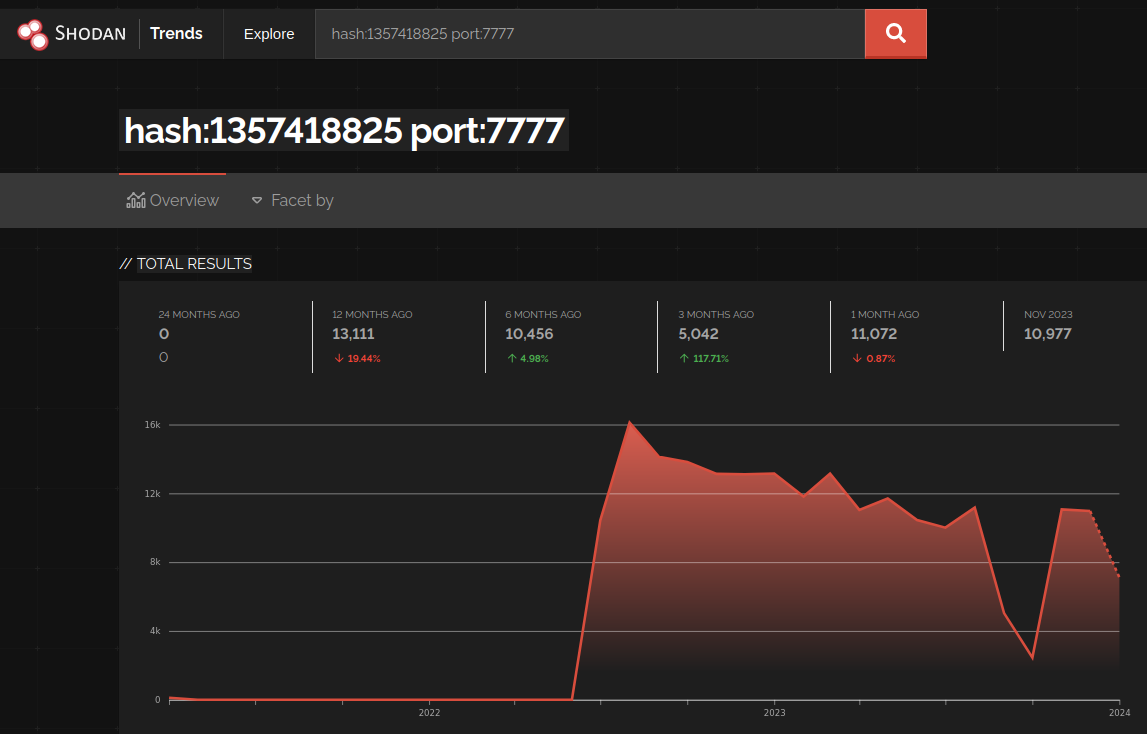
7777-Botnet Infection Vectors
Introduction
In October 2023, the 7777-Botnet was first discussed in a writeup titled, The Curious Case of the 7777-Botnet. The author, supported by other researchers, describes a ~10,000 node botnet that's purpose is to brute-force Microsoft Azure user credentials. It employs targeted, low-volume methods that are so effective that they were only discovered due to a geolocation login anomaly. The botnet’s targets include VIP users from organizations within the United States and Europe. Additionally, the writeup details loose links to the well-known threat actors Scattered Spider and Lazarus, based on reports from CrowdStrike and ReversingLabs respectively. The botnet, which has a fairly-distinct signature, remains active.
