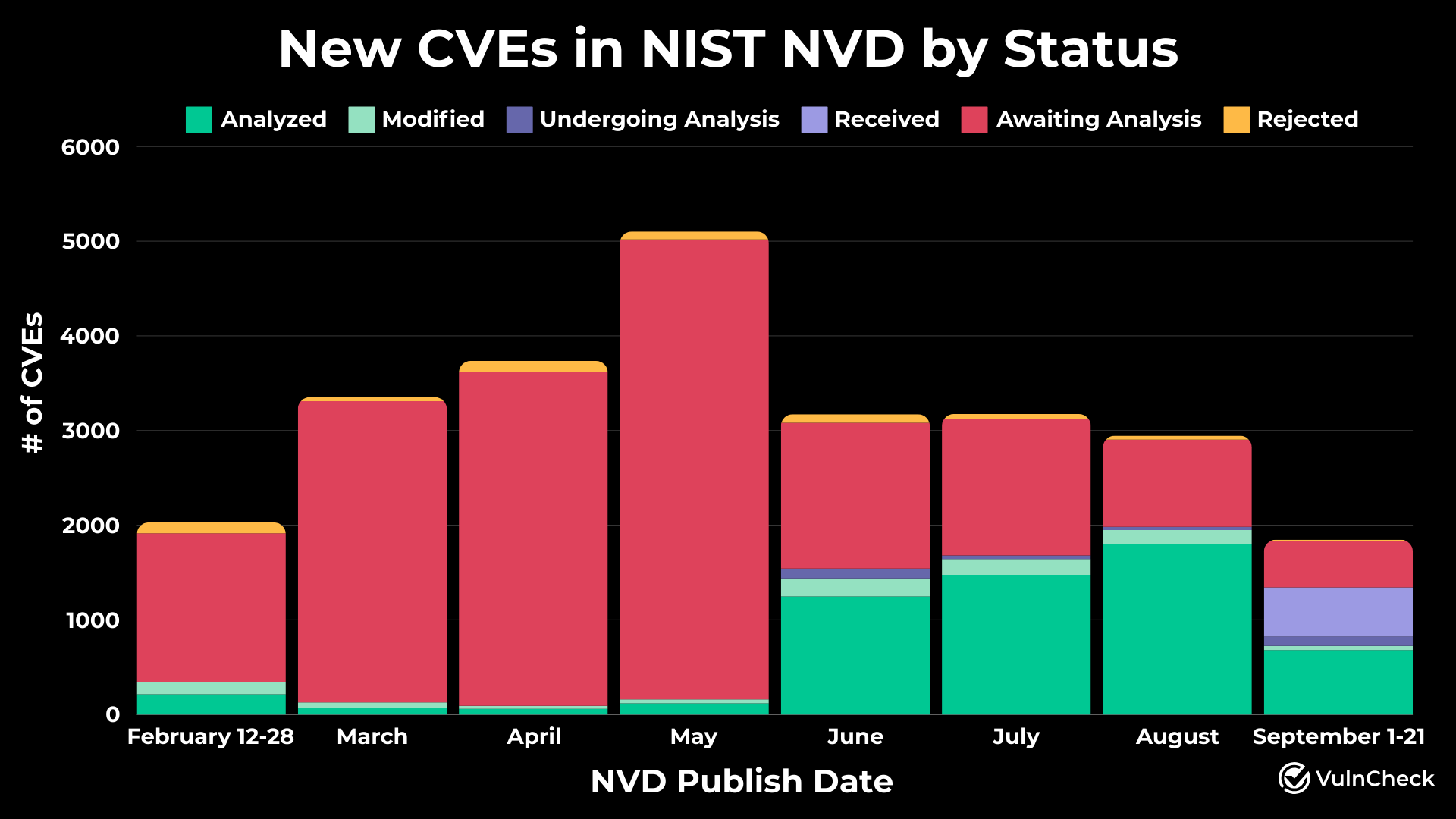
On February 12, 2024, the NVD began slowing its processing and enrichment of new vulnerabilities, resulting in a backlog of over 18,000 vulnerabilities.
On May 23, we wrote about The Real Danger Lurking in the NVD Backlog. It showed that 93.4% of new vulnerabilities had not been analyzed by the National Vulnerability Database (NVD) between February 12 and May 19, 2024.
