In recent weeks, our KEV (Known Exploited Vulnerabilities) feed has seen a notable increase in CVEs. If you've noticed and are wondering what's driving the spike, you're not alone. The short answer: VulnCheck has been hard at work closing the gap on untracked exploitation by auditing publicly available sources and assigning CVEs where none existed. Here's a look behind the scenes at what’s been happening.
Why the Spike in CVEs?
Two major developments contributed to the increase:
- Auditing ShadowServer for Unassigned CVEs We performed an extensive audit of ShadowServer's daily detection snapshots. During this process, we identified vulnerabilities with active detections but no associated CVE ID, a major blind spot for defenders relying on structured vulnerability intelligence. Rather than let these gaps persist, we tracked down the original advisories and/or exploit proof-of-concepts and issued CVEs ourselves. In total, we contributed 30+ new CVEs through this audit process where exploitation evidence existed.
These vulnerabilities span a range of high-risk technologies, including camera systems, network edge devices, and content management systems—frequent targets for botnets and threat actors. Notable vendors affected include Hikvision, D-Link, AVTech, Dahua, Linksys, , TVT, SugarCRM, Edimax, among others. Many of the issues we identified are older, unpatched flaws in widely deployed technologies, often originating from Chinese manufacturers. Details on each of these CVEs can be found in our advisory archive here: https://vulncheck.com/advisories.
- Introduction of CrowdSec as a Source We've added CrowdSec’s public exploitation evidence as a new exploitation reference source within VulnCheck KEV. We continuously seek high-signal, reliable public sources of exploitation evidence, and CrowdSec fits the bill. This resulted in the addition of 70+ vulnerabilities to VulnCheck KEV that we didn’t already have exploitation evidence for.
Expanding the CVE Ecosystem
VulnCheck’s role here isn't limited to aggregation. When we find credible exploitation without a CVE, we treat that as a security intelligence failure, and we act. Our Process:
Daily ShadowServer Snapshot Analysis We continuously ingest detection telemetry and flag items lacking CVE attribution.
