Overview
Sophos took immediate steps to remediate CVE-2022-3236 – an unauthenticated and remote code execution vulnerability affecting the Sophos Firewall Webadmin and User Portal HTTP interfaces – with an automated hotfix sent out in September 2022. Through its advisory published on September 23, 2022, it also alerted users who don't receive automatic hotfixes to apply the update themselves. The advisory stated the vulnerability had previously been used against "a small set of specific organizations, primarily in the South Asia region." In December, Sophos released v19.5 GA GA with an official fix.
Assessing Potential Exploitation of Sophos Firewall and CVE-2022-3236
/logs/csc.log and /log/validationError.log.Few Public Details
CVE-2022-3236 was quickly added to the CISA Known Exploited Vulnerabilities Catalog and Zero Day Initiative (ZDI) published a high-level description of the issue in October, but public information has otherwise been non-existent. Self-described “proof of concept” exploits have been published to GitHub, but they were quickly deleted, likely due to their scamming nature. Sploitus has cached a number of these repositories.
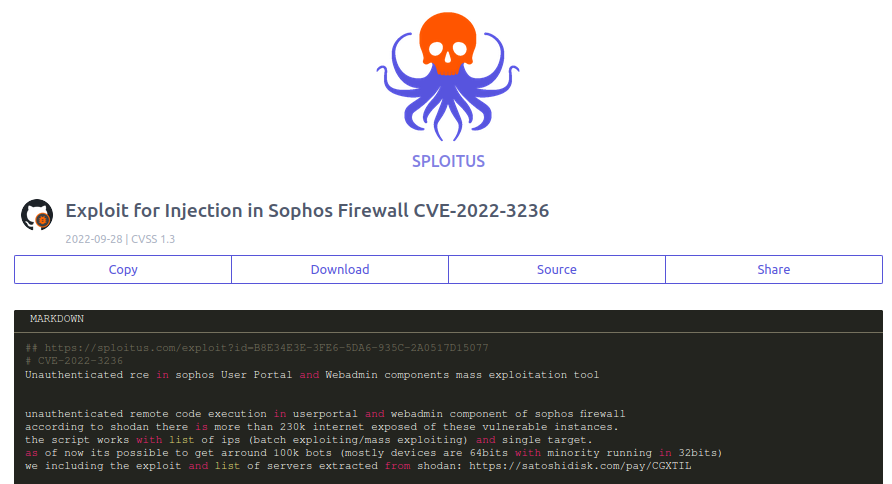
As the image shows above, the repository is soliciting payment via satoshidisk.com for a promised exploit and targeting information. This is a common scam that leaves many buyers unsatisfied.
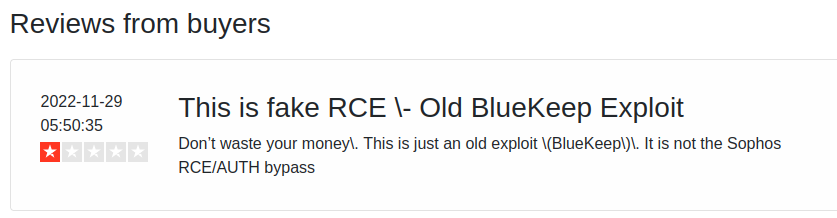
At the time of writing, there appears to be no public proof of concept exploits. However, the ZDI article gives sufficient information to quickly reproduce the issue (as we have), so it’s only a matter of time before something is made public.
Sophos Firewall in the Wild
The scam repositories aren’t surprising given the popularity of Sophos Firewall. Using Shodan, we can identify ~78,0000 User Portal and ~10,000 WebAdmin interfaces.
