Key Takeaways
- Vulnerabilities, CVE-2023-0636 and CVE-2024-6209, impact ABB Cylon ASPECT, a widely used building automation and energy management system.
- CVE-2023-0636 allows command injection, enabling unauthorized remote code execution. While ABB reports authentication is required, testing reveals this is not always enforced.
- CVE-2024-6209 enables unauthenticated file disclosure, allowing attackers to extract plain-text credentials, facilitating further exploits within affected systems.
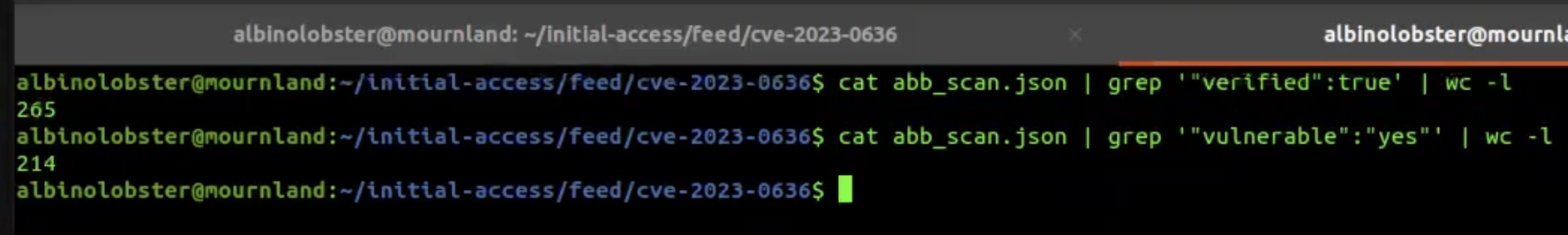
- Our team identified 265 reachable ABB Cylon ASPECT systems online, with 214 remaining unpatched, despite the availability of a patch since 2022.
- Proof-of-concept exploits are publicly available, yet threat intelligence platforms show limited exploitation activity.
Video Walkthrough: ABB Cylon ASPECT CVE-2023-0636 and CVE-2024-6209
In this week's Initial Access Research, I dove into two key vulnerabilities in ABB's building automation and energy management software, ABB Cylon Aspect. This software is used in major installations like the American Museum of Natural History and UC Irvine, making these vulnerabilities noteworthy for security teams in the industrial control Systems (ICS) sector.
Key Vulnerability: CVE-2023-0636
The main focus of the discussion is CVE-2023-0636, a command injection vulnerability in ABB Cylon Aspect. This vulnerability allows for remote code execution, making it a serious threat, particularly in internet-facing systems. While ABB claims authentication is required for exploitation, research shows otherwise, allowing attackers easier access than initially assumed.
