Key Takeaways
- VulnCheck NVD++ provides CPE for 76.95% of CVEs published in 2024 while NIST NVD only provides CPE for 41.35% of CVEs
- On average, VulnCheck NVD++ has CPE four days faster than NVD.
- VulnCheck achieves this through extensive automation and monitoring.
- VulnCheck NVD++ is available as a free community offering.
The Critical Role of CPE in Detecting Vulnerabilities
Common Platform Enumeration (CPE) is a standardized naming system for software, systems, and hardware, making it essential for accurate vulnerability management. By enabling security teams to gain visibility and identify exactly which assets are affected when a vulnerability is disclosed, CPE cuts down response times and improves patching precision. Historically, the cybersecurity industry has relied on the National Institute of Standards and Technology (NIST), the stewards of both the National Vulnerability Database (NVD) and the CPE programs, to publish CPE data alongside Common Vulnerabilities and Exposures (CVE) entries.
For years, the security industry has taken the availability of CPE data for granted, relying on it as a foundational part of cybersecurity infrastructure. That changed abruptly in March 2024, when the NVD stopped publishing CPE data. This unexpected halt created significant disruption across the industry. Countless companies, from vulnerability databases to security software vendors, found themselves scrambling to fill the gap left by the sudden absence of this vital, freely available resource. Without access to consistent, reliable and timely CPE data, these companies struggled to provide their customers with the clear, actionable intelligence they depended on.
In response, VulnCheck stepped in to help. In March 2024, we launched NVD++, an enhanced version of the NVD that includes VulnCheck-generated CPE entries. Designed as a drop-in replacement for the NVD, NVD++ allows organizations to resume providing precise, actionable vulnerability information to their customers. What’s more, VulnCheck offers NVD++ completely free of charge as part of our commitment to supporting the cybersecurity community with reliable and accessible resources.
The NVD is Back, But is it Really?
In late May 2024, NVD secured a new contract and returned to processing CVEs and new CPE data started flowing into NVD once more. Yet even with NVD’s return, there is still a gap in coverage and timeliness that is notable, leaving the need for an alternate source for timely and reliable CPE. So let’s take a look at how VulnCheck NVD++ has become the go-to source for timely, reliable and accurate CPE through our community offering, which has continued to grow, mature, and outpace NIST NVD.
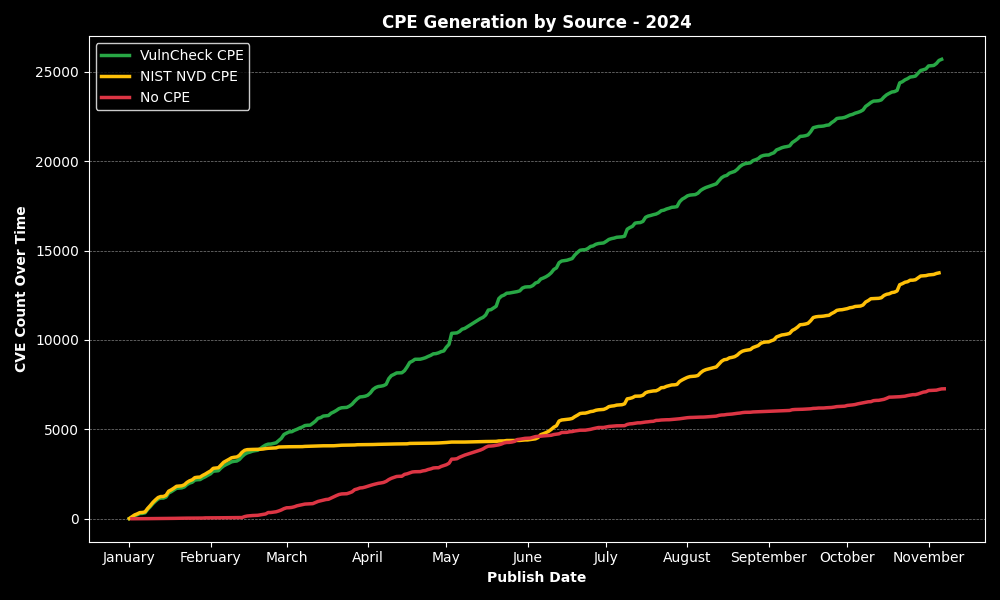
This CPE Generation chart by source maps CPE generation by the number of CVEs based on the publish date of the vulnerability. Since VulnCheck started generating CPEs in 2024 you can see the CPE generation has outpaced NVD since they paused processing in mid-February. VulnCheck has generated CPE consistently through automation and now covers 76.95% of CVEs while NIST NVD has only generated CPE for 41.35% of CVEs and is reliant on human analysis. To dive deeper into CPE generation over time, we can compare VulnCheck and NIST NVD CPE generation by day throughout 2024. This provides visibility into which organization generated CPEs in relation to each CVE’s publication date.
