On June 22, 2023, Palo Alto Networks Unit 42 published IoT Under Siege: The Anatomy of the Latest Mirai Campaign Leveraging Multiple IoT Exploits. The blog discusses a Mirai botnet variant using a handful of "new" CVEs to propagate.
One of the vulnerabilities was CVE-2022-29303. CVE-2022-29303 is an unauthenticated and remote command injection vulnerability affecting the Contec SolarView Series. Since VulnCheck Exploit Intelligence has indexed a number of public exploits for SolarView, we decided to dig in and examine the potential scale and impact of this exploitation in the wild.
To understand the potential impact, we first need to know what Contec SolarView is. SolarView monitors and visualizes small to medium-scale solar power generation and storage. Contec’s website advertises that the “SolarView brand … has been introduced at more than 30,000 power stations.” It also highlights deployment scenarios for SolarView Air and SolarView Battery that depict the hardware being used in commercial buildings and solar power plants. Contec SolarView is clearly intended for ICS networks, so you’d hope to never find one accessible over the internet.
Shodan currently indexes more than 600 SolarView systems.
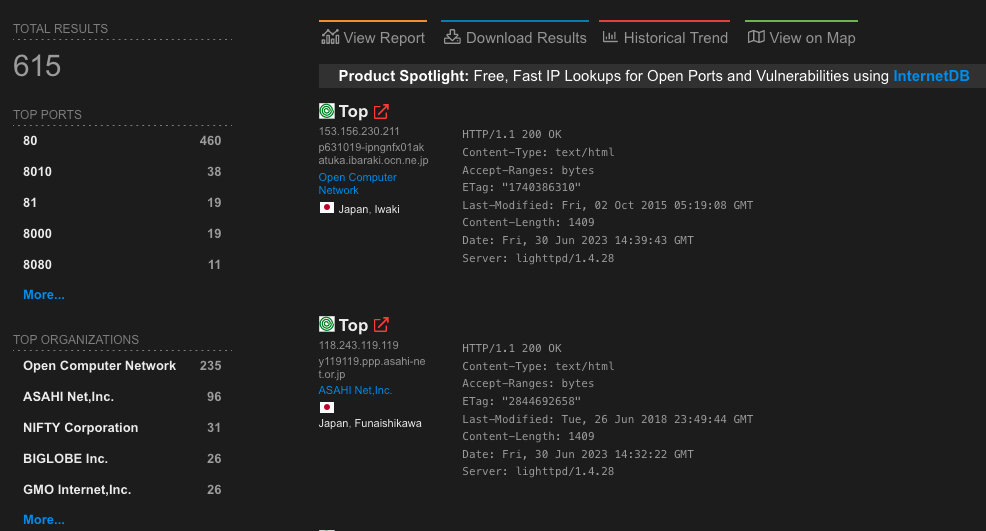
Palo Alto Networks’ recent blog touches on the Mirai-variant abusing CVE-2022-29303. According to the CVE description, the affected versions of SolarView are “ver.6.00”. Version 6.00 was released in 2019, and SolarView Compact has seen four firmware releases since then (6.20 in 2019, 7.00 in 2021, 8.00 in 2022, and 8.10 in 2023). That suggests that only a small subset of internet-facing hosts are likely to be vulnerable. However, further examination of SolarView’s firmware revealed that this CVE description is inaccurate.
CVE-2022-29303 affects the web server’s conf_mail.php endpoint, but version 6.20 (the version following the reportedly vulnerable 6.00) didn’t implement a fix for the issue. Not only was version 6.00 affected, but 6.20 as well. In fact, we found that the very straight-forward command injection in conf_mail.php has existed since at least version 4.00:
if( isset($_REQUEST['button']) ){
$button = $_REQUEST['button'];
$mail_address = $_REQUEST['mail_address'];
}
include("include/ShowMsg.func");
include("include/common.def");
$TestMailLog = "/var/log/SMail_test.log";
$CONFFILE = $ConfDataDir."/fws_mail.conf";
if( $button == $LABEL_SENDEXEC ){
$mail_address = str_replace( " ","", $mail_address );
if( strlen($mail_address) > 3 ){
$sendmes = "SolarView";
$exec_cmd = "echo -1 ".$mail_address." TEST-MAIL '$sendmes' > /dev/elogparam";
system( $exec_cmd );
$status = 2;
}
else{
$status = 3;
}
}
It wasn’t until version 8.00 that conf_mail.php was added to the auth.require list, and validation is added to the attacker-controlled $mail_address variable.
if( isset($_REQUEST['button']) ){
$button = $_REQUEST['button'];
$mail_address = EscStr($_REQUEST['mail_address']);
$mail_address = str_replace(" ","",$mail_address);
$address_array = explode(",", $mail_address);
$mail_address = "";
$cnt = 0;
for( $i = 0 ; $i < sizeof($address_array) ; $i++ ){
if( filter_var($address_array[$i], FILTER_VALIDATE_EMAIL) ){
if( $cnt == 0 ){
$mail_address = $address_array[$i];
}
else{
$mail_address .= ",".$address_array[$i];
}
$cnt++;
}
}
}
Suffice to say, the range of affected systems is much wider than the CVE description lets on, and thanks to a copyright string on the landing page (and the sparse amount of releases over the years), we can easily fingerprint the affected internet-facing systems.