On May 29, NIST announced that it awarded a contract to a third-party, Maryland-based Analygence, to help address the backlog. Its announcement expressed confidence that “this additional support will allow us to return to the processing rates prior to February 2024 within the next few months.” It further stated that it expects the “backlog to be cleared by the end of the fiscal year.”
That self-imposed deadline is September 30 so we thought it would be worthwhile to revisit our research to see how it’s doing against those goals.
We found a very mixed story.
As the chart above shows, since the May 29 announcement, the NIST National Vulnerability Database (NVD) has made considerable progress in processing new vulnerabilities, but a significant backlog remains. In this update, we aim to provide the security community with insights into the current state of that progress, using data sourced from both the NVD and VulnCheck’s exploit and vulnerability services. Our analysis focuses on CVEs published by the NVD between February 12 and September 21, 2024.
Key Findings
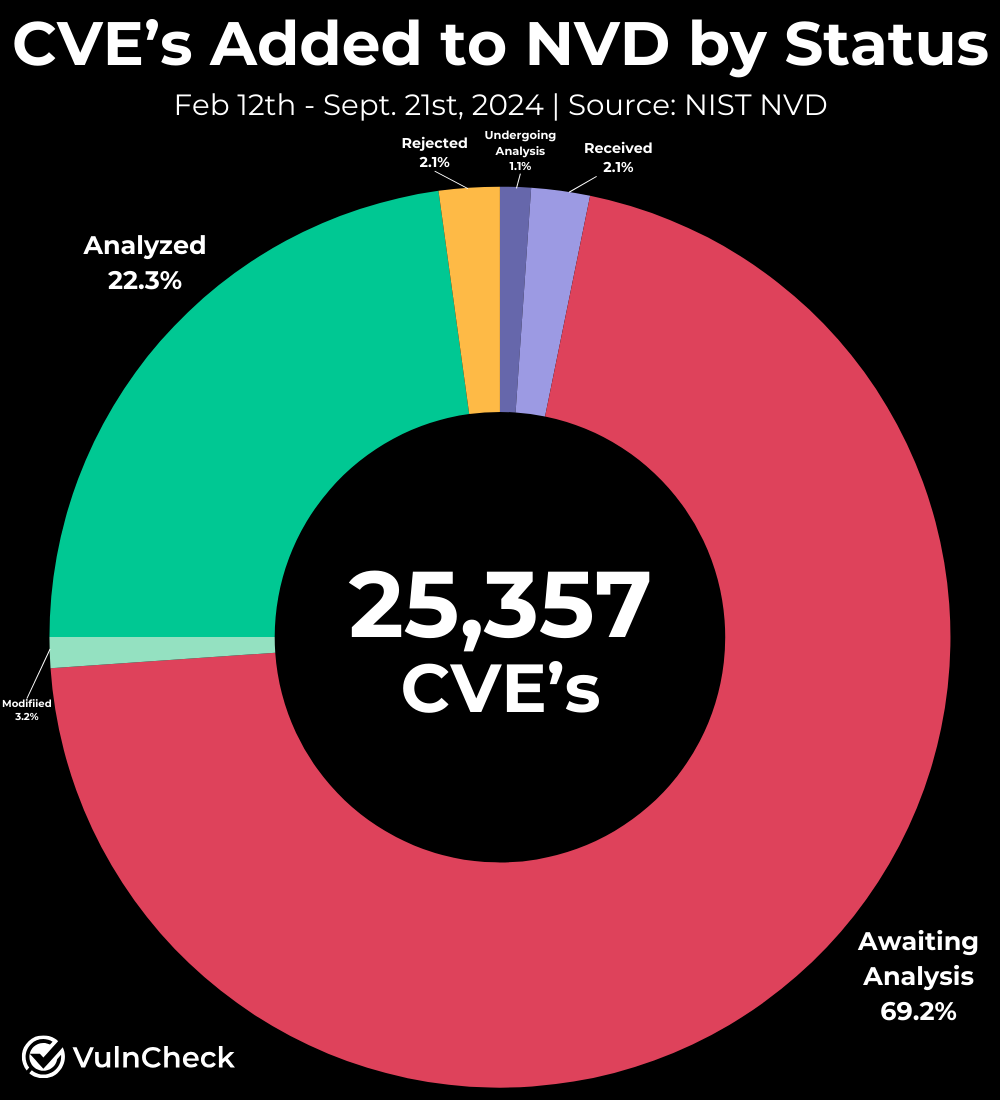
- As of September 21, 2024, 72.4% of CVEs (18,358 CVEs) in the NVD have yet to be analyzed (compared to 93.4% as of May 19, 2024).