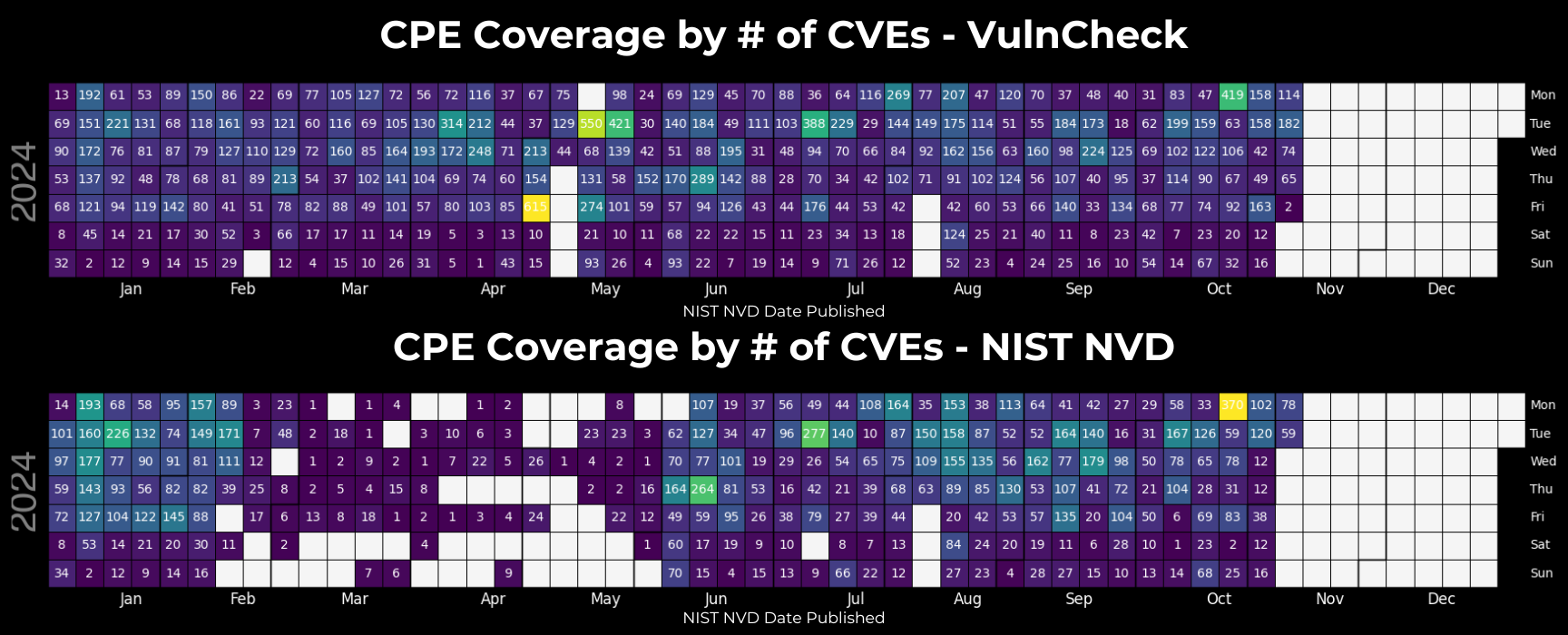
How Quickly is VulnCheck CPE Available for Timely Detection?
While NIST NVD is reliant on human analysis and publishes CPE entries on its own schedule and resource availability, VulnCheck has focused on automating the creation and validation of CPE, often within hours of a vulnerability disclosure. This accelerated timeline allows organizations to respond sooner with precision, helping them outpace their adversaries.
