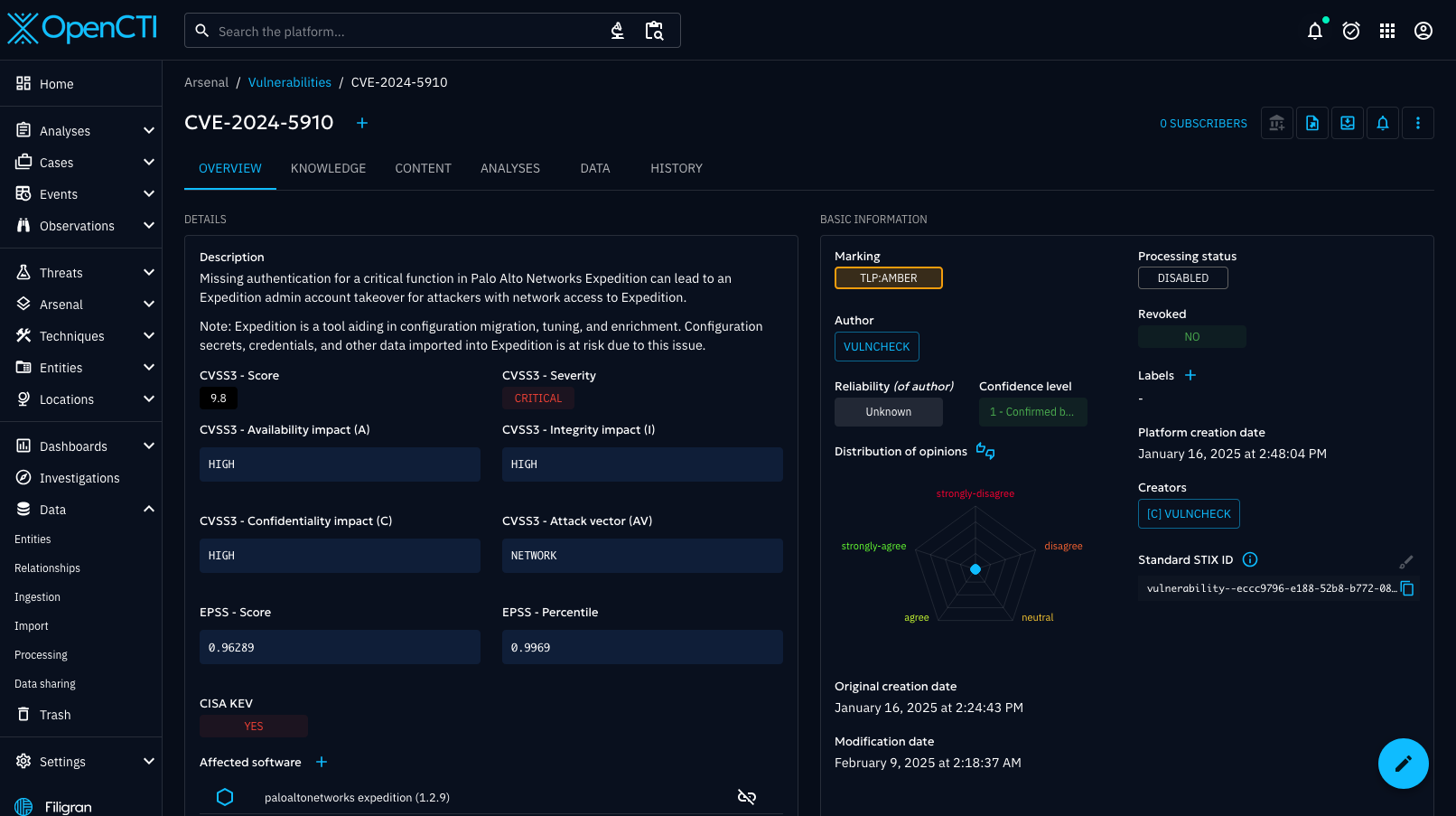
VulnCheck is expanding access to its Vulnerability and Exploit Intelligence with a new integration for OpenCTI. Now, VulnCheck customers and community members can seamlessly access VulnCheck intelligence within their OpenCTI deployment.
How it works
VulnChecks new integration is an external import connector that seamlessly integrates data from VulnChecks API, converting the data to STIX objects and importing into OpenCTI.
Currently we support several Vulncheck sources, including:
- VulnCheck KEV: Populates OpenCTI with vulnerabilities actively exploited in the wild, focusing on high-priority risks.
- VulnCheck-NVD2 / Nist-NVD2: Imports vulnerability information enriched with CVSS scores, descriptions, and associated CPEs.
- Exploits: Maps exploits to vulnerabilities and generates corresponding Malware objects in OpenCTI.
- EPSS Enrichment: Adds vulnerabilities along with their EPSS scores and percentiles, helping prioritize remediation efforts based on exploit probability.
- Ransomware: Creates Malware objects for ransomware families, linking them to associated vulnerabilities.