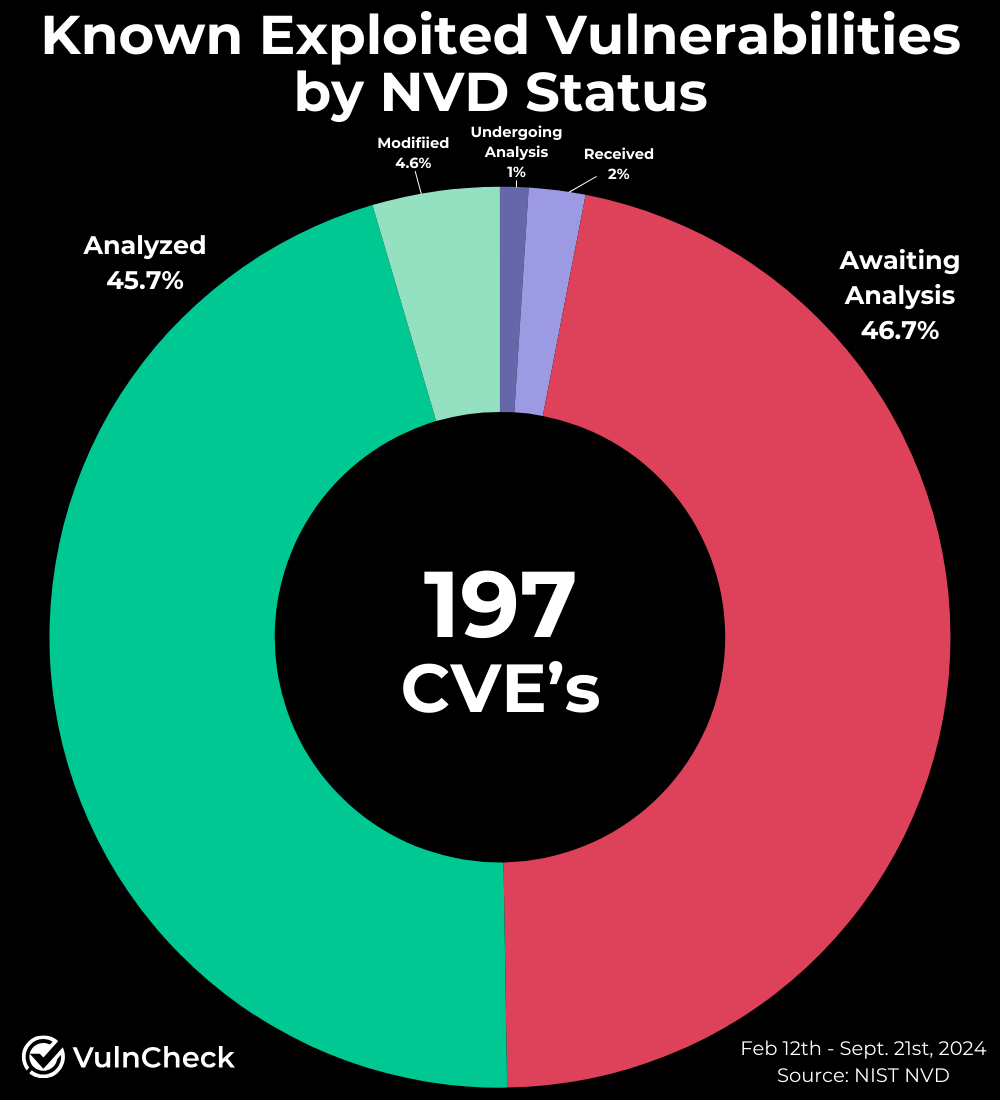
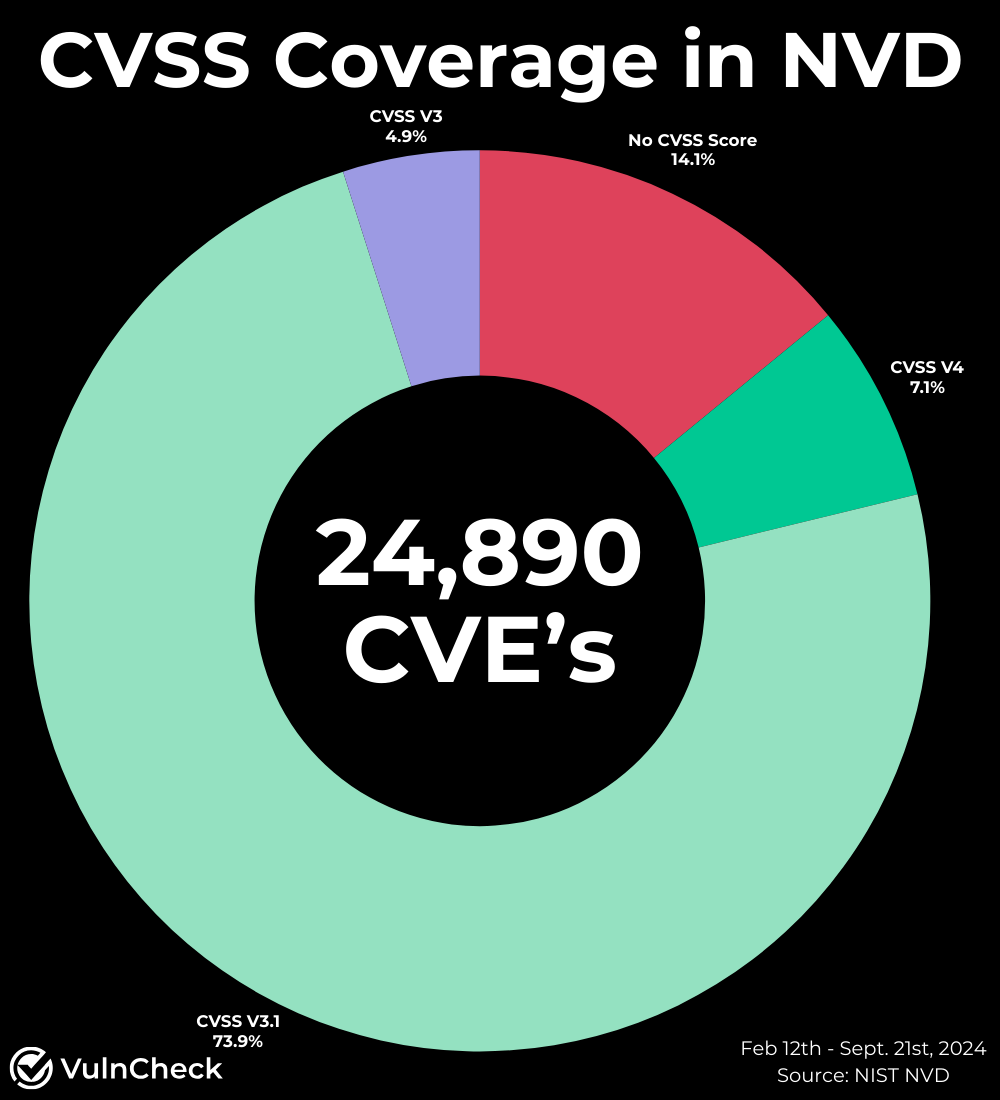
- As of September 21st, 46.7% of Known Exploited Vulnerabilities (KEVs) remain unanalyzed by the NVD (compared to 50.8% as of May 19, 2024). Of the 197 KEVs, 92 have yet to be assessed by the NVD (Source: VulnCheck KEV). A* s of September 21, 2024, 85.9% of CVEs added to the NVD since February 12 now have a CVSS record, leaving only 14.1% without a CVSS score.
- VulnCheck believes that NVD’s embrace of CISA’s Vulnrichment as a data provider for CVSS enrichment has been a notable success.
NVD Current Processing Status of CVEs Since February 12, 2024
Although our outlook for the NVD was bleak in May, when 93.4% of vulnerabilities remained unanalyzed, there has been significant progress. Of the 25,357 new vulnerabilities added to the database since February 12, 72.4% (categorized as Awaiting Analysis, Received, or Undergoing Analysis) have yet to be fully analyzed. While a substantial backlog remains, it appears the NVD might now have the capacity to keep up with enriching new CVEs as they are issued. It will be interesting how and when they address the backlog.