Xiongmai Infections
However, little is known about how the botnet infects new hosts. Looking through our IP intelligence data, we can see it co-located with software with known vulnerabilities. This can give us a good idea of the potential vulnerabilities that the botnet is using to infect new nodes. Take, for example, this 7777-Botnet installation on a Xiongmai device detailed in our IP-intelligence dataset:
{"ip":"1.34.97.9","port":7777,"ssl":false,"lastSeen":"2024-01-15T13:08:10.811693","asn":"AS3462","country":"Taiwan","country_code":"TW","city":"Hsinchu","cve":[],"matches":["7777Botnet"],"hostnames":["1-34-97-9.hinet-ip.hinet.net"],"type":{"id":"c2","finding":"command and control infrastructure"},"feed_ids":["e738e65a-6e88-4ad3-a922-55d32e57d4e7"]}
{"ip":"1.34.97.9","port":81,"ssl":false,"lastSeen":"2024-01-14T15:33:16.045105","asn":"AS3462","country":"Taiwan","country_code":"TW","city":"Hsinchu","cve":["CVE-2017-7577","CVE-2018-10088","CVE-2022-45460"],"matches":["Xiongmai Path Traversal Credential Leak","Xiongmai Authentication Buffer Overflow","Xiongmai URI Buffer Overlow"],"hostnames":["1-34-97-9.hinet-ip.hinet.net"],"type":{"id":"initial-access","finding":"potentially vulnerable"},"feed_ids":["876acbdf-ab92-46d7-bfcd-8d11e77baf0c","2025c398-1336-46f7-8ae3-3a0eea75ed61","54dde2a2-54ca-48ce-aa12-8823dc2f82d9"]}
For those less inclined to look at JSON, you can also observe the installation on Shodan:
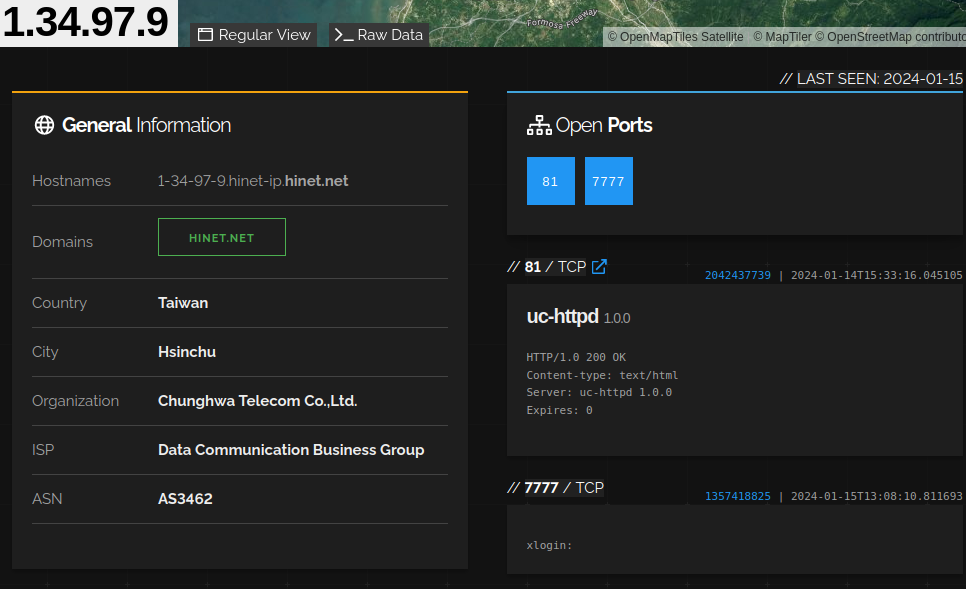
As we can see, the botnet is co-located with a Xiongmai NVR/IP camera’s HTTP server. In our IP intelligence JSON, we are able to correlate three known vulnerabilities this server is affected by: CVE-2017-7577, CVE-2018-10088, and CVE-2022-45460. All of these are well-known vulnerabilities with public exploits found in Routersploit, Exploit-DB, and on GitHub. CVE-2018-10888, in particular, is already associated with the Satori, Hajime, and BotenaGo botnets.
As we detailed in our November 2022 blog, Xiongmai IoT Exploitation, the volume of devices vulnerable to these CVE is still reasonably high. And while new Xiongmai vulnerabilities have popped up in recent years (e.g. CVE-2022-26259), the exposed interfaces and lower volume of Xiongmai devices exploited 7777-Botnet suggests older vulnerabilities are being used. As such, it’s entirely reasonable to assume that 7777-Botnet is leveraging one of (if not all), CVE-2017-7577, CVE-2018-10088, and CVE-2022-45460. This isn’t a fact, but a reasonable guess based on the information in front of us.
Hikvision Infections
A similar pattern we see in our IP intelligence data is 7777-Botnet co-located with Hikvision cameras (and OEM derivatives). The botnet is likely using CVE-2021-36260 to infect these targets. This idea is bolstered by the fact that a majority of infected cameras are still using affected versions:
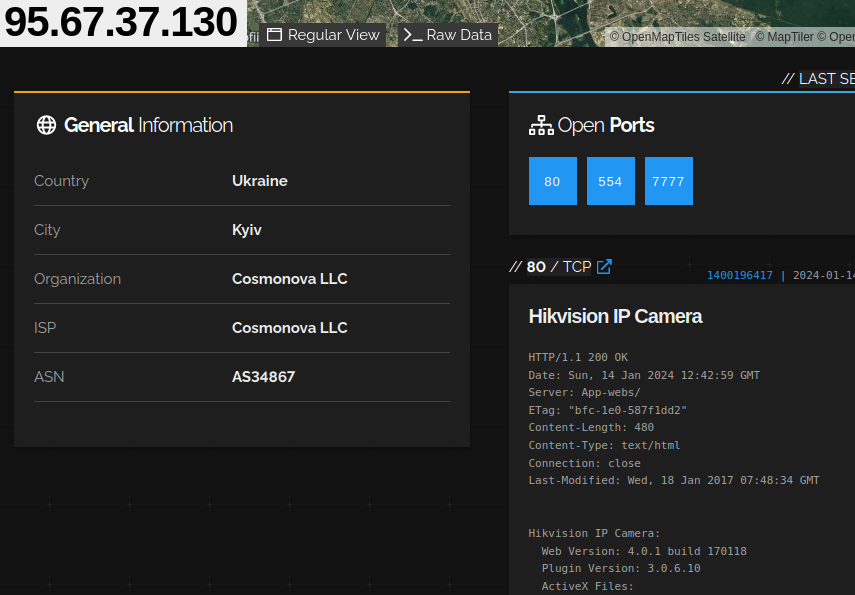
CVE-2021-36260 is a very well-known vulnerability. VulnCheck tracks 23 public exploits for this vulnerability, including a Metasploit module. The vulnerability is included in CISA’s Known Exploited Vulnerabilities Catalog (KEV), and they included it in their “Top CVEs Actively Exploited By People’s Republic of China State-Sponsored Cyber Actors” list. CVE-2021-36260 is already associated with botnets Zerobot and Moobot Finally, CVE-2021-36260 is actively detected in the Shadow Server and GreyNoise honeypot networks.