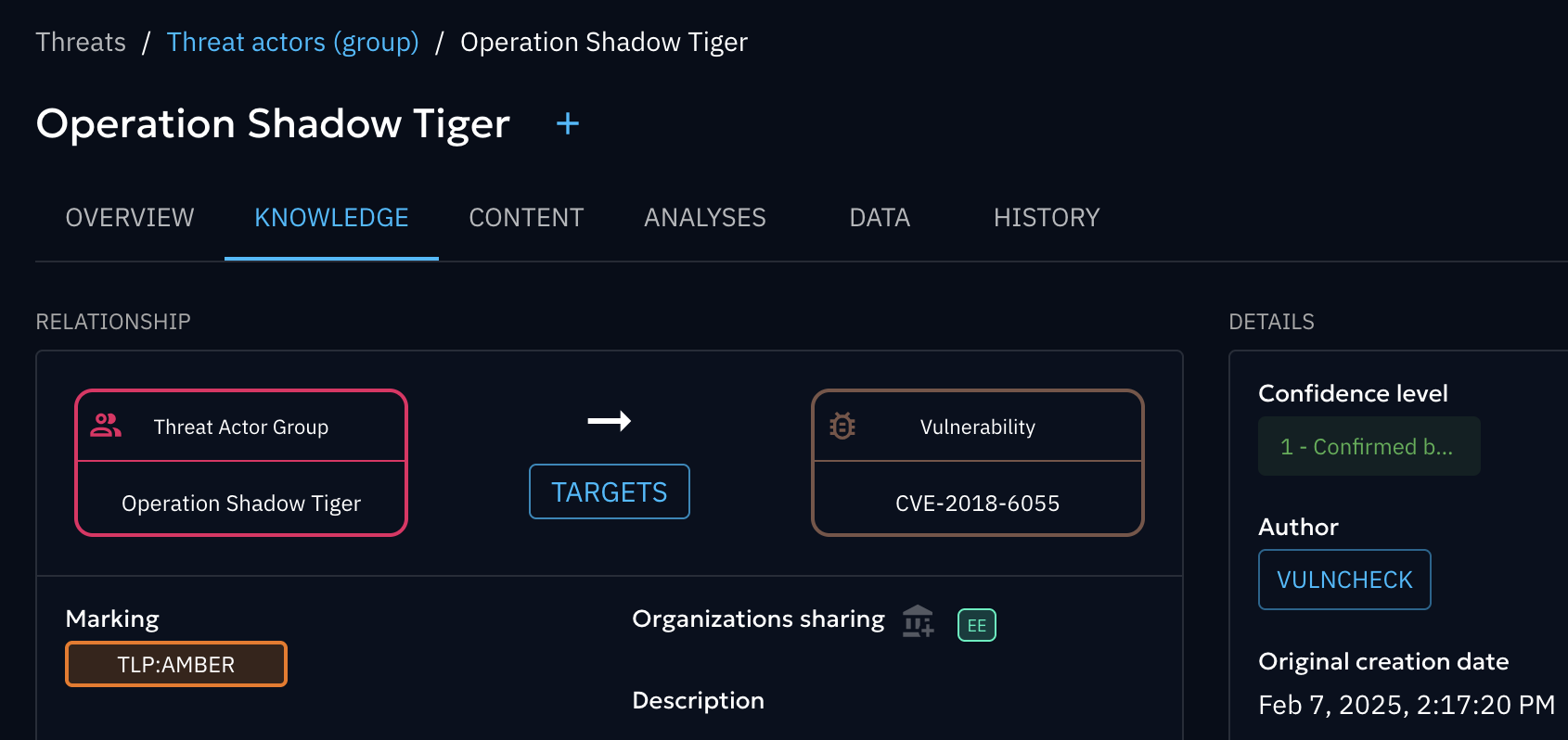
- Threat Actors: Adds Threat Actor objects with external references, relationships to targeted vulnerabilities, and descriptive metadata.
- Botnets: Ingests infrastructure data associated with botnet activities and links them to targeted vulnerabilities.
- Initial Access Indicators: Maps CPEs and vulnerabilities leveraged for initial access tactics.
- IP Intelligence: Adds infrastructure and IP-related intelligence, including countries and related vulnerabilities.
- Snort/Suricata Rules: Ingests Snort and Suricata rules as Indicators.
In aggregation with other threat intelligence providers, VulnChecks data helps create a more enriched and contextual view of the threat intelligence you care about.
How to Get Started
To get VulnCheck's connector working in your OpenCTI deployment, you'll first want to take a look at the connector's documentation. In particular the section for configuration is where you'll find optional configuration parameters for data ingestion. You can use CONNECTOR_VULNCHECK_DATA_SOURCES to filter on the indices and CONNECTOR_SCOPE to filter on the scope of STIX objects.
You can run it either as a standalone python process or in a containerized environment. Either way, you get the same threat intelligence data with the same configurable ingestion options.
For more information, check out the resources below:
About VulnCheck
VulnCheck is helping organizations not just to solve the vulnerability prioritization challenge - we’re working to help equip any product manager, security team and threat hunting team to get faster and more accurate intelligence with infinite efficiency using VulnCheck solutions.
We knew that we needed better data, faster across the board, in our industry. So that’s what we deliver to the market. We’re going to continue to deliver key insights on vulnerability management, exploitation and major trends we can extrapolate from our dataset to continuously support practitioners.
Are you interested in learning more? If so, VulnCheck's Exploit & Vulnerability Intelligence has the broadest coverage.