VulnCheck Initial Access Intelligence equips organizations and security teams with detection artifacts including Suricata signatures, YARA rules, PCAPs, and private exploit PoCs to defend against initial access vulnerabilities that are either already being exploited or likely to be exploited soon.
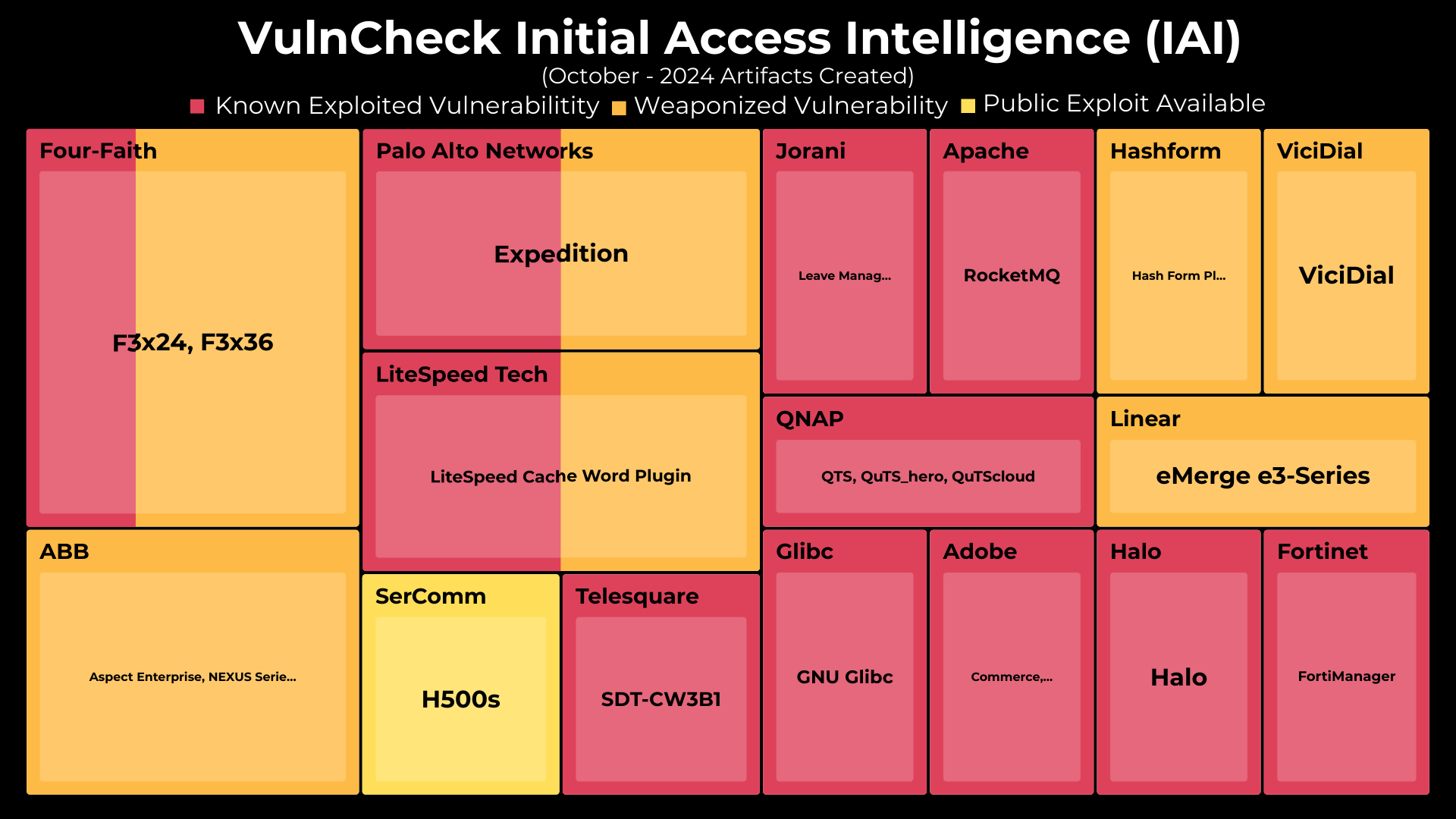
In October 2024, VulnCheck crossed 300+ CVEs that have Initial Access Intelligence (IAI) artifacts, developing artifacts for 21 CVEs, covering 16 different vendors and products. 11 of the 22 have confirmed exploitation activity as of November 10th, 2024.
Expanded Coverage of the Flax Typhoon Botnet
We've continued to expand detection coverage for CVE's which were discovered to be a target of the recently reported Flax Typhoon Botnet. This month additional CVE's we've added coverage for include: CVE-2023-26469 (Jorani - LMS), CVE-2023-47218 (QNAP - QTS, QuTS_hero, QuTScloud), CVE-2023-37582 (Apache - RocketMQ), CVE-2019-12168 (Four-Faith - F3x24, F3x36), and CVE-2021-46422 (Telesquare - SDT-CW3B1). VulnCheck now boasts detection coverage for 37 of the 66 CVEs associated with the Flax Typhoon Botnet.