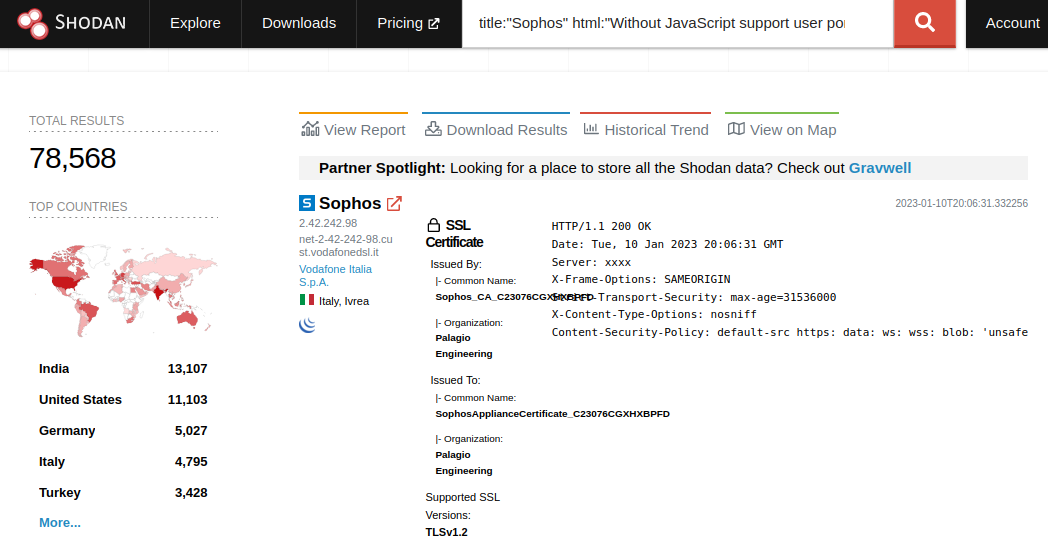
Since we wrote our own exploit for CVE-2022-3236 (and CVE-2022-1040), we were curious how many internet-facing Sophos Firewalls might still be vulnerable. We performed a version scan of the servers we identified on Shodan, and found the following results (some low volume hotfixed versions excluded from the graphs due to size):
Sophos Firewalls Using Fixed Versions
Sophos Firewalls Using Versions with a Hotfix Available
Sophos Firewalls Using Vulnerable Versions
More than 99% of internet-facing Sophos Firewalls haven't upgraded to versions containing the official fix for CVE-2022-3236. But around 93% are running versions that are eligible for a hotfix, and the default behavior for the firewall is to automatically download and apply hotfixes (unless disabled by an administrator). It’s likely that almost all servers eligible for a hotfix received one, although mistakes do happen. That still leaves more than 4,000 firewalls (or about 6% of internet-facing Sophos Firewalls) running versions that didn’t receive a hotfix and are therefore vulnerable.
Indicators of Compromise
There are firewalls that remain vulnerable to CVE-2022-3236, and the vulnerability was exploited as a 0-day for a period of time. After developing our exploit, we looked for high-quality indicators of compromise. We believe two log files have good indicators of exploitation attempts. The first file is /logs/csc.log.
Our exploit generates the following partially redacted log entry:
MESSAGE Jan 06 12:42:45Z [worker:15566]: {
"request": {
"method": "opcode",
"name": "myaccount_login",
"version": "1.6",
"type": "json",
"length": 441,
"data": {
"value": REDACTED,
"APIVersion": "1805.2",
"transactionid": "73",
"___serverport": 443,
"___serverip": "10.12.70.202",
"___component": "GUI",
"_discriminator": REDACTED,
"captcha": "d376b3",
"username": "txPGiKDy",
"mode": 451,
"currentlyloggedinuserip": "10.12.70.252",
"___serverprotocol": "HTTP",
"password": "****"
}
}
}
The presence of the _discriminator field in a login request is sufficient to detect an exploit attempt. The other log, /log/validationError.log, has a similar, but much more verbose indicator.
