The National Vulnerability Database (NVD) is a crucial resource to the cybersecurity community, offering vital insights into vulnerabilities pinpointed through the Common Vulnerability Enumeration (CVE) program. Yet, recent changes at the National Institute of Standards and Technology (NIST) have hindered the timely processing of CVE data and the inclusion of essential enrichment, resulting in a discernible gap. This has spurred a collaborative endeavor to address the issue, ensuring the seamless continuation of vulnerability management efforts.
The Rise and Pause of NVD: A Turning Point
Over the last decade, the CVE program has seen a consistent increase in reported vulnerabilities annually. The NIST NVD's primary objective is to collect, refine, enhance, and disseminate information on all disclosed CVEs as a public service. The surge in volume has necessitated a corresponding expansion in NIST's operational capabilities to ensure analysis occurs at the required speed for response by vulnerability management and security teams. In particular, the analysis produces CVE enrichment including vulnerable configurations with CPEs, CVSS scores/metrics, CWE classifications, and Reference citations.
However, the unexpected pause in NVD's operations for CVE analysis and enrichment is causing concern in the cybersecurity community, jeopardizing many established processes and workflows for vulnerability management and response. What was once a reliable source of vulnerability data has recently lapsed in its pace of publication, leaving organizations struggling to find a replacement.
Key Enrichment Data
The pause in NVD's operations has delayed them adding several types of vulnerability enrichment, creating a growing backlog of newly disclosed CVEs linger in the AWAITING ANALYSIS status:
- Common Vulnerability Scoring System (CVSS) Metrics/Scoring: The universal baseline for quantitatively measuring vulnerability Severity. This is the essential starting point for calculating temporal scores and other more advanced methods for prioritizing vulnerabilities.
- Common Platform Enumeration (CPE) : The globally accepted method of declaring which vendors, products, versions, builds, hotfixes and affected platforms are affected by a given CVE expressed as “Known Affected Software Configurations”. Without this essential information, detecting and measuring exposure to known vulnerabilities is impossible.
- References: URLs provided as supplemental information, offering additional context and insights into a CVE, including Vendor advisories and fix notifications, known exploit methods and POCs, media coverage and technical briefs. These enable practitioners to classify vulnerabilities and make informed decisions about priority and response..
- Common Weakness Enumeration (CWE): Abstracts the vulnerability’s underlying weaknesses, helping with categorization, impact analysis, association with CAPEC and Mitre ATT&CK techniques, aiding analysis and mitigation..
Stepping Up: VulnCheck's Response
VulnCheck has emerged as a widely recognized source of community-accessible vulnerability intelligence, and is dedicated to ensuring publicly available information about known vulnerabilities is available to all. As part of this commitment, VulnCheck launched NVD++ on March 13, 2024, a Community-accessible service providing timely access to NIST NVD data, ensuring uninterrupted support for vulnerability management efforts.
To help close the enrichment gap for CVEs in the “Awaiting Analysis’ status, VulnCheck prioritized the generation of CPEs from reliable sources and has started adding them into the JSON available through our NVD++ service as “vcConfigurations”. Our initial release closes the gap by close to half of the current CVEs missing critical CPE data, starting with the majority of the highest prevalence vendors and products where vulnerability management teams lack the data to measure local exposure.
Our research team is investigating additional sources and prioritizing accuracy over quick coverage to expand CPE correlation in the coming weeks.
How to use VulnCheck CPE
The CPE data is represented as "vcConfigurations" and in a distinct CPE list in "vulnerableCPEs", in the following VulnCheck API indexes:
- nist-nvd2 - NVD 2.0 format, including essential data available to the VulnCheck Community tier
- nist-nvd - NVD 1.0 format, including essential data available to the VulnCheck Community tier
- Vulncheck-nvd2 - NVD 2.0 format, including premier Vulnerability & Exploit Intelligence available to VulnCheck customers
Example CPE Data:
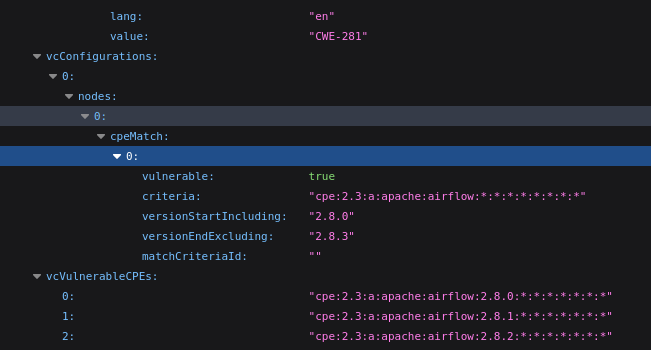
The CPE data is available for both community NVD++ and Commercial feeds. We only ask that Community user’s provide attribution to VulnCheck when our CPE data is used within another product or service.
