Welcome to the VulnCheck KEV Catalog
VulnCheck now offers access to a new Community resource, the VulnCheck Known Exploited Vulnerabilities (KEV) catalog. The free offering, available by joining the VulnCheck Community, provides advanced intelligence on vulnerabilities that have been exploited wild. VulnCheck’s KEV catalog provides organizations with earlier and broader visibility into known exploitation, along with publicly available references indicating where and when exploitation was reported from credible sources.
The VulnCheck KEV catalog can be accessed through our Community Edition via the VulnCheck KEV dashboard, machine-readable JSON, and the VulnCheck KEV API endpoint. To illustrate the value of the VulnCheck KEV, let's examine the exploitation timeline for a recent vulnerability.
Exploring Exploitation of Atlassian Confluence CVE-2023-22527
For this demonstration, we'll use CVE-2023-22527, an Atlassian Confluence Server vulnerability added to CISA KEV on January 24th, 2024. We can explore the JSON data from VulnCheck KEV using the following URL: https://api.vulncheck.com/v3/index/vulncheck-kev?cve=CVE-2023-22527
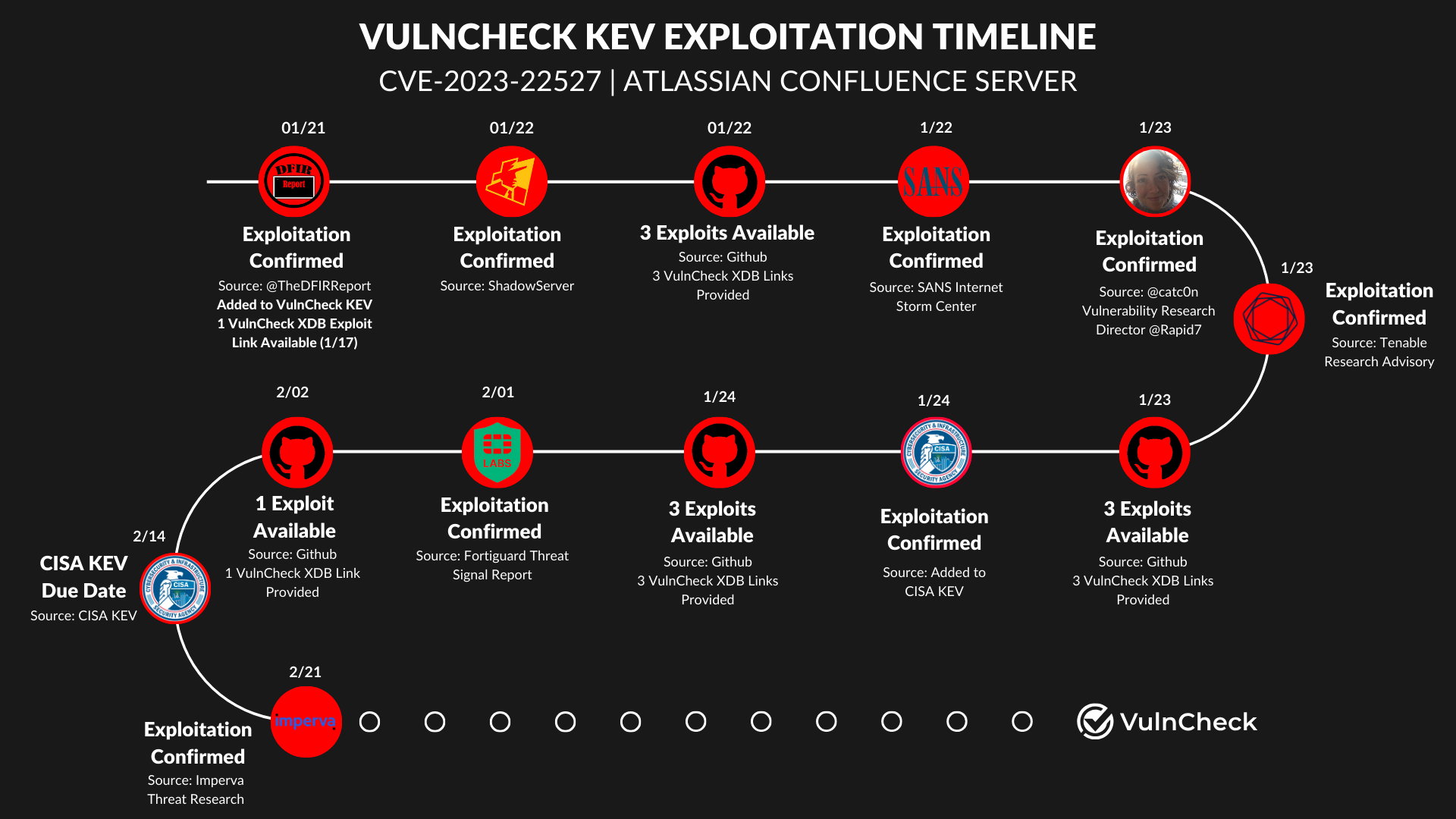
Reviewing the JSON, we observe the following timeline for the CVE:
- 01-21-2024: Date of first observation by a public source
- 01-24-2024: Date added to CISA KEV
- 02-14-2024: Date by which CISA requires federal agencies to remediate the vulnerability
Example JSON from VulnCheck KEV:
"dueDate": "2024-02-14T00:00:00Z",
"cisa_date_added": "2024-01-24T00:00:00Z",
"date_added": "2024-01-21T00:00:00Z",
"_timestamp": "2024-02-26T09:25:46.098273Z"
Exploring References for Known Exploitation
Now, with a high-level overview of the timeline of publicly known exploitation, let's examine the referenceable sources provided in VulnCheck KEV. For this CVE, there are nine available reference sources to date, including:
- 01-21-2024 (First Seen): @TheDFIRReport