Unaddressed Known Exploited CVEs
As of September 20th, 46.7% of Known Exploited Vulnerabilities (KEVs) remain unanalyzed by the NVD. Of the 197 KEVs, 92 have yet to be assessed by the NVD (Source: VulnCheck KEV). In our earlier research from May, we found 50.8% (30 out of 59) of KEVs were also unanalyzed by the NVD. Many of these unanalyzed vulnerabilities that have gone unanalyzed impact key technologies such as Adobe, Arcserve, Apache, Cisco, Microsoft, Progress, VMware, Zyxel, and others.
The VulnCheck Known Exploited Vulnerabilities (KEV) catalog is a real-time resource that tracks known exploited vulnerabilities, including those from the CISA KEV list. It is available as a free community resource with publicly referenceable citations.
Common Vulnerability Scoring System Coverage
While the NVD has faced challenges in processing new vulnerabilities, CVE Numbering Authorities (CNAs) and CISA Vulnrichment have worked hard to enrich CVE records directly with CPE, CVSS, CWE and SSVC. While NVD has not incorporated all data from Vulnrichment, I’ve decided to highlight the impact of their incorporation of CVSS from Vulnrichment in addition to the CVSS scores submitted by CVE Numbering Authorities (CNA’s). To assess this progress, I analyzed CVSS coverage within the NIST NVD across primary and secondary sources. As of September 21, 2024, 85.9% of CVEs added since February 12 now have a CVSS record, leaving only 14.1% of CVEs without a CVSS score.
To understand which CNAs have the most outstanding CVEs without a CVSS score, I compiled the following table. Two CNAs stand out: Linux, which has overwhelmed the CVE program with a high volume of vulnerabilities this year, and Mitre, the Root CNA responsible for managing the CVE program.
| CVE Numbering Authority (CNA) | CVE Count w/o CVSS Score |
|---|---|
| Linux | 2172 |
| Mitre | 632 |
| Apple | 139 |
| WPscan | 135 |
| JPCert | 51 |
| Apache | 46 |
| Mozilla | 40 |
| Huawei | 39 |
| 37 | |
| Mediatek | 28 |
| Android | 27 |
| Jenkins | 17 |
| Chrome | 16 |
| Unisoc | 14 |
| Devolutions | 14 |
| HP Security | 11 |
| Joomla | 10 |
Notable Improvements Made by CVE, CNAs and CISA Enrichment
In the article The Real Danger Lurking in the NVD Backlog, we highlighted several improvements that could have a significant impact, including CNAs submitting more complete data, the NVD focusing on automating CVE enrichment, and CISA’s Vulnrichment project becoming an Authorized Data Provider. We are pleased to see these improvements taking shape, and the NVD’s embrace of Vulnrichment as a data provider for CVSS enrichment has been a notable success. It will be interesting to see if NVD follows CISA’s path and becomes an Authorized Data Provider of the CVE Program.
Another positive outcome of CISA’s Vulnrichment work is the integration of Stake-holder Specific Vulnerability Categorization(SSVC) decision nodes, now available in the CISA ADP section of the CVE List. Ben Edwards wrote an insightful article exploring this new source of prioritization information: Do We Need Yet Another Vulnerability Scoring System? For SSVC, That's a YASS!
VulnCheck's Commitment to Helping Fill the NVD Gap
Regardless of the uncertainty, VulnCheck is committed to contributing back to the security community. VulnCheck is providing vulnerability enrichment services, including CPE and access to NIST-NVD from a single source at no cost. Anyone can register for the free service here: https://vulncheck.com/community.
VulnCheck also provides a commercial service with broad access to vulnerability and exploit intelligence,including: Vulnerabilities in Open Source packages / dependencies, Vulnerabilities in ICS/OT, IoMT, IoT, mobile, etc., devices, Git repositories for new exploit PoCs, Caching of exploit PoCs, Exploit Maturity classification, Exploit Type classification, Evidence of exploitation in-the-wild & exploitation timelines and more.
About VulnCheck
VulnCheck is helping organizations not just to solve the vulnerability prioritization challenge - we’re working to help equip any product manager, CSIRT/PSIRT or SecOps team and Threat Hunting team to get faster and more accurate with infinite efficiency using VulnCheck solutions.
We knew that we needed better data, faster across the board, in our industry. So that’s what we deliver to the market. We’re going to continue to deliver key insights on vulnerability management, exploitation and major trends we can extrapolate from our dataset to continuously support practitioners.
Are you interested in learning more? If so, VulnCheck's Exploit & Vulnerability Intelligence has broad threat actor coverage. Register and demo our data today.