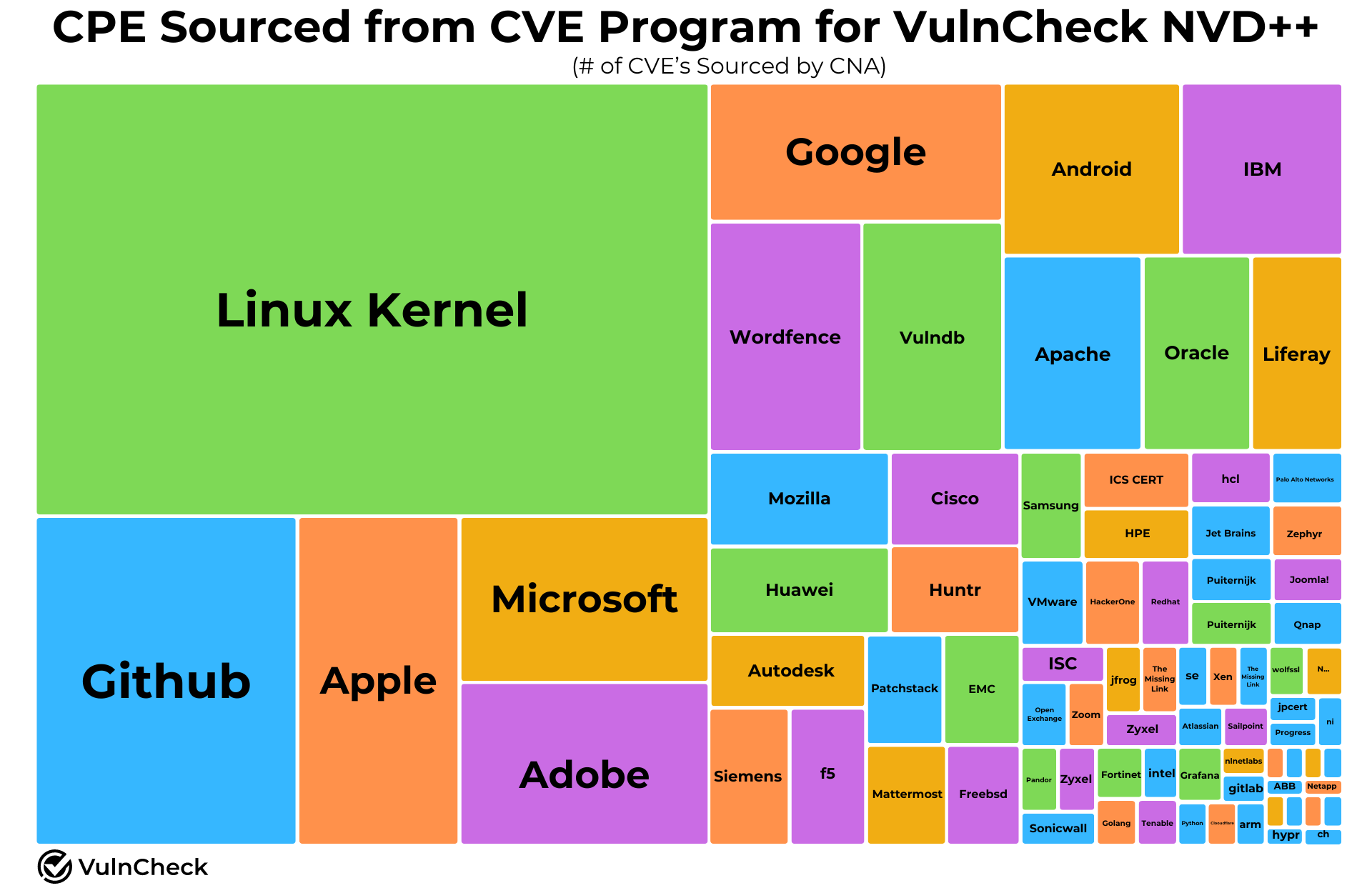
VulnCheck CPE coverage
All the vendor / product / version information we harvest is CNA provided via Mitre 5.0. All the cpe are based off of CNA provided cpe or cpe we found that matched the vendor / product in NVD. We also do cpe unrolling (where possible), which we think is a big deal.
At the current time of publishing this post VulnCheck’s CPE data covers 20% of CVE’s across the full NVD, and 40% of CVE’s awaiting coverage and we will continue to approach on these numbers as we expand our CPE coverage.

VulnCheck NVD++ provides the security community with a dependable alternative for maintaining a persistent connection to NIST NVD CVE data, empowering users with seamless and reliable access to this critical public resource.
To learn more about VulnCheck NVD++, please visit: https://vulncheck.com/nvd2
About VulnCheck
Are you interested in exploring threat actors? Do you want to track the vulnerabilities they are exploiting in the wild? If so, VulnCheck's Exploit & Vulnerability Intelligence has broad threat actor coverage. Register and demo our data today.