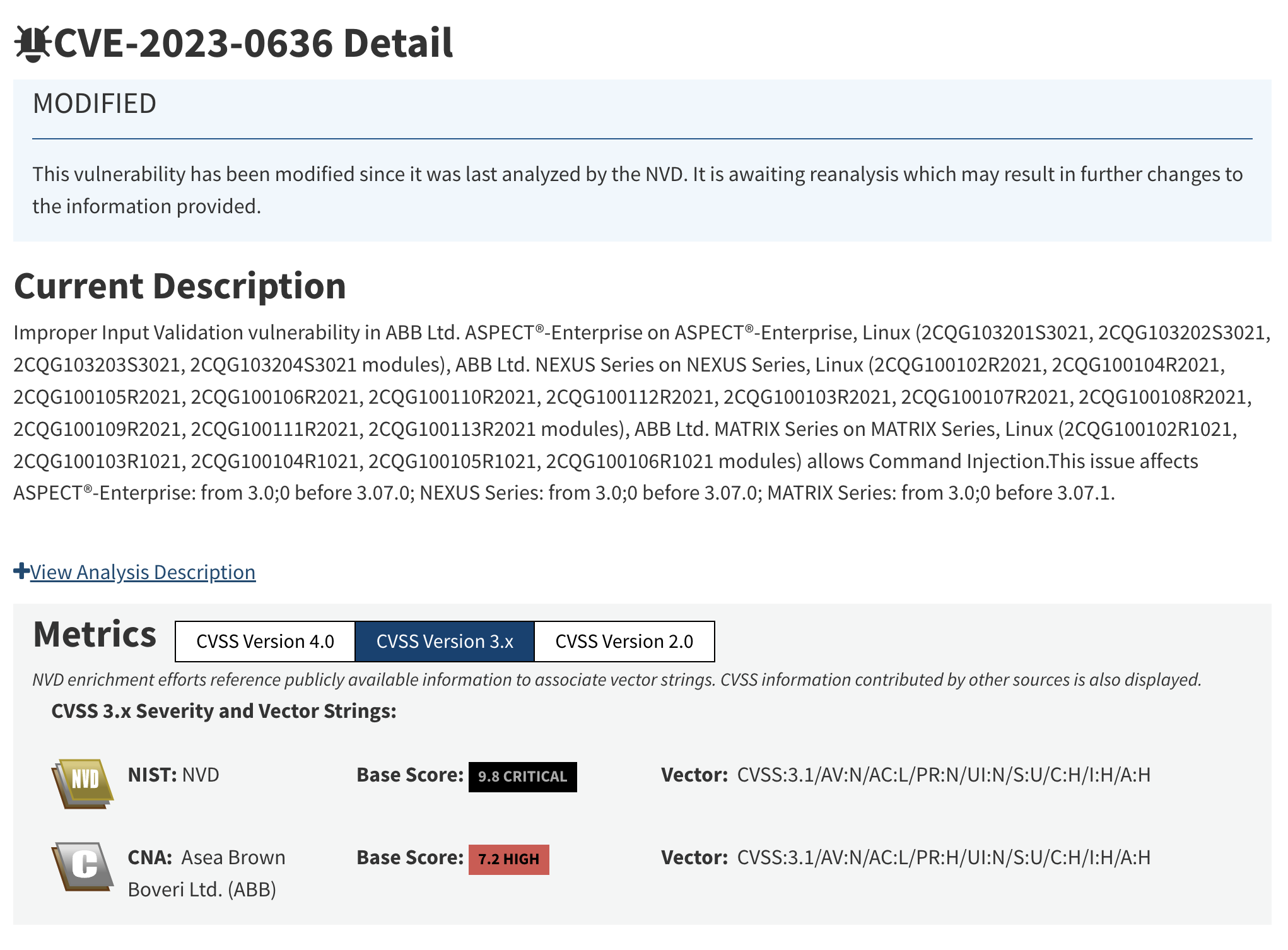
The VulnCheck team explored exploit data and showcased a proof-of-concept (POC) originally published on Packet Storm by security researcher “Liquid Worm.” This POC revealed multiple ways to exploit the command injection, with little resistance in place. VulnCheck verified the vulnerability using internal tooling and developed an unobtrusive version scanner to assess its presence in live systems, discovering 265 reachable systems, of which 214 unpatched systems, despite a patch available since 2022.
Further Vulnerabilities: File Disclosure and Remote Code Execution
In addition to CVE-2023-0636, Liquid Worm disclosed an unauthenticated file disclosure vulnerability, allowing attackers to retrieve user credentials in plain text. This gap in ABB’s products significantly elevates the risk, as these credentials can then facilitate other command injections and remote code executions within the system.
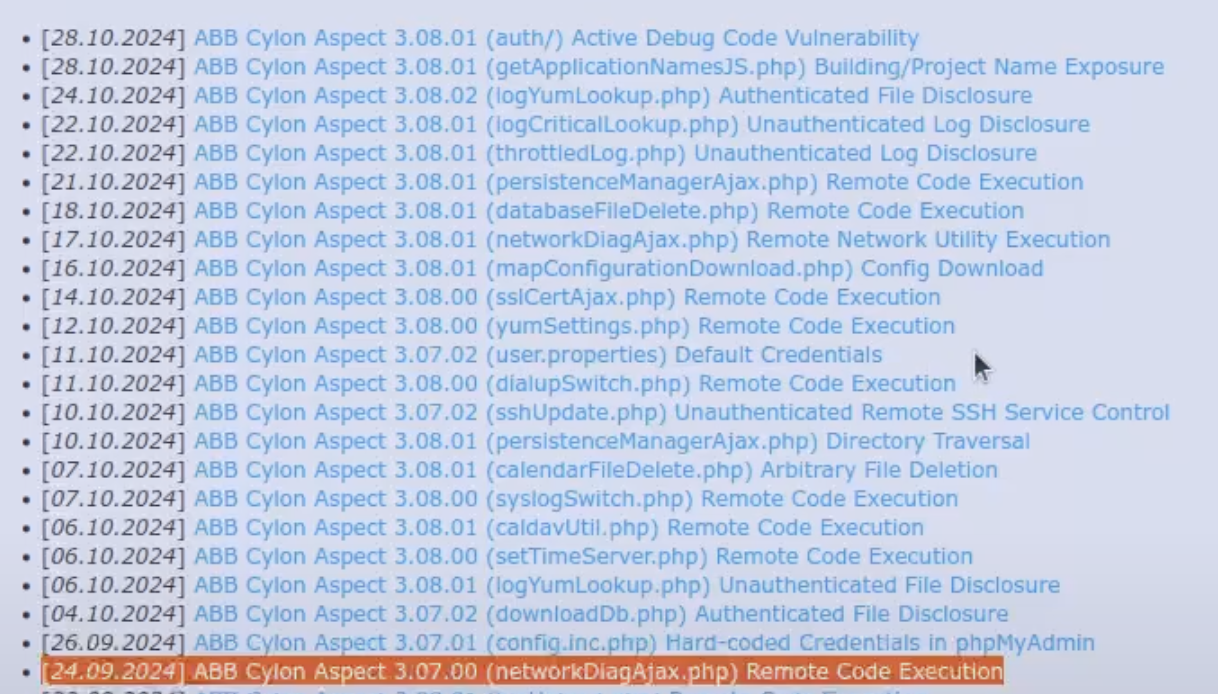
Real-World Impact and Action For Impacted Organizations
The VulnCheck team found hundreds of vulnerable ABB Cylon Aspect installations online through platforms like Shodan and Censys. Surprisingly, despite available exploits, no major exploitation activity has been recorded in threat intelligence sources like GreyNoise. However, this discovery underscores the need for organizations with Industrial Control Systems to actively monitor and patch these vulnerabilities, especially as critical infrastructure software often remains online.
