Last week, Five Eyes agencies issued a Joint Cybersecurity Advisory titled, “People’s Republic of China-Linked Actors Compromise Routers and IoT Devices for Botnet Operations”. The report was authored across multiple agencies including the FBI, US Cyber Command, NSA, Australian Signals Directorate, ACSC, NCSC of New Zealand, Canada, and NCSC UK.
The advisory, issued by Five Eyes agencies’, introduces new intelligence, including indicators of compromise, exploited CVEs, and the geographical location of impacted devices. Below, we highlight key details from the report to help raise awareness about this Flax Typhoon botnet.
Key Takeaways from the Joint Cybersecurity Advisory
- 66 vulnerabilities are actively being exploited by Flax Typhoon's Botnet
- The Flax Typhoon Botnet primarily targets routers, IoT devices, and other web-facing applications.
- 47.9% of devices associated with the Flax Typhoon Botnet are located in the United States.
- Prior to this advisory, VulnCheck KEV included 41 of the 66 CVEs and has since been updated to include all 66 vulnerabilities. At the time of publication, CISA KEV included 27 of the 66 CVEs.
Technologies Targeted by Flax Typhoon Botnet
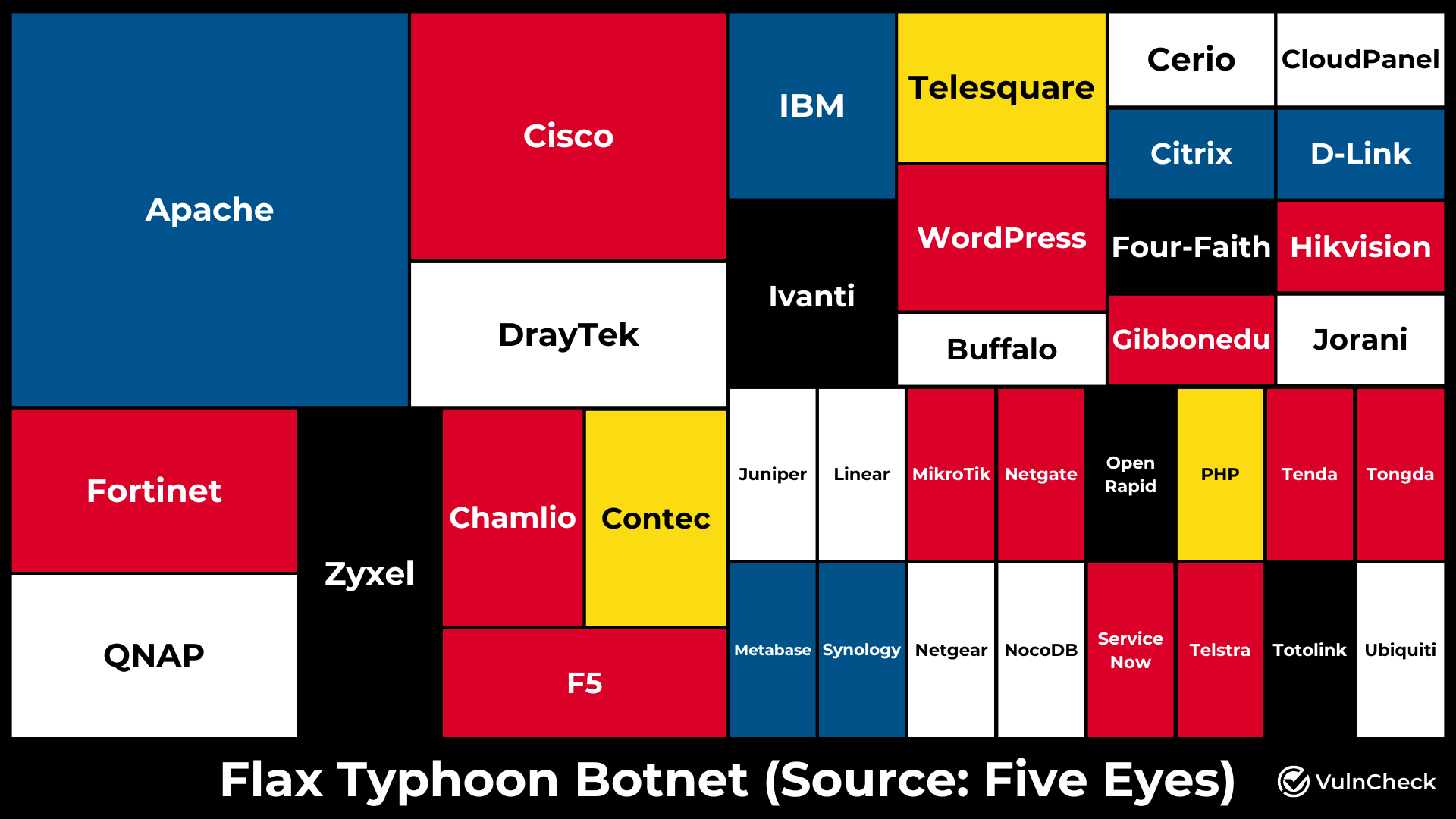
The joint advisory lists 66 vulnerabilities actively exploited to target routers, IoT devices and other web facing applications. The most affected software suppliers associated with the botnet include:
- Apache (10 CVEs)
- Cisco (5 CVEs)
- Zyxel (3 CVEs)
- QNAP (3 CVEs)
- Fortinet (3 CVEs)
- Draytek (3 CVEs)
- WordPress (2 CVEs)
- Telesquare (2 CVEs)
- Ivanti (2 CVEs)
- IBM (2 CVEs)
- F5 (2 CVEs)
- Contec (2 CVEs)
- Chamilo (2 CVEs)
Odds are you have some of these technologies in your environment, making it crucial to address these vulnerabilities.
Countries Targeted by Flax Typhoon Botnet

Analysis of devices associated with the Flax Typhoon Botnet shows that 47.9% of the devices are located in the United States, indicating a likely focus and foothold on US critical infrastructure. Other notable targets include Vietnam (8% of devices) and Germany(7.2% of devices). It appears the botnet is largely targeting North American, European and Asian countries.
| Country | Node Count | Percentage |
|---|---|---|
| United States | 126,000 | 47.90% |
| Vietnam | 21,100 | 8.00% |
| Germany | 18,900 | 7.20% |
| Romania | 9,600 | 3.70% |
| Hong Kong | 9,400 | 3.60% |
| Canada | 9,200 | 3.50% |
| South Africa | 9,000 | 3.40% |
| United Kingdom | 8,500 | 3.20% |
| India | 5,800 | 2.20% |
| France | 5,600 | 2.10% |
| Bangladesh | 4,100 | 1.60% |
| Italy | 4,000 | 1.50% |
| Lithuania | 3,300 | 1.30% |
| Albania | 2,800 | 1.10% |
| Netherlands | 2,700 | 1.00% |
| China | 2,600 | 1.00% |
| Australia | 2,400 | 0.90% |
| Poland | 2,100 | 0.80% |
| Spain | 2,000 | 0.80% |
Vulnerabilities Targeted by Flax Typhoon Botnet