Manual Verification For each flagged issue, we identify relevant advisories or exploits.
CVE Assignment When warranted, we submit and assign a CVE through the appropriate channels. This also involves coordination with CNAs (CVE numbering authorities) with the most appropriate scope. This includes close coordination with Mitre and the new CVE research working group that was recently formed.
This proactive CVE assignment strategy isn't exclusive to ShadowServer; we're also auditing Metasploit and ExploitDB in a similar manner, so the riskiest vulnerabilities that were overlooked receive a CVE.
This highlights our commitment to the success of the CVE Program.
Meet the Team Behind It
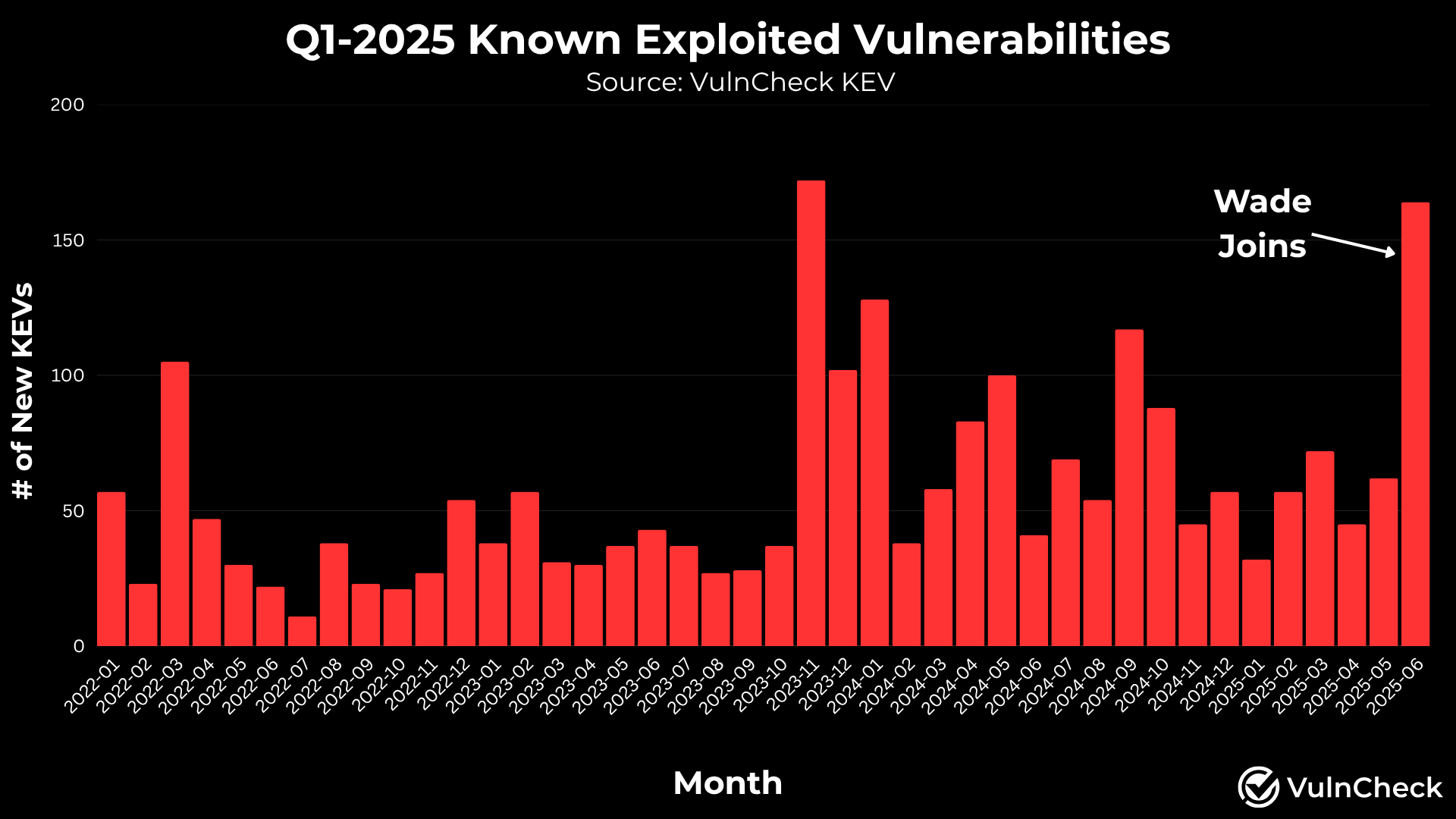
This initiative was spearheaded by our vulnerability intelligence team, including recent hire Wade Sparks III, formerly of the CISA KEV team. Wade has been instrumental in streamlining CVE submissions and bringing field-tested experience to our approach.
What’s Next?
While the ShadowServer audit is nearing completion, we expect the spike in volume will taper off, our work is far from over. Next up:
Metasploit & ExploitDB Audits: Ongoing efforts to catch more untracked, higher risk vulnerabilities with readily available exploits.
More CVE Assignments: We’re committed to assigning CVE IDs to vulnerabilities that pose high risk, so they appear in scanners, dashboards, and security tools worldwide.
Follow Our Work & Get Alerted
You can always view the latest advisories at: https://vulncheck.com/advisories
Subscribe for free to VulnCheck KEV alerts and get alerted via Email or Slack each time we add a new KEV.
About VulnCheck
VulnCheck is helping organizations not just to solve the vulnerability prioritization challenge - we’re working to help equip any product manager, security team and threat hunting team to get faster and more accurate intelligence with infinite efficiency using VulnCheck solutions. We knew that defenders needed better data, faster across the board, in our industry. So that’s what we deliver to the market. We deliver key insights on vulnerability management, exploitation and major trends we can extrapolate from our dataset to continuously support practitioners.
Join the VulnCheck Community today and get access to our VulnCheck NVD++ and the VulnCheck KEV in 30 seconds or less.