Detection Artifacts for ABB Cyclon ASPECT Industrial Control Systems
During October, we released an initial access artifacts for ABB Cyclon ASPECT CVE-2023-0636 & CVE-2024-6209 including a blog post and video walkthrough from Jacob Baines exploring the ABB systems exploits and internet connected systems to see what’s accessible and potentially vulnerable.
Expanded Visibility w/ FOFA & ZoomEye Queries
In October we expanded VulnCheck’s Initial Access query coverage. In addition to providing Shodan, Censys and GreyNoise queries, we have expanded query coverage to now include FOFA & ZoomEye furthering our commitment to helping defenders gain broad visibility into their attack surface.
Initial Access Intelligence - October Breakdown
To provide better visibility into these updates, we’ve broken down October’s Initial Access Intelligence Artifacts by CVE. For each CVE, we provide a range of detection tools including:
- Exploits
- Version scanners
- PCAPs
- Suricata rules
- Snort rules
- YARA rules
- Greynoise/Censys/Shodan/FOFA/ZoomEye Queries
- Target Docker Containers
October 2024 Initial Access Artifacts
| artifactName | Date Added | cve | exploit | versionScanner | pcap | suricataRule | snortRule | yara |
|---|---|---|---|---|---|---|---|---|
| Jorani Log Poisoning RCE | 2024-10-02 | CVE-2023-26469 | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ |
| Linear eMerge e3-Series forgot_password Command Injection | 2024-10-02 | CVE-2024-9441 | ✅ | ✅ | ✅ | ✅ | ||
| QNAP QTS and QuTS hero Unauthenticated Remote Code Execution in quick.cgi | 2024-10-03 | CVE-2023-47218 | ✅ | ✅ | ✅ | ✅ | ✅ | |
| Apache RocketMQ Arbitrary File Write | 2024-10-04 | CVE-2023-37582 | ✅ | ✅ | ✅ | ✅ | ✅ | |
| Hash Form WordPress Plugin Nonce Exposure RCE | 2024-10-07 | CVE-2024-5084 | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ |
| Four-Faith Hidden Creds and OS command execution | 2024-10-09 | CVE-2019-12168 | ✅ | ✅ | ✅ | ✅ | ✅ | |
| Four-Faith Auth Bypass via Hidden API | 2024-10-09 | CVE-2024-9644 | ✅ | ✅ | ✅ | ✅ | ✅ | |
| Four-Faith Hidden Creds and Information Leak | 2024-10-09 | CVE-2024-9643 | ✅ | ✅ | ✅ | ✅ | ✅ | |
| Telesquare SDT-CW3B1 sysCommand RCE | 2024-10-16 | CVE-2021-46422 | ✅ | ✅ | ✅ | |||
| ABB ASPECT System Credential Disclosure | 2024-10-16 | CVE-2024-6209 | ✅ | ✅ | ✅ | ✅ | ✅ | |
| Glibc iconv Buffer Overflow | 2024-10-17 | CVE-2024-2961 | ✅ | |||||
| Magento XXE Glibc iconv Buffer Overflow RCE | 2024-10-17 | CVE-2024-2961 | ✅ | ✅ | ✅ | ✅ | ✅ | |
| ViciDial Blind SQL Credential Leak | 2024-10-17 | CVE-2024-8503 | ✅ | ✅ | ✅ | ✅ | ✅ | |
| ABB ASPECT System networkDiagAjax Command Injection | 2024-10-17 | CVE-2023-0636 | ✅ | ✅ | ✅ | ✅ | ✅ | |
| SerComm CPE Router Authenticated Command Injection | 2024-10-20 | CVE-2021-44080 | ||||||
| LiteSpeed Cache Weak RNG RCE | 2024-10-22 | CVE-2024-28000 | ✅ | ✅ | ✅ | ✅ | ✅ | |
| LiteSpeed Cache Credential Leak | 2024-10-22 | CVE-2024-44000 | ✅ | ✅ | ✅ | ✅ | ✅ | |
| Palo Alto Network Expedition Authentication Bypass | 2024-10-25 | CVE-2024-5910 | ✅ | ✅ | ||||
| Palo Alto Network Expedition Authentication Bypass & Command Injection | 2024-10-25 | CVE-2024-9464 | ✅ | ✅ | ✅ | ✅ | ||
| Fortinet FortiManager Missing Authentication Vulnerability | 2024-10-28 | CVE-2024-47575 | ||||||
| Halo Spring WebFlux Path Traversal | 2024-10-28 | CVE-2024-38816 | ✅ | ✅ | ✅ | ✅ | ✅ |
Go Exploit Framework
In October, we expanded the capabilities of go-exploit to include a new command and control feature called ShellTunnel which captures reverse shell traffic and routes it through an intermediary attacker-controlled server before reaching the main C2 server. https://vulncheck.com/blog/go-exploit-shelltunnel
For those new to go-exploit, VulnCheck's exploit proof of concept (PoC) and version scanner code is written in the Go programming language. They are provided with a Dockerfile for ease of use. The exploits leverage an Open Source Software (OSS) shared library, which VulnCheck has authored and maintains, called go-exploit.
Learn More About VulnCheck Initial Access Intelligence
Learn more about how you can leverage Initial Access Intelligence detection artifacts to detect & respond to remote code execution (RCE) vulnerabilities here: https://docs.vulncheck.com/products/initial-access-intelligence/introduction