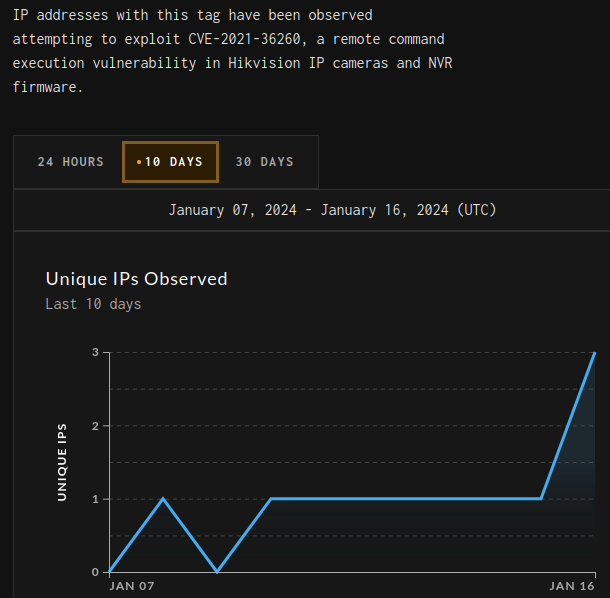
Given all that background, it again seems reasonable to theorize that the botnet is spreading to Hikvision cameras using CVE-2021-36260. Even as the vulnerability gets older, there continues to remain thousands of vulnerable targets, appearing to correlate directly with the botnet’s infection rates
TP-Link Infections
Another set of targets the botnet seems to go after are TP-Link routers. We observe the botnet co-hosted with the web interface for the following models: WR740N, WR840N, WR841N, WR940N, WR941ND, and a much smaller subset of Archer infections.
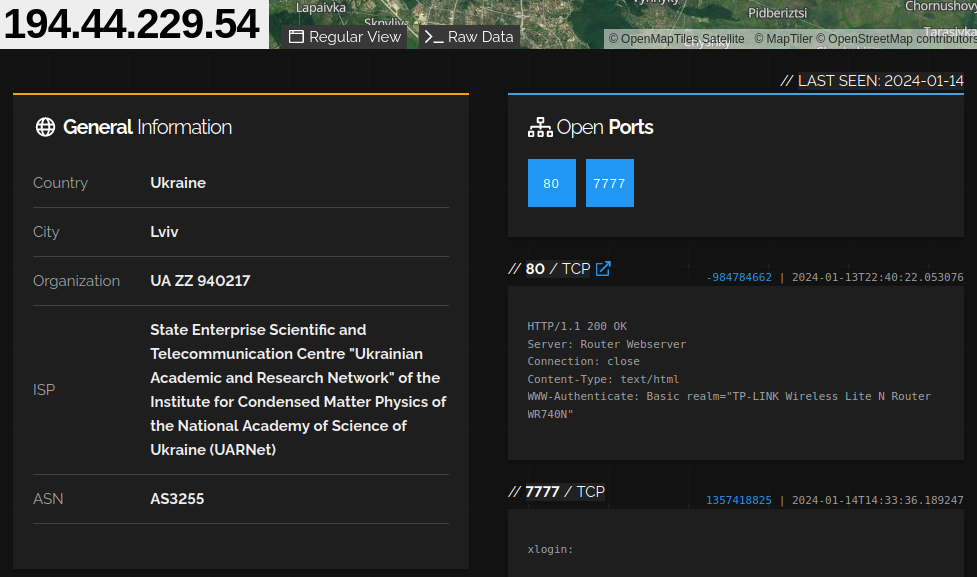
The infected routers are all older, having not received any updates since 2022 (and one not receiving an update since 2019). It’s difficult to pin a single vulnerability on this group because TP-Link either creates CVEs with useless descriptions or doesn’t create any at all. Their release notes hardly shed light on the situation either.