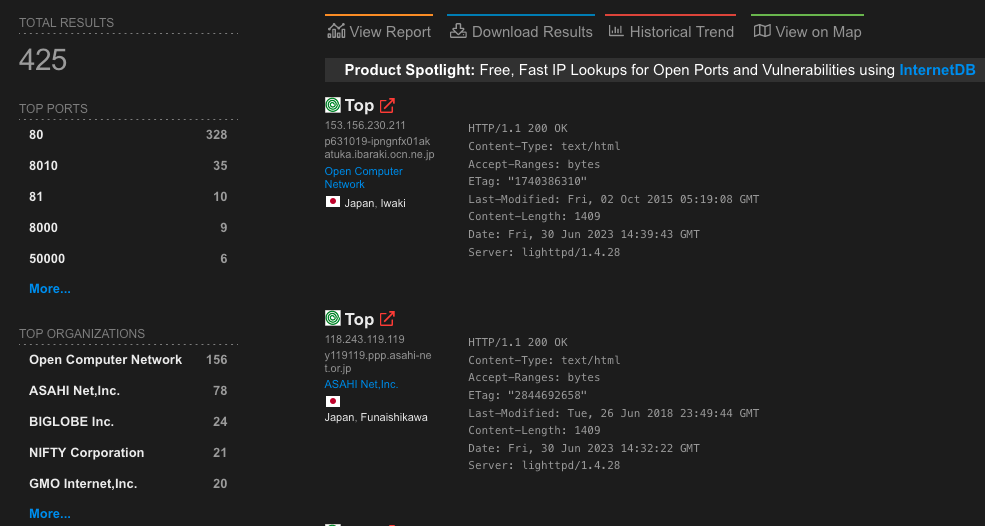
It turns out that less than one third of the internet-facing SolarView series systems are patched against CVE-2022-29303.
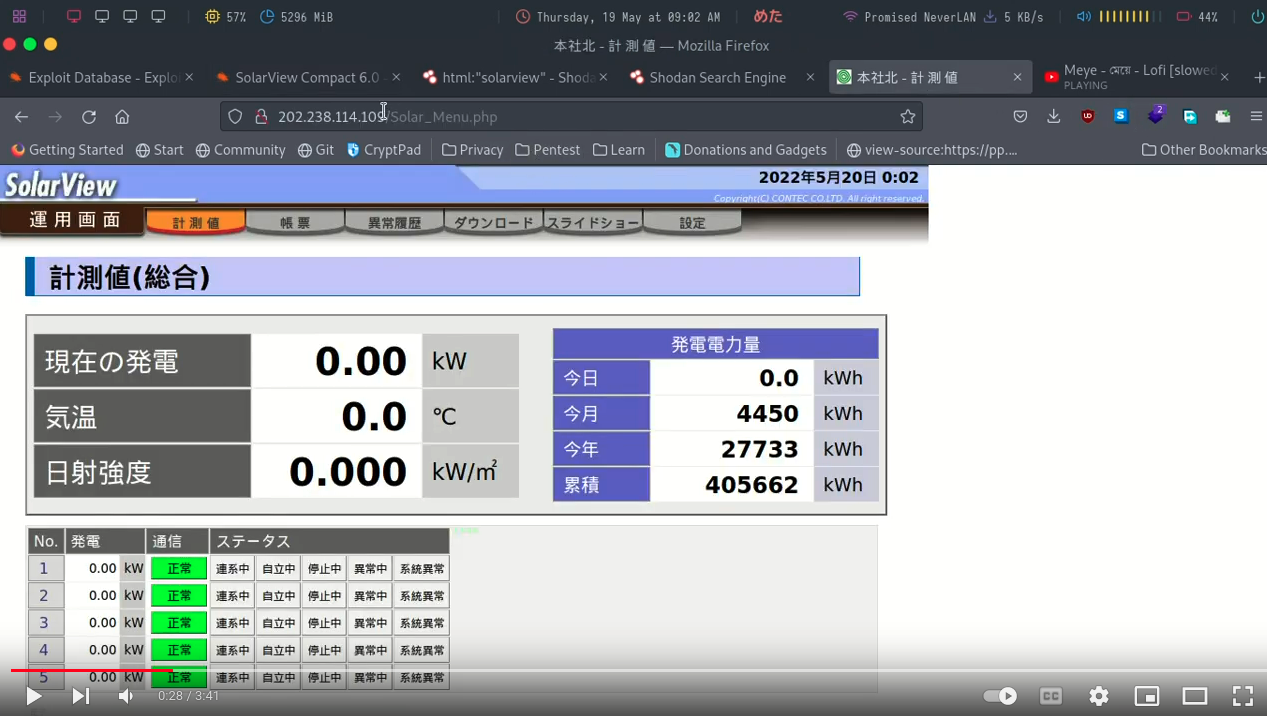
Additionally, Unit 42’s blog wasn’t even the first indication that the vulnerability was being exploited in the wild. CVE-2022-29303 has had an Exploit-DB entry since May 2022. GreyNoise mentioned the vulnerability in a blog in May 2023. And a YouTube video from May 2022 shows an attacker using the Exploit-DB exploit against a SolarView system found on Shodan (why one would post their crimes to YouTube, I’ll never know).