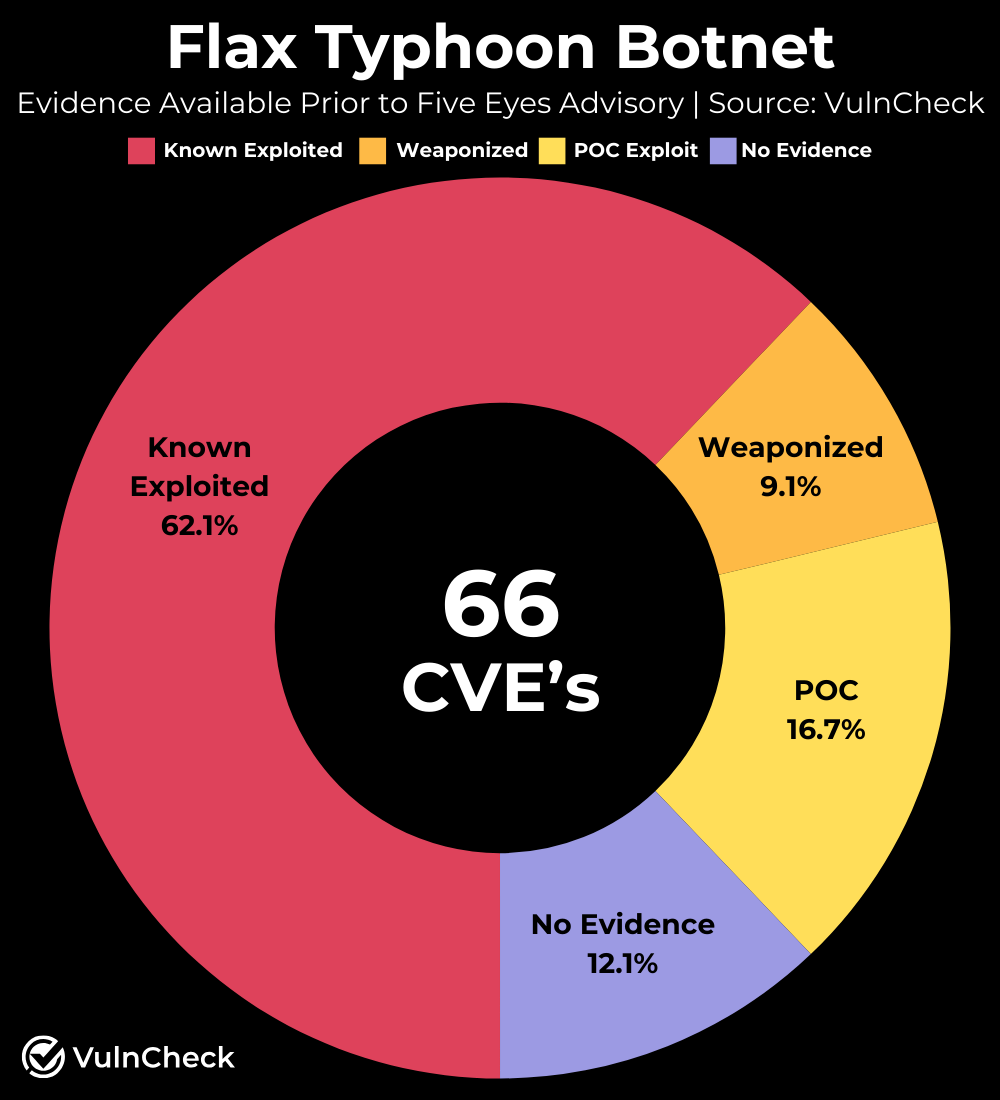
The Flax Typhoon Botnet exploits 66 vulnerabilities. Of these, 41 were known to VulnCheck before the advisory was published and available in VulnCheck KEV, a free community resource. Interestingly, only 27 of these vulnerabilities are listed in CISA's Known Exploited Vulnerabilities (KEV) catalog. VulnCheck has since updated its own KEV resource to include all 66 vulnerabilities, and we expect CISA is likely to follow suit in the coming days/weeks/months.
Prior to this advisory, VulnCheck already had strong coverage. Besides the 41 known exploited vulnerabilities, 6 additional vulnerabilities were known to be weaponized (71.2%). Of the remaining vulnerabilities, 11 have proof-of-concept (PoC) exploit code, while 8 had no available exploit evidence prior to this advisory (12.1%).
Recommended Mitigations from the FBI
The FBI recommends several actions to mitigate threats posed by botnets like Flax Typhoon. These actions apply both to preventing IoT devices from becoming part of a botnet and to defending networks from already active botnets:
- Disable unused services and ports
- Implement network segmentation
- Monitor for high network traffic volume
- Apply patches and updates
- Replace default passwords with strong passwords
- Plan for device reboots
- Replace end-of-life equipment
Taking an Evidence-Based Approach to Vulnerability Prioritization