To put this speed advantage of VulnCheck NVD++ to the test, we conducted a four-week study from October 11 to November 8, 2024, comparing the CPE release times of CVEs between VulnCheck NVD++ and NIST NVD. The results confirmed what our users already know: VulnCheck’s accelerated CPE publication provides a critical edge in vulnerability detection.
Over the course of the study, 3,189 CVEs were published, including several CVEs that were disclosed in vendor advisories but not published to MITRE (cve.org). Of these, NVD++ contained CPE for 2,279 CVEs (71.5%) while NIST NVD contained CPE for 1,470 CVEs (46.1%) during the same time period. This shows that over a four-week period, VulnCheck generated CPE for 809 CVEs that NVD has not generated CPE for (a rate of 28 more CVE covered per day).
Accelerating the Time to Detection Ahead of NIST NVD
Our case study also helped us put a number on how much faster NVD++ receives CPE. In the 997 instances where NVD++ contained CPE and NIST NVD eventually added CPE too, VulnCheck, on average, generated CPE more than 96 hours faster than NVD.
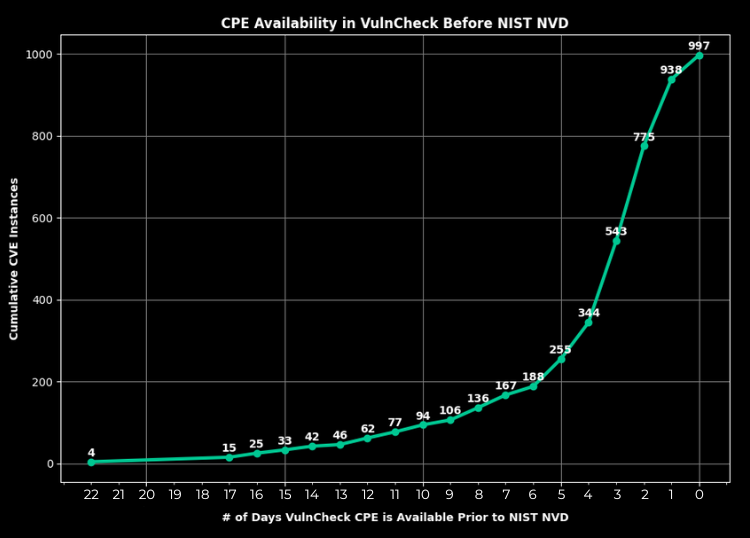
A four-day time gap provides defenders with a significant advantage in gaining visibility into their vulnerabilities faster. This can even play out on the shorter end of the time scale. For example, CVE-2024-4757, affecting Fortinet ForitManager, was published on October 23, 2024, and added to CISA KEV on the same day. VulnCheck NVD++ has CPE hours after disclosure but NIST NVD lagged behind by 24 hours - very crucial hours for a vulnerability being actively exploited in the wild.
What We Know About the CVEs without CPE in NVD++
Of the 910 CVEs that currently have no CPE assigned, many of these CVEs involve WordPress plugins, open-source projects on GitHub, or submissions to MITRE, the CNA of last resort. Many of these are new and/or esoteric software that has never been assigned CPE, and because VulnCheck only uses official CPEs created by NIST (to avoid later untangling conflicting CPE) closing this gap is not entirely possible.