It gets worse. While CVE-2022-29303 has garnered attention from some organizations like Unit 42 and GreyNoise, there are a couple of other unauthenticated RCEs affecting the systems that have not.
For example, CVE-2023-23333 affects the SolarView series up to version 8.00 (despite the fact that the CVE description says “through 6.0”). This vulnerability doesn’t have any Exploit-DB entries, but it has multiple exploits on GitHub.
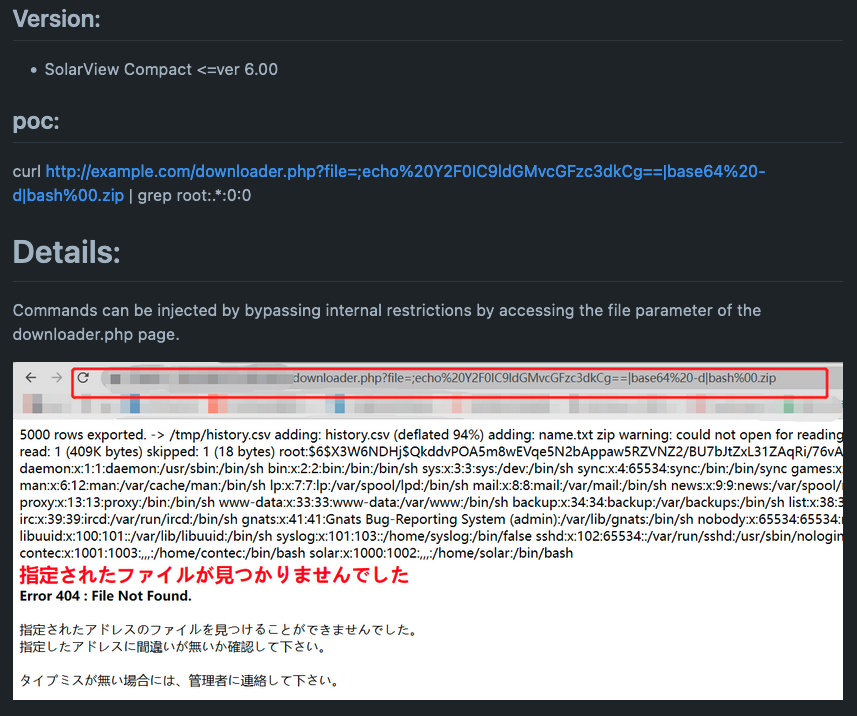
CVE-2023-23333 is a simple command injection affecting the downloader.php endpoint (specifically mishandling of user data in the zip case).
if( isset($_REQUEST['file']) ){
$file = $_REQUEST['file'];
}
function get_extend( $filename ){
$pos = strrpos( $filename, "." );
return substr( $filename, $pos );
}
$ext = get_extend( $file );
switch( $ext ){
case ".csv":
break;
case ".jpg":
case ".jpeg":
case ".JPG":
case ".JPEG":
case ".Jpeg":
case ".Jpg":
case ".gif":
case ".GIF":
case ".Gif":
$path = "/home/www/html/images/";
break;
case ".zip":
$ARCH_FILE = sprintf("/home/contec/data/%s", $file);
if( file_exists($ARCH_FILE) ){
unlink($ARCH_FILE);
}
$cmd = sprintf("/usr/local/bin/data_zip.sh %s > /dev/null", basename($ARCH_FILE));
system($cmd);
$file = $ARCH_FILE;
break;
}
The SolarView Series is also affected by CVE-2022-44354, a file upload vulnerability that allows an attacker to upload a PHP webshell to the system. The CVE description says “Compact 4.0 and 5.0” are affected, but there’s a duplicate CVE (CVE-2022-31374) that says Compact 6.0 is affected. Either way, we see no changes to /Solar_Image.php (the affected component) until version 7.0.