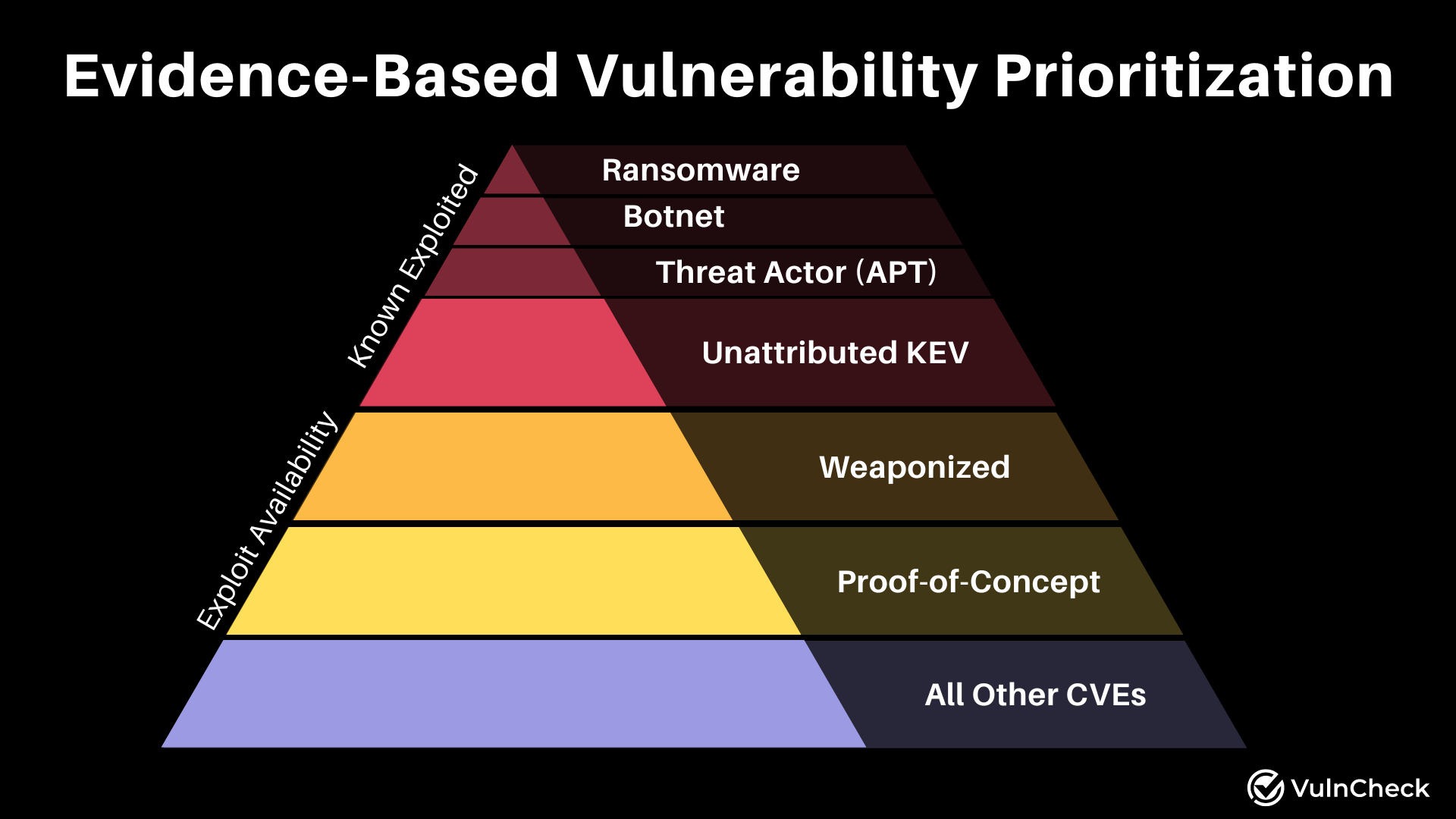
Prioritizing vulnerabilities effectively requires a comprehensive approach that integrates exploit evidence, environmental context, and additional risk factors. By utilizing threat intelligence and vulnerability attributes, organizations can make informed decisions in prioritizing vulnerabilities and reducing an organization's overall risk. At VulnCheck, we provide the tools and intelligence necessary to navigate the complex landscape of vulnerability management. Our resources, such as the VulnCheck KEV and Exploit & Vulnerability Intelligence, empower security practitioners to prioritize and remediate vulnerabilities effectively.
About VulnCheck
VulnCheck is helping organizations not just to solve the vulnerability prioritization challenge - we’re working to help equip any product manager, CSIRT/PSIRT or SecOps team and Threat Hunting team to get faster and more accurate with infinite efficiency using VulnCheck solutions.
We knew that we needed better data, faster across the board, in our industry. So that’s what we deliver to the market. We’re going to continue to deliver key insights on vulnerability management, exploitation and major trends we can extrapolate from our dataset to continuously support practitioners.
Are you interested in learning more? If so, VulnCheck's Exploit & Vulnerability Intelligence has broad threat actor coverage. Register and demo our data today.