Every organization and every enterprise response team faces a growing and evolving attack surface. Product managers at all cybersecurity vendors are looking to accommodate those objectives.
However, reducing exposures in the attack surface means very different things from organization to organization, and the variability of emerging threats can affect how cyber teams respond to those threats.
An organization’s attack surface varies based on accessible devices connected to the network, web services, and APIs and the exposed vulnerabilities on them. Layer in your adversaries, their tactics, their objectives, the groups to which they belong and their attack techniques and tactics - - and your hands are full as the CISO.
Most cybersecurity products have a significant reliance on external data and intelligence to enrich the accuracy and usefulness of its output for customers. However, many intelligence sources are not machine-readable, and that lack of legibility forces users to work harder to reduce the signal to noise ratio when managing vulnerabilities.
This limits the effectiveness of any cybersecurity product, because the data has to be analyzed by humans. This means the data isn’t able to be consumed quickly enough to prevent vulnerabilities from exploitation by threat actors. Which for product managers building cybersecurity products, means more bugs and escalated support calls by customers.
While the reduction of an organization’s overall attack surface is a general goal of most products, exposure management platforms (EMP), like Sevco Security are purpose-built to ensure that organizations have a material reduction in securing areas of the business that prevents attacks from becoming a full-scale breach. We’ll look more at this below to see a tangible example of how exploit intelligence integrates with an actual EMP solution that are built on the foundation of providing a complete asset inventory. (more on this below)
The Rise of Exploits - Knowing More About Relevant Threat Actors
With a 180% increase in breaches with an exploited vulnerability as reported in the 2024 Verizon Data Breach Investigation Report, the need for reliable intelligence that can supercharge the platform is essential.
Why? Because it only takes one vulnerability, and just one attacker to weaponize any random vulnerability.
When vulnerability and exploit intelligence does not outpace the adversaries, and when manual effort is required to consume it, cybersecurity products fail to deliver their full, potential value. Product managers can rethink their workflows and the ways to use intelligence sources to help their end-users respond and defend at machine speeds.
Most intelligence sources from third-party providers require human interpretation, and aren't immediately actionable, leaving many cybersecurity platforms lacking the data to support an informed response.
Knowing your adversary means identifying the threat actors, how they operate, knowledge of their techniques and tactics, and knowing specifically their intentional impact.
Tracking threat actors is a challenge, given the inconsistent naming strategies across cybersecurity products. As such, integrating intelligence to provide end-users with real-time accuracy and visibility into the threat actor ecosystem is essential.