********** Entity json validation log:6-1-2023 7:42:33 Objectname=login::login
=> Validation start for: password
- Validating type : SCALAR,STRING
- Validating 'datatype' : Result=true
- Validating 'require' : Result=true
- Validating 'validateValidAndInvalidInput' for type SCALAR
=> Validation start for: mode
- Validating 'validateValidAndInvalidInput' for type SCALAR
=> Validation start for: value
- Validating 'validateValidAndInvalidInput' for type SCALAR
=> Validation start for: APIVersion
- Validating 'validateValidAndInvalidInput' for type SCALAR
=> Validation start for: captcha
- Validating 'validateValidAndInvalidInput' for type SCALAR
=> Validation start for: ___serverip
- Validating 'validateValidAndInvalidInput' for type SCALAR
=> Validation start for: currentlyloggedinuserip
- Validating 'validateValidAndInvalidInput' for type SCALAR
=> Validation start for: username
- Validating type : SCALAR,STRING
- Validating 'datatype' : Result=true
- Validating 'require' : Result=true
- Validating 'validateValidAndInvalidInput' for type SCALAR
=> Validation start for: ___serverprotocol
- Validating 'validateValidAndInvalidInput' for type SCALAR
=> Validation start for: transactionid
- Validating 'validateValidAndInvalidInput' for type SCALAR
=> Validation start for: ___serverport
- Validating 'validateValidAndInvalidInput' for type SCALAR
=> Validation start for: _discriminator
- Validating 'validateValidAndInvalidInput' for type SCALAR
=> Validation start for: ___component
- Validating 'validateValidAndInvalidInput' for type SCALAR
Again, note the presence of the _discriminator field within a login request. We encourage Sophos Firewall administrators to look through their logs to determine if they see these indications of an exploit attempt.
Limitations of Exploitation
While CVE-2022-3236 does allow an attacker to inject and execute arbitrary Perl, there is a limitation to mass exploitation. By default, Sophos Firewall requires web clients to solve a captcha during authentication.
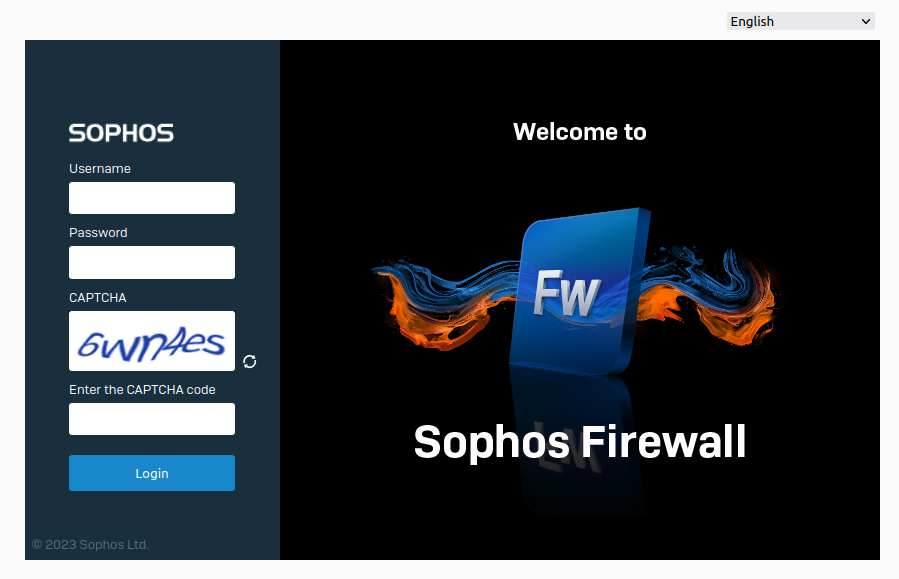
The vulnerable code is only reached after the captcha is validated. A failed captcha will result in the exploit failing. While not impossible, programmatically solving captchas is a high hurdle for most attackers. Most internet-facing Sophos Firewalls appear to have the login captcha enabled, which means, even at the most opportune times, this vulnerability was unlikely to have been successfully exploited at scale.
Conclusion
CVE-2022-3236 is one of those rare vulnerabilities that has been exploited in the wild with few details ever made public. Having developed an exploit ourselves, we can say this vulnerability was likely never as scary as it sounded thanks to the swift work of Sophos and good default security settings on the firewall itself. Internet-facing firewalls appear to largely be eligible for hotfixes and the default authentication captcha likely prevented mass exploitation.
For more information on vulnerabilities exploited in the wild, register for a VulnCheck account today by loading https://vulncheck.com and clicking “Log In”.