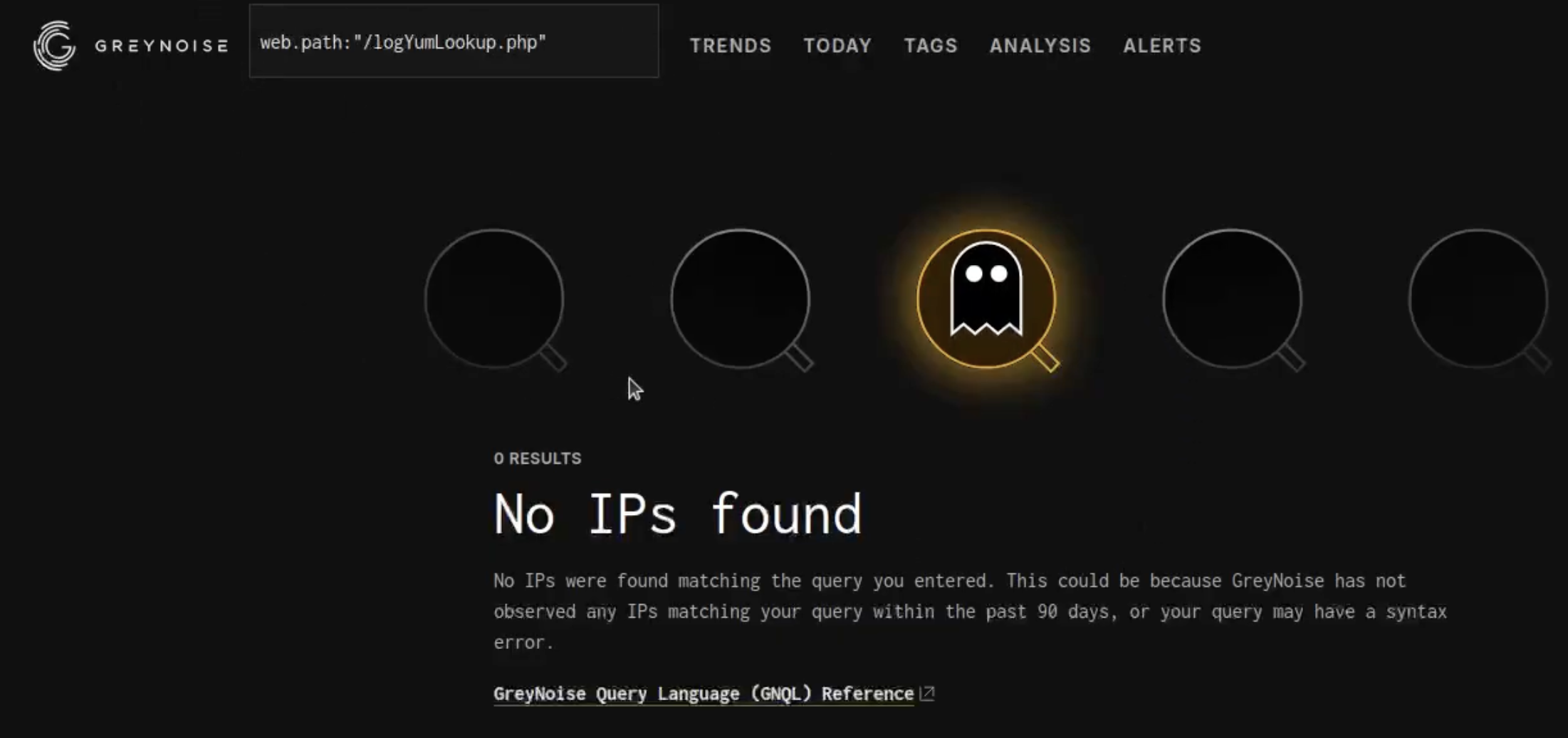
Security professionals should ensure that customers keep such high-risk systems patched, as ABB advises against exposing these systems online at all. This highlights the risk associated with unpatched and publicly accessible control systems.
What Defenders Can Do
- If your organization uses ABB Cylon Aspect, ensure that these devices are patched and up to date.
- Ensure the ABB devices and other Industrial Control Systems are not accessible on the internet.
- Use the detection signatures we’ve provided to monitor for any signs of exploitation.
About VulnCheck
The VulnCheck Initial Access team is always looking to advance the state of attack on initial access vulnerabilities. For more research like this, see our blogs, PaperCut Exploitation and Fileless Remote Code Execution on Juniper Firewalls . Sign up to start a trial of our Initial Access Intelligence and Exploit & Vulnerability Intelligence product today.