- 01-22-2024: ShadowServer
- 01-22-2024: Sans Internet Storm Center
- 01-23-2024: @catc0n
- 01-23-2024: Tenable Blog
- 02-01-2024: Fortiguard Threat Signal Report
- 02-21-2024: Imperva Blog
Example JSON of reported exploitation:
"vulncheck_reported_exploitation": [
{
"url": "https://www.cisa.gov/sites/default/files/feeds/known_exploited_vulnerabilities.json",
"date_added": "2024-01-24T00:00:00Z"
},
{
"url": "https://dashboard.shadowserver.org/statistics/honeypot/map/?day=2024-01-22&host_type=src&vulnerability=cve-2023-22527",
"date_added": "2024-01-22T00:00:00Z"
},
{
"url": "https://twitter.com/TheDFIRReport/status/1749066611678466205",
"date_added": "2024-01-21T00:00:00Z"
},
{
"url": "https://isc.sans.edu/diary/rss/30576",
"date_added": "2024-01-22T00:00:00Z"
},
{
"url": "https://twitter.com/TheDFIRReport/status/1749424404063232099?s=20",
"date_added": "2024-01-22T00:00:00Z"
},
{
"url": "https://twitter.com/catc0n/status/1749912359127105813?s=20",
"date_added": "2024-01-23T00:00:00Z"
},
{
"url": "https://www.tenable.com/blog/cve-2023-22527-atlassian-confluence-data-center-and-server-template-injection-exploited-in-the",
"date_added": "2024-01-23T00:00:00Z"
},
{
"url": "https://www.fortiguard.com/threat-signal-report/5376/atlassian-confluence-remote-code-execution-cve-2023-22527",
"date_added": "2024-02-01T00:00:00Z"
},
{
"url": "https://www.imperva.com/blog/attackers-quick-to-weaponize-cve-2023-22527-for-malware-delivery/",
"date_added": "2024-02-21T00:00:00Z"
}
]
Expanding the View Into Publicly Available Exploits
Notably, the first publicly available exploit on GitHub was accessible on 1-17-2024, before the vulnerability was published to VulnCheck KEV (Available in our commercial exploit feeds). After the first known exploitation was seen on 01-21-2024, there have been ten additional exploits posted on GitHub: three on 01-22-2024, three on 01-23-2024, three on 01-24-2024, and one on 02-02-2024.
