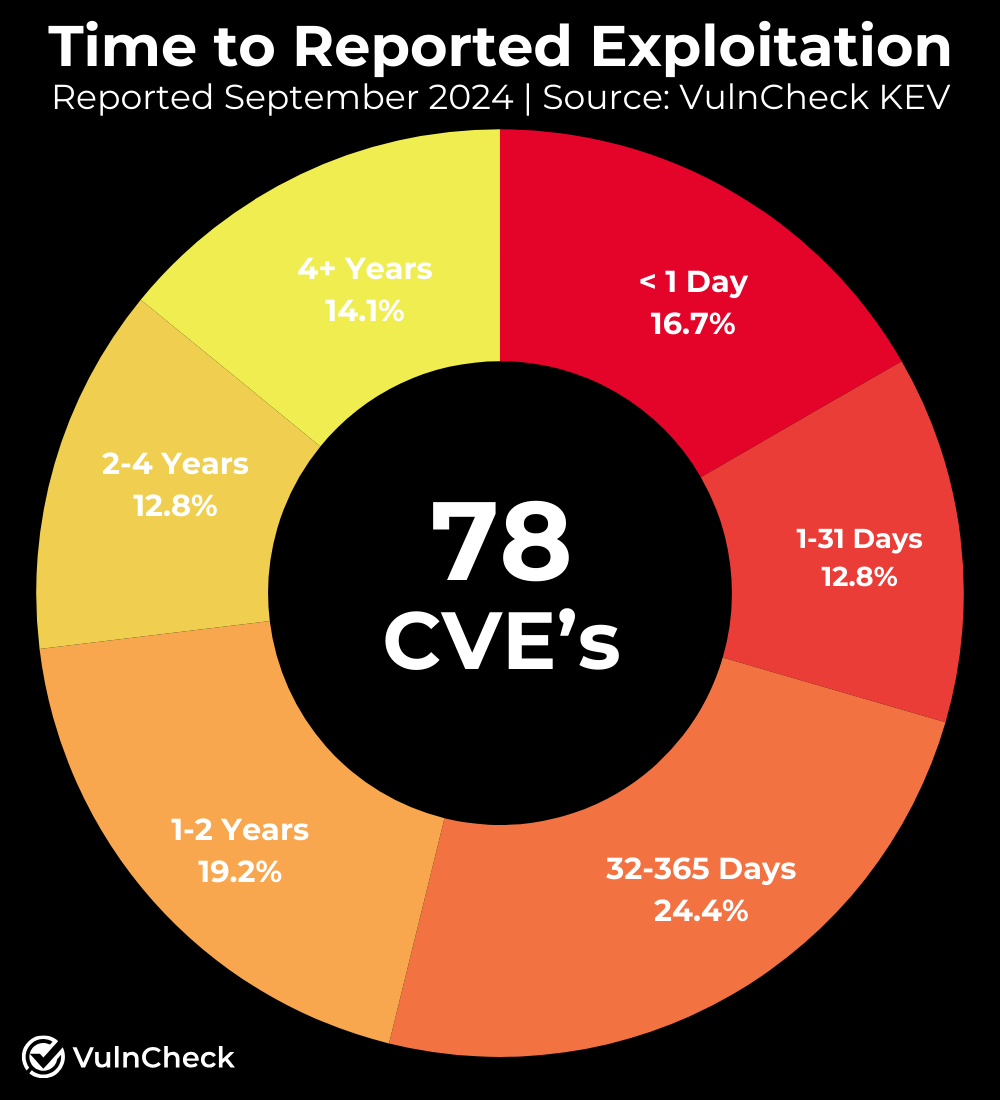
A common question is: How quickly are known vulnerabilities exploited? To explore this, we analyzed 78 known exploited vulnerabilities (KEVs), comparing the time between their NVD publication and public reports of exploitation.
Our findings show that 29.5% of September’s KEVs had exploitation evidence within one month of their CVE publication, while 53.9% were exploited within a year. We plan to expand this research to cover a broader set of KEVs for deeper insights in the future on time to exploitation.