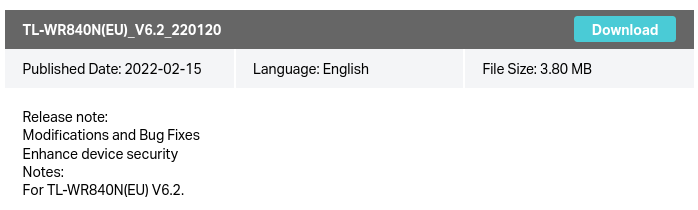
However, CVE-2022-24355 seems a reasonable candidate. It doesn’t require authentication, and public exploits have been developed for the WR940N and WR841N.
There are more well-known TP-Link vulnerabilities that affect these models, such as CVE-2021-41653. But these exploits seem to require valid credentials to exploit the target. It is certainly a possibility that there are routers using default credentials or that 7777-botnet is brute-forcing credentials, but there is no evidence to support that. As such, CVE-2022-24355 seems like the most straightforward possibility - although it is little more than an educated guess.
Other Infections and SOCKS5
We also see the 7777-Botnet on systems without TP-Link, Xiongmai, or Hikvision present, although at a significantly lower volume (which might indicate these are just honeypots, it’s hard to say). We see the botnet co-located with MVPower (CVE-2016-20016), Zyxel NAS (CVE-2020-9054), and GitLab (CVE-2021-22205).
We also observed that the botnet often spins up a SOCKS5 server on port 11288. We uncovered this, again, by monitoring co-located services. Shodan doesn’t capture this behavior, but our friends over at Censys can visualize it for us.
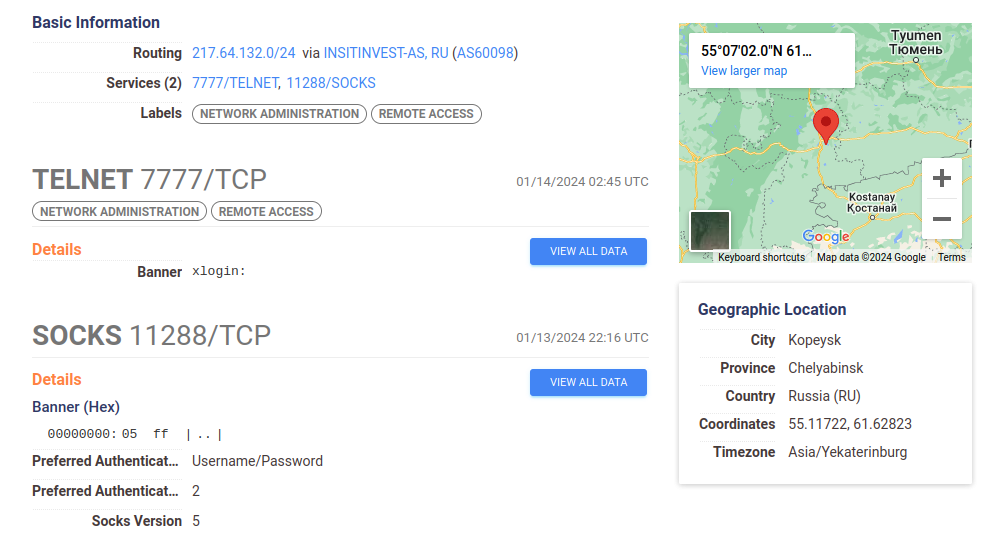
This is an interesting feature of the botnet that was not described in the original writeup and indicates it might have a larger role in the attacker’s infrastructure.
Conclusion
The 7777-Botnet is an active botnet, and speculating how it spreads to new systems helps researchers begin to understand how to dismantle the botnet and also provides defenders with actionable steps to defend against infection. Using known vulnerabilities on co-located services, we hypothesize five different CVE that the botnet might be using to spread to TP-Link, Xiongmai, and Hikvision devices, and we suggest a few CVE for more low-volume infections.
While the botnet isn’t well-known, it is easy enough to protect your networks from it. Ensure that you isolate infected hosts, remediating the potentially exploited CVE, and validate that no additional infected devices exist in your network. Further, be sure to inventory devices for unnecessary internet exposure, and place them behind appropriate security controls.
About VulnCheck and IP Intelligence
This analysis comes out of VulnCheck's IP Intelligence capability, which is now generally available in our Initial Access Intelligence product. Sign up to trial our data by using the Register and Schedule Demo buttons at the top right corner of our website.