Example JSON of Publicly Available Exploits:
"vulncheck_xdb": [
{
"xdb_id": "b86f8af644dc",
"xdb_url": "https://vulncheck.com/xdb/b86f8af644dc",
"date_added": "2024-01-23T09:28:53Z",
"exploit_type": "initial-access",
"clone_ssh_url": "git@github.com:Niuwoo/CVE-2023-22527.git"
},
{
"xdb_id": "b6e41e9efa89",
"xdb_url": "https://vulncheck.com/xdb/b6e41e9efa89",
"date_added": "2024-01-24T21:29:59Z",
"exploit_type": "initial-access",
"clone_ssh_url": "git@github.com:Privia-Security/CVE-2023-22527.git"
},
{
"xdb_id": "66eb62ffb562",
"xdb_url": "https://vulncheck.com/xdb/66eb62ffb562",
"date_added": "2024-01-22T11:38:55Z",
"exploit_type": "initial-access",
"clone_ssh_url": "git@github.com:Drun1baby/CVE-2023-22527.git"
},
{
"xdb_id": "2054e543b959",
"xdb_url": "https://vulncheck.com/xdb/2054e543b959",
"date_added": "2024-01-22T13:26:45Z",
"exploit_type": "initial-access",
"clone_ssh_url": "git@github.com:cleverg0d/CVE-2023-22527.git"
},
{
"xdb_id": "242d461849bd",
"xdb_url": "https://vulncheck.com/xdb/242d461849bd",
"date_added": "2024-01-17T10:21:00Z",
"exploit_type": "initial-access",
"clone_ssh_url": "git@github.com:ga0we1/CVE-2023-22527_Confluence_RCE.git"
},
{
"xdb_id": "4530fd2e7aec",
"xdb_url": "https://vulncheck.com/xdb/4530fd2e7aec",
"date_added": "2024-01-24T04:44:59Z",
"exploit_type": "initial-access",
"clone_ssh_url": "git@github.com:yoryio/CVE-2023-22527.git"
},
{
"xdb_id": "d6ff5abefc7e",
"xdb_url": "https://vulncheck.com/xdb/d6ff5abefc7e",
"date_added": "2024-01-22T19:02:59Z",
"exploit_type": "initial-access",
"clone_ssh_url": "git@github.com:thanhlam-attt/CVE-2023-22527.git"
},
{
"xdb_id": "30d9851d825e",
"xdb_url": "https://vulncheck.com/xdb/30d9851d825e",
"date_added": "2024-01-23T10:55:28Z",
"exploit_type": "initial-access",
"clone_ssh_url": "git@github.com:Chocapikk/CVE-2023-22527.git"
},
{
"xdb_id": "4875746a557f",
"xdb_url": "https://vulncheck.com/xdb/4875746a557f",
"date_added": "2024-02-02T04:20:14Z",
"exploit_type": "initial-access",
"clone_ssh_url": "git@github.com:YongYe-Security/CVE-2023-22527.git"
},
{
"xdb_id": "a3677d9bae7f",
"xdb_url": "https://vulncheck.com/xdb/a3677d9bae7f",
"date_added": "2024-01-23T07:10:55Z",
"exploit_type": "initial-access",
"clone_ssh_url": "git@github.com:VNCERT-CC/CVE-2023-22527-confluence.git"
}
]
A Clearer Picture Into Known Exploited Vulnerabilities
Having gathered this exploitation information, we can assemble the timeline into a clear visualization to better understand the publicly known exploitation evidence provided in VulnCheck KEV.

This example underscores how early visibility into exploitation, along with references to exploits, offers timely insight into known exploitation—a key value of using VulnCheck KEV.
Gain access to VulnCheck’s KEV catalog, which includes the data shown in this example for over 1,900 known exploited vulnerabilities, by registering for VulnCheck Community Edition here.
About VulnCheck
Are you interested in gaining broader visibility into vulnerability intelligence and exploitation? If so, VulnCheck's Exploit & Vulnerability Intelligence provides the broadest coverage to gain early access into the known. Register and demo our data today.