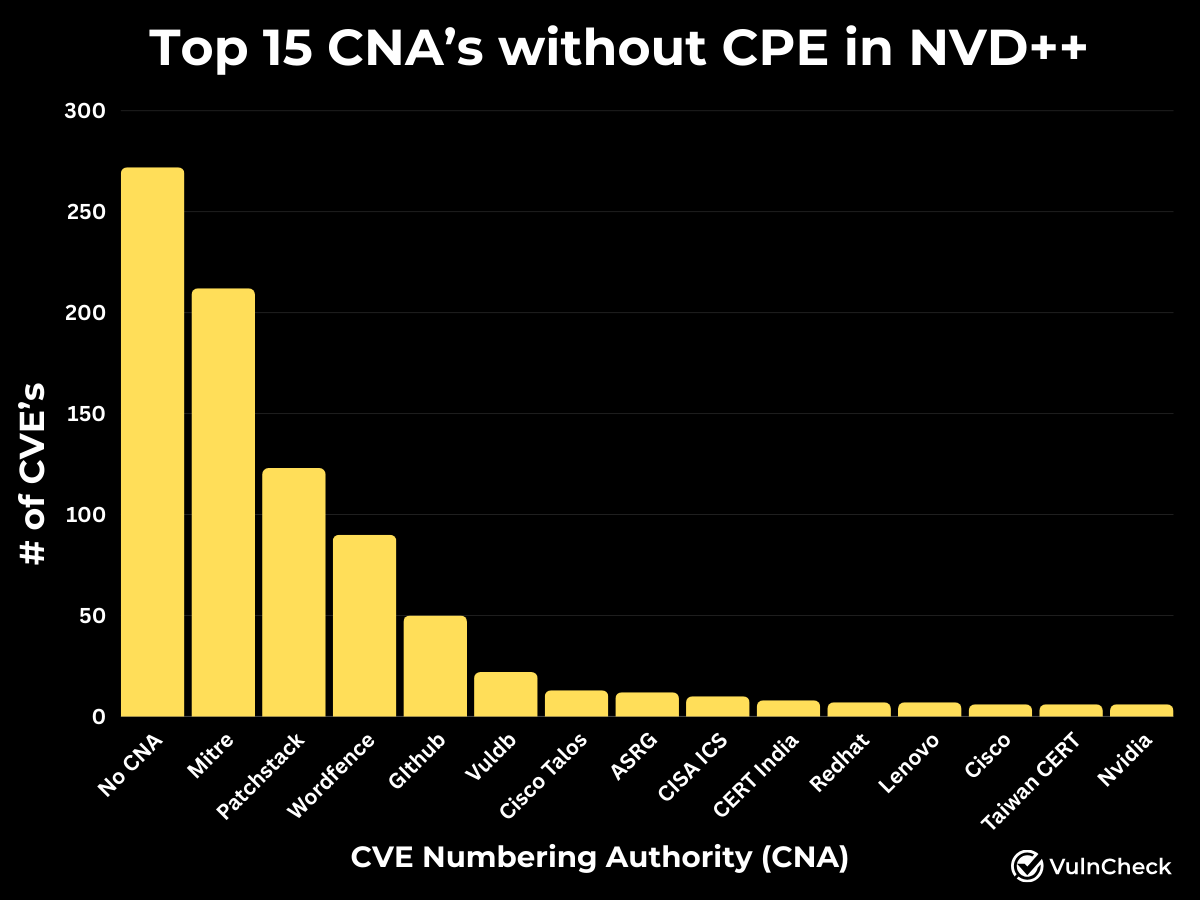
Another significant source of CVEs missing CPEs comes from CNAs that release advisories with incomplete or poorly formatted information and neglect to submit the CVE to MITRE. These account for approximately 30% of the CVEs without CPEs in our NVD++ study. Although it sounds unbelievable, our data supports this finding. Here are three examples: ZDI published an advisory for CVE-2024-9710 on October 15 with no corresponding entry on cve.org; Bosch did the same for CVE-2024-33618 on October 16; and IBM for CVE-2024-28786 on October 17. This pattern repeats daily, averaging around 10 CVEs per day.
NVD++: Faster CPE Through Automation
VulnCheck is able to achieve a faster CPE generation time because our commercial offering, Exploit and Vulnerability Intelligence (EVI), monitors almost 500 unique CVE data sources. EVI normalizes the data sources and makes them available over an API or via bulk download, which gives us a huge lake of data from which to build and normalize CPE data. As VulnCheck continues to invest in EVI, NVD++ will continue improving due to the increased volume of data.
Our commercial customers also greatly benefit from the fast CPE generation times because they have access to our CPE API, which allows them to look up CPEs and receive all the known vulnerabilities without ever even having to integrate with a data source like NVD++ or NIST NVD. Additionally, since we generate everything automatically, our commercially available CPE Dictionary contains new versions significantly faster than the NIST CPE dictionary.
Accessing VulnCheck and NVD CPE from a Single Reliable Source w/ VulnCheck NVD++
VulnCheck NVD++ provides seamless access to both VulnCheck CPE and NIST CPE from a single source. This free community offering delivers the full NIST NVD dataset, enriched with VulnCheck CPE, via high-speed API and bulk download. You can download a complete copy of the data in seconds.
To receive CPE faster to better support your customers, go to https://www.vulncheck.com and click the “Sign in / Join” button on the top right. You’ll automatically be given access to all of our VulnCheck community offerings, including NVD++.