- else if( $img_type < 0 || 3 < $img_type ){
+ else if( $img_type <= 0 || 3 < $img_type ){
echo "JPEG”;
}
else{
- copy( $userfile, $IMG_PATH."/".basename($userfile_name));
- echo urldecode($userfile_name)."<BR>\n";
- chmod( $IMG_PATH."/".basename($userfile_name), 0666 );
- echo $MSG_SEND_OK."\n";
+ $cmd = sprintf("/usr/bin/file %s | awk '{print $2}'",$userfile );
+ $img_type = exec( $cmd);
+ if( $img_type == "GIF" || $img_type == "PNG" || $img_type == "JPG" || $img_type == "JPEG" ){
+ copy( $userfile, $IMG_PATH."/".basename($userfile_name));
+ echo urldecode($userfile_name)."<BR>\n";
+ chmod( $IMG_PATH."/".basename($userfile_name), 0666 );
+ echo $MSG_SEND_OK."\n";
+ }
The changes in version 7.00 are trivially bypassed by appending the webshell to a valid image. SolarView version 8.00 adds /Solar_Image.php to the auth.require list, which at least makes this an authenticated issue now.
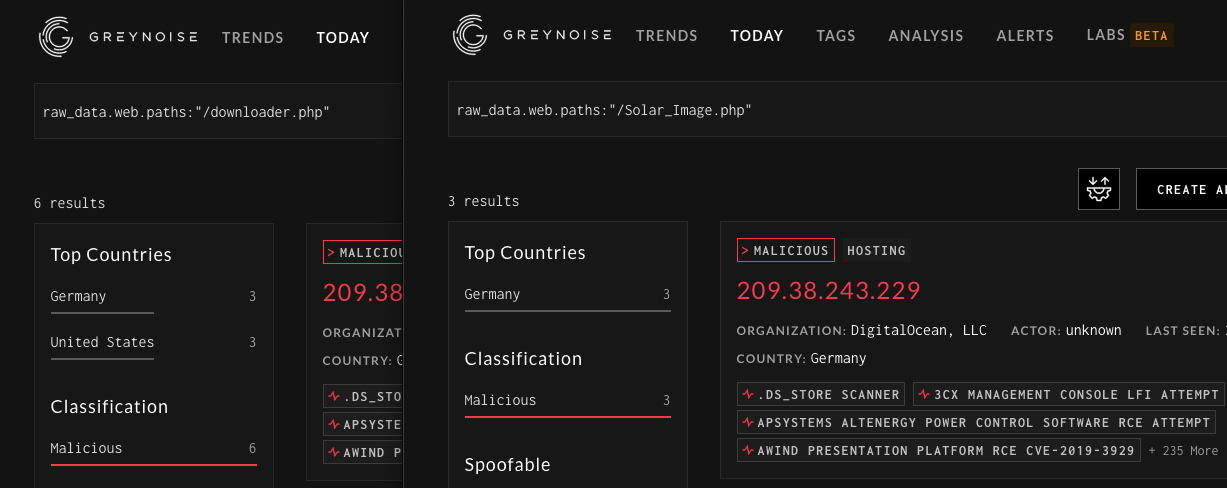
Both the /Solar_Image.php and /downloader.php endpoints appear to generate hits from malicious hosts on GreyNoise meaning that they too are likely under some level of active exploitation.
Finally, it’s worth noting that these issues are not isolated to the SolarView “Compact” hardware version. The “Air” is also affected (the code is nearly identical) and, likely, the “Battery” hardware version is affected as well.
Conclusion
We’ve looked at a few critical CVEs that affect the SolarView series and determined that there are a few hundred internet-facing systems that remain affected by these issues. When considered in isolation, exploitation of this system is not significant. The SolarView series are all monitoring systems, so loss of view (T0829) is likely the worst-case scenario.However, the impact of exploitation could be high impact depending on the network the SolarView hardware is integrated into.
For instance, if the hardware is part of a solar power generation site, then the attacker may affect loss of productivity and revenue (T0828) by using the hardware as a network pivot to attack other ICS resources.
The fact that a number of these systems are internet facing and that the public exploits have been available long enough to get rolled into a Mirai-variant is not a good situation. As always, organizations should be mindful of which systems appear in their public IP space and track public exploits for systems that they rely on.
Sign Up
For more information on vulnerabilities exploited in the wild, register for a VulnCheck account today by loading https://vulncheck.com and clicking “Log In”.