Here are the specific elements of threat actor intelligence that every cybersecurity product leader should consider:
- VariableThreat Actor Naming: There are many different naming schemes for Threat Actors. Cybersecurity product vendors name threat actors using their own methodologies, which makes correlating their behaviors more challenging because there isn’t a global standard.
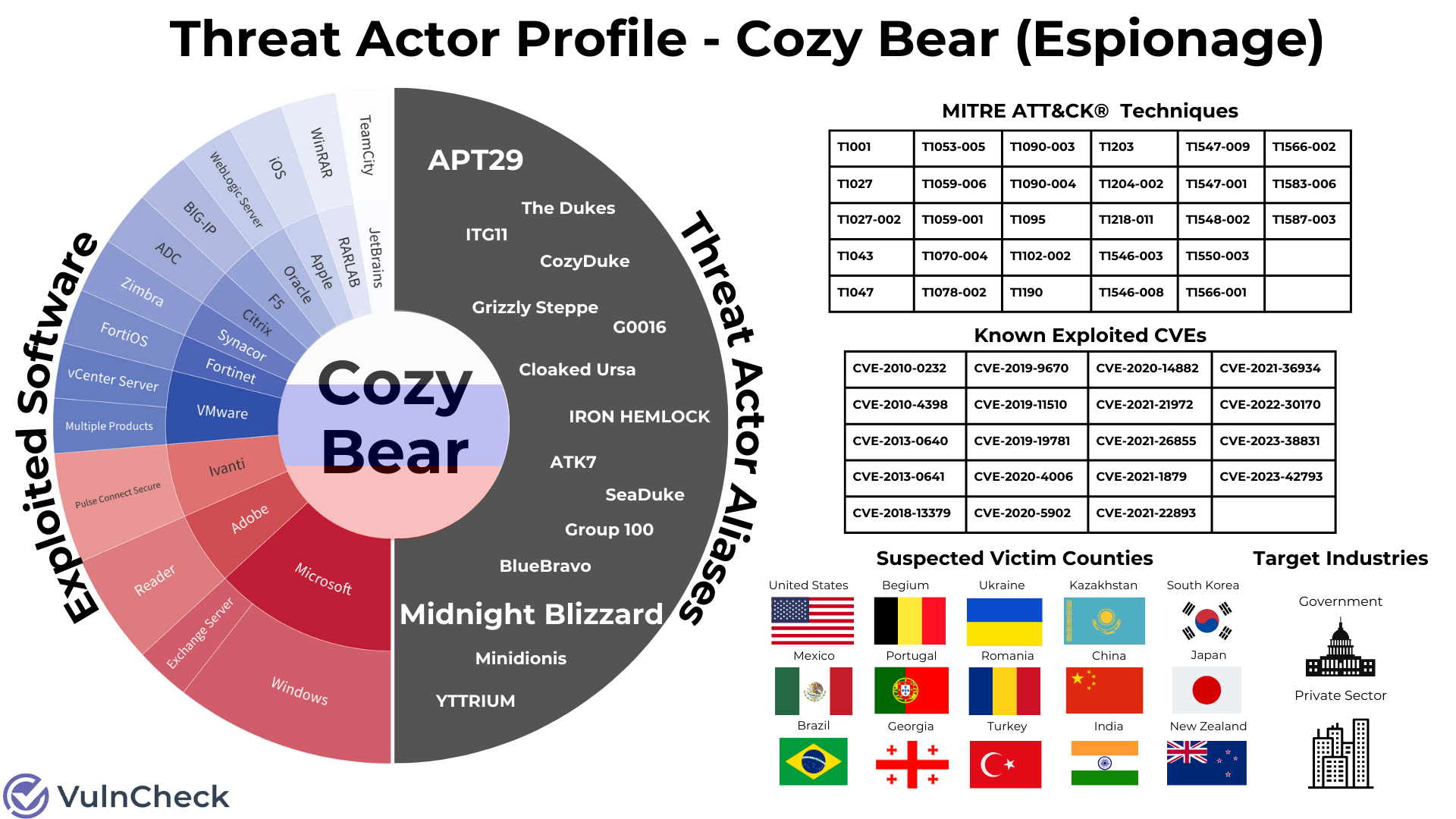
- Normalizing Threat Actor Names: Product managers should look for ways to normalize the variable naming conventions leverage the MISP and MITRE conventions, synonyms and schemes from a credible intelligence provider. Product managers should have a working knowledge of how intelligence feeds with threat actor identification indicators can help enrich other data sets - and to be effective, it must be comprehensive. The good example of this is Fancy Bear, also known as G0007, PETROVITE, APT28, SNAKEMACKERAL, Swallowtail, Group 74, Senit and Sofacy to name a few. Lookups take time, so it's essential for product managers to streamline the experience for end-users by hosting complete data sets.
Here’s an example of what that should look like for optimal threat actor data query results:
Relevant Market Use Case: Exposure and Attack Surface Management
While it’s certainly true based on the examples above that timely, accurate intelligence can reduce exposures in the attack surface in many ways - through both a platform that integrates intelligence, but also by way of just using the intelligence.
It’s also interesting to look at tools in the market, like EPM tools, where product teams are taking aggressive, proactive steps to enrich their output to further reduce the attack surface.
Sevco Security is truly one of the leaders in the ASM market - in addition to the vulnerability prioritization and exposure management market - who is using data from VulnCheck in its platform.
Sevco enables security teams to find security gaps in their environment and see both exhaustive exploit intelligence on the vulnerabilities detected and comprehensive intelligence on the assets affected – their criticality to operations, the users who access them, the other controls present to protect them.
Sevco is taking a unique approach to helping their customers reduce exposure to emerging threats with VulnCheck by integrating VulnCheck’s Community Tier solutions - notably our VulnCheck NVD++ and VulnCheck KEV.
Why is Sevco a good example? First, they’ve figured out a very smart way to ingest VulnCheck’s intelligence into their platform to enrich their own data for customers, for example, with our KEV feed that features 200% more known exploited vulnerabilities than CISA KEV. VulnCheck’s data is refreshed continuously so known exploited vulnerabilities from this single feed are instantly available in the Sevco product, and scored by Sevco.
However, starting with a CVE in this intelligence feed is a great starting point to get closer to the root of the exploitation. What product teams are building is the entire story of that CVE, complete with patterns, a full data set and the ability to surface an impact analysis.
The screenshot below shows the added enrichment VulnCheck delivers directly in the Sevco platform that clearly adds a level of timeliness to VulnCheck’s data correlation of intelligence that’s collected, and then recombined into machine-readable feeds.