A look at September’s Known Exploited Vulnerabilities Mapped to Scoring System
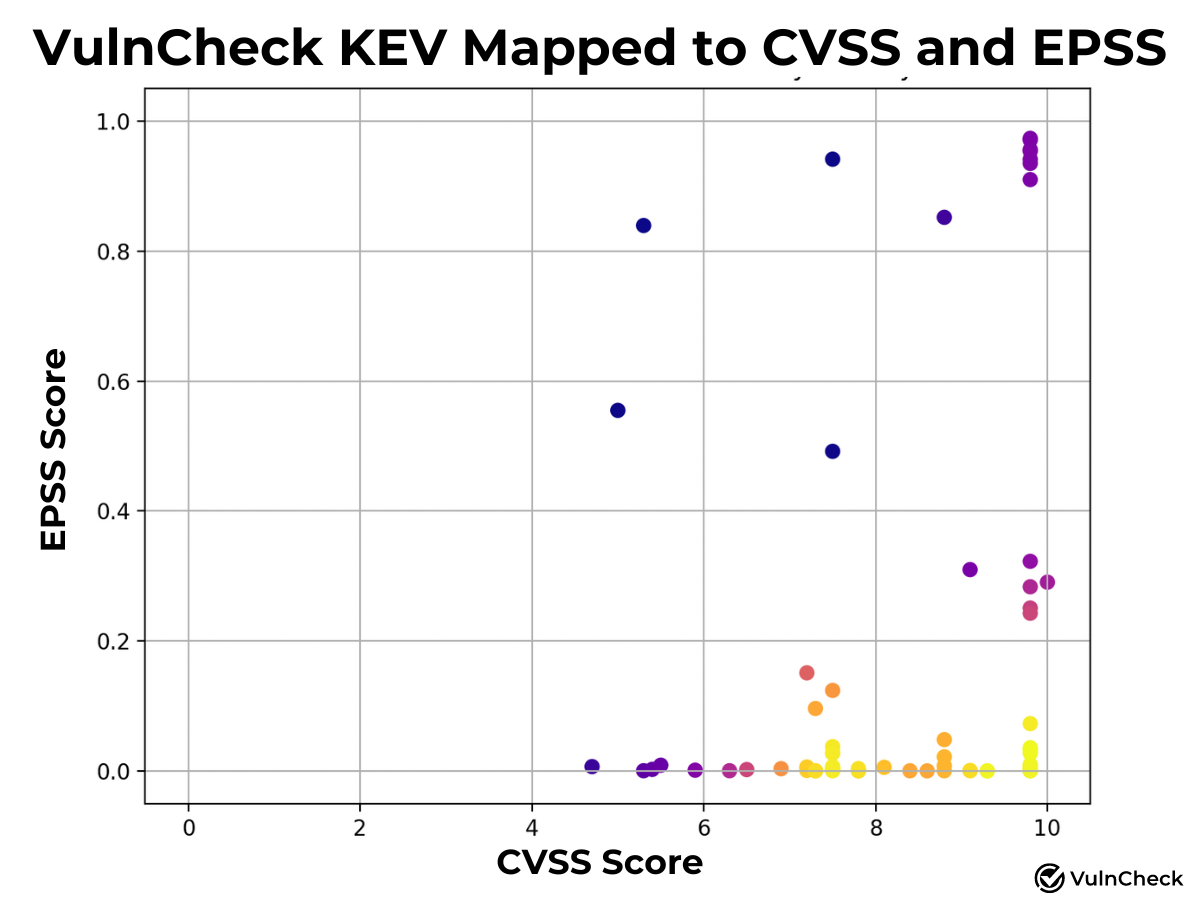
We've continued to analyze Known Exploitation in relation to vulnerability scoring systems, specifically CVSS and EPSS. Our goal is to provide insights into how these scoring systems can better reflect known exploitation and emerging threats. To enhance visibility into CVSS and EPSS, I created a plot of known exploitation mapped to these systems. Yellow indicates higher density, while purple represents lower density of CVEs associated with known exploitation. By applying an EPSS score (Early October scoring) of 0.1 or a 10% probability of exploitation or higher, we find that 20 CVEs (25.6%) align with Known Exploitation captured for the first time during June, July and August. With a CVSS-BT score of 9 or higher, 36 CVEs (46.1%) map to Known Exploitation. We plan to explore scoring systems further to provide deeper insights when we have more time.
Related to the topic of vulnerability prioritization, we suggest exploring: Taking an Evidence Based Approach to Prioritization.
Access VulnCheck Known Exploited Vulnerabilities (KEV) Catalog
For those eager to dive deeper into known exploited vulnerabilities, you can start by utilizing VulnCheck Community a free resource including VulnCheck KEV and VulnCheck NVD++.
About VulnCheck
VulnCheck is helping organizations not just to solve the vulnerability prioritization challenge - we’re working to help equip any product manager, CSIRT/PSIRT or SecOps team and Threat Hunting team to get faster and more accurate with infinite efficiency using VulnCheck solutions.
We knew that we needed better data, faster across the board, in our industry. So that’s what we deliver to the market. We’re going to continue to deliver key insights on vulnerability management, exploitation and major trends we can extrapolate from our dataset to continuously support practitioners.
Are you interested in learning more? If so, VulnCheck's Exploit & Vulnerability Intelligence has broad threat actor coverage. Register and demo our data today.