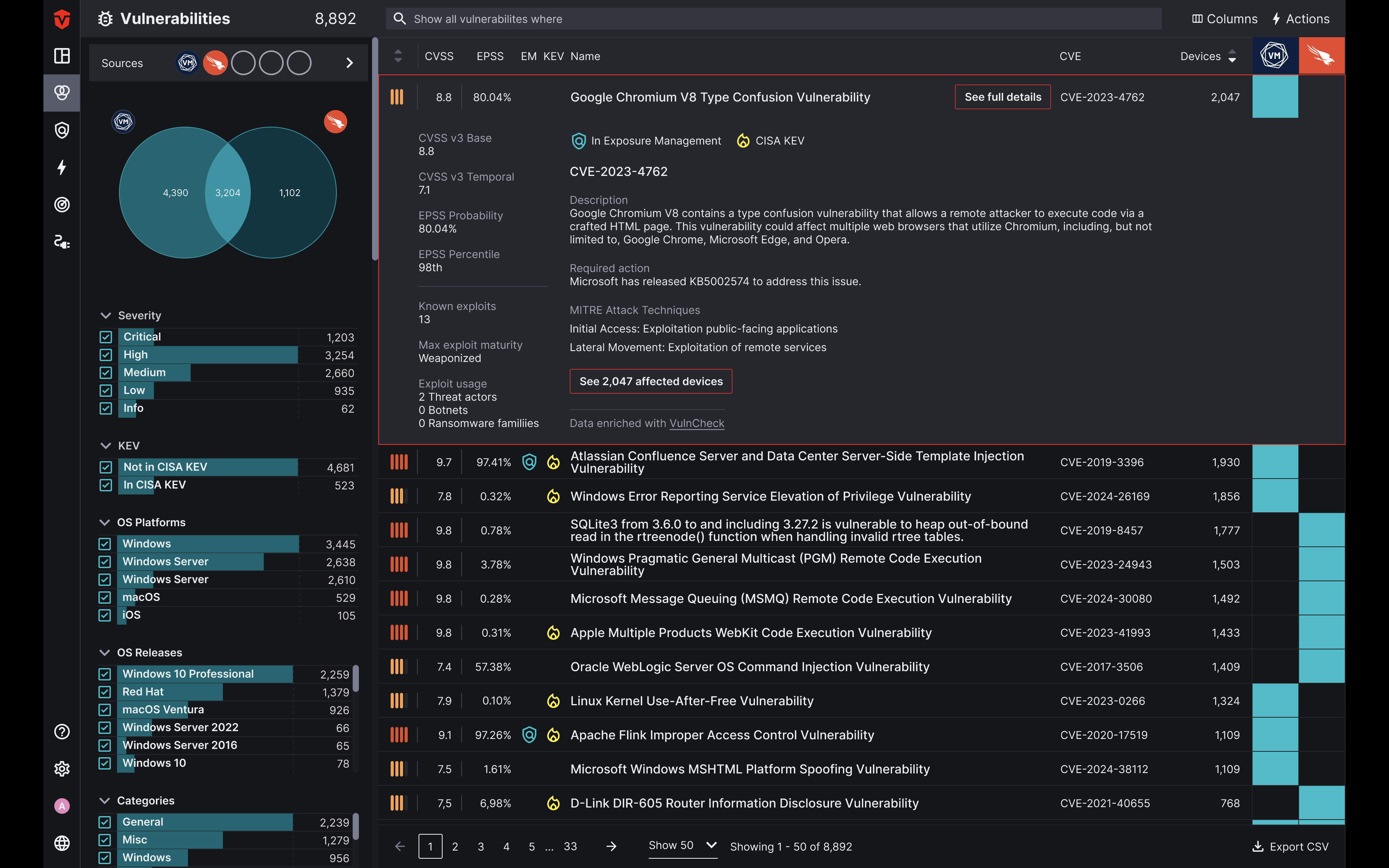
What is cool about this view that shows a demonstrable reduction in attack surface with VulnCheck’s exploit intelligence inside the Sevco platform that:
- Drills down on a single CVE in the Sevco platform, users get a unified view with context of managing exposures.
- Shows affected devices with any given CVE.
- The severity levels and the overall scoring of a particular CVE based on the CVSS, EPSS and then exploit maturity and weaponization.
- MITRE attack techniques in what’s identified.
- Exploit intelligence where vulnerabilities are identified as exploited in the wild.
In summary, there are many factors that go into selecting intelligence sources to enrich cybersecurity products so that enterprise teams can track toward continuous improvement to drive better, faster data into their products.
Sevco integrates VulnCheck intelligence and combines it with asset criticality, business context and other signals unique to the organization that essentially become ‘asset intelligence’ for the end-user. Its a great combination of vulnerability and exploit intelligence with the complete picture of device and user inventory that delivers a holistic view of the risk unpatched vulnerabilities pose to an organization's environment.
This is the first in a series of examples of how product organizations should be looking to add intelligence across many different classes of cybersecurity platforms and across multiple intelligence-based use cases.
