VulnCheck Initial Access Intelligence equips organizations and security teams with detection artifacts including Suricata signatures, YARA rules, PCAPs, and private exploit PoCs to defend against initial access vulnerabilities that are either already being exploited or likely to be exploited soon.
In September 2024, VulnCheck crossed 290+ Initial Access Intelligence (IAI) artifacts, developing artifacts for 16 CVEs, covering 14 different vendors and products. 7 of the 14 have confirmed exploitation activity as of October 7th, 2024.
Notably, we added IAI coverage for CVE-2023-50386, CVE-2019-7256, and CVE-2023-35843 which were discovered to be a target of the recently reported Flax Typhoon Botnet and continue to expand our coverage of the CVEs targeted by this botnet.
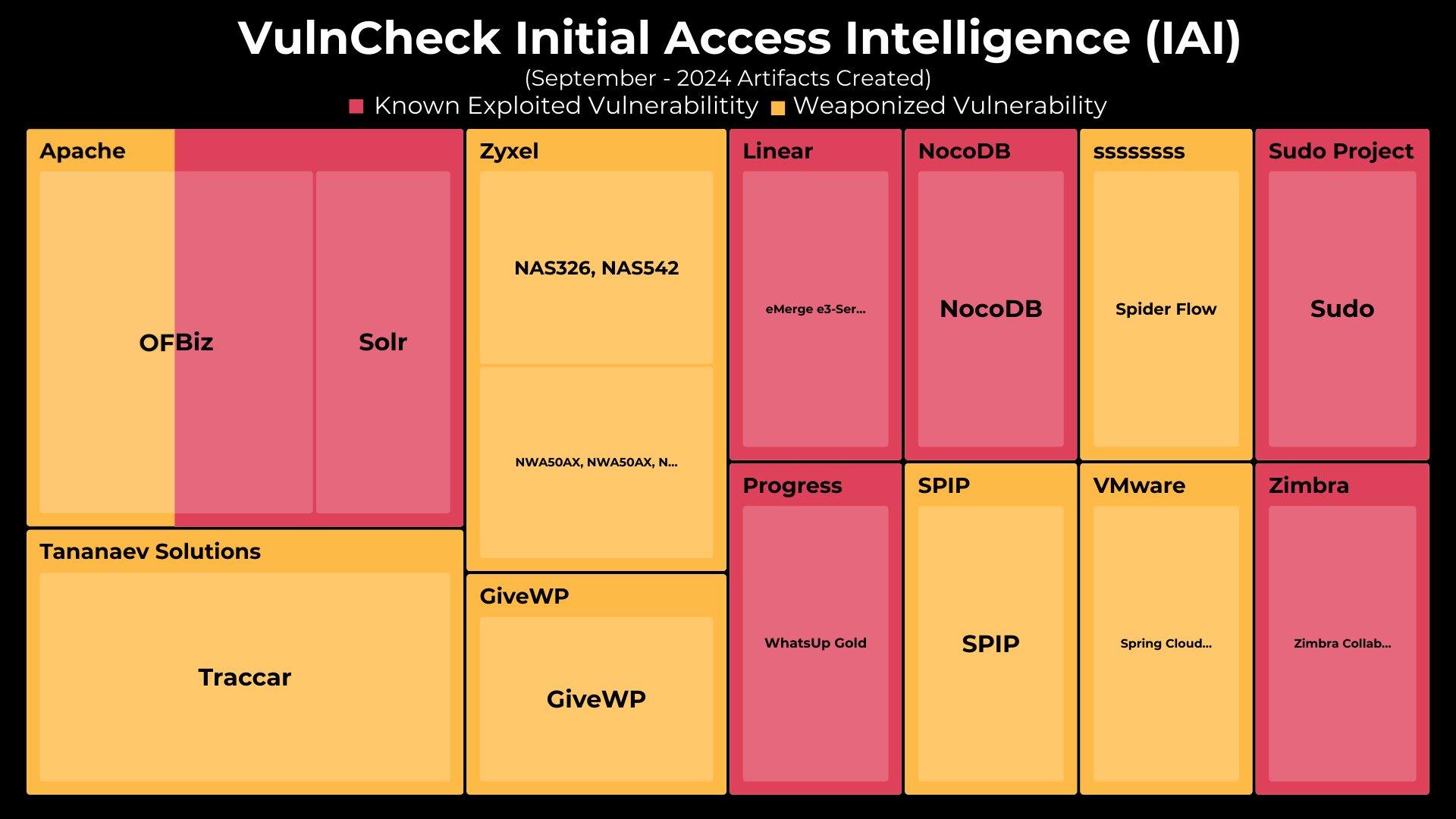
To provide better visibility into these updates, we’ve broken down September’s Initial Access Intelligence Artifacts by CVE. For each CVE, we provide a range of detection tools including:
- Exploits
- Version scanners
- PCAPs
- Suricata rules
- Snort rules
- YARA rules
- Greynoise/Censys/Shodan queries
September 2024 Initial Access Artifacts
| Artifact Name | Date Added | CVE | Exploit | Version Scanner | pcap | Suricata Rule | snortRule | yara |
|---|---|---|---|---|---|---|---|---|
| Traccar Image Upload Path Traversal RCE | 2024-09-05 | CVE-2024-24809 | ✅ | ✅ | ✅ | ✅ | ✅ | |
| Traccar Unrestricted File Upload | 2024-09-05 | CVE-2024-31214 | ✅ | ✅ | ✅ | ✅ | ✅ | |
| GiveWP Remote Code Execution | 2024-09-06 | CVE-2024-5932 | ✅ | ✅ | ✅ | ✅ | ✅ | |
| Apache OFBiz CSV Data File Webshell | 2024-09-10 | CVE-2024-45195 | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ |
| Zyxel nebula_ap_redirect Crash | 2024-09-11 | CVE-2024-7261 | ✅ | ✅ | ✅ | |||
| ssssssss Spider Flow Command Injection | 2024-09-12 | CVE-2024-0195 | ✅ | ✅ | ✅ | ✅ | ✅ | |
| Zyxel NAS Auth Bypass and Configuration Leak | 2024-09-12 | CVE-2024-6342 | ✅ | ✅ | ✅ | ✅ | ✅ | |
| SPIP Bigup Plugin Remote Code Execution | 2024-09-12 | CVE-2024-8517 | ✅ | ✅ | ✅ | ✅ | ✅ | |
| Apache OFBiz Stats Screen SSRF | 2024-09-18 | CVE-2024-45507 | ✅ | ✅ | ✅ | ✅ | ✅ | |
| Progress WhatsUp Gold SQL Injection | 2024-09-20 | CVE-2024-6670 | ✅ | ✅ | ✅ | ✅ | ✅ | |
| Sudo Heap-based Overflow "Baron Samedit" Local Privilege Escalation | 2024-09-25 | CVE-2021-3156 | ✅ | ✅ | ||||
| Apache Solr Configuration Backup RCE | 2024-09-25 | CVE-2023-50386 | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ |
| Linear eMerge e3-Series ReaderNo Command Injection | 2024-09-26 | CVE-2019-7256 | ✅ | ✅ | ✅ | |||
| Spring Cloud Data Flow Remote Code Execution | 2024-09-26 | CVE-2024-37084 | ✅ | ✅ | ✅ | |||
| NocoDB Path Traversal | 2024-09-27 | CVE-2023-35843 | ✅ | ✅ | ✅ | ✅ | ||
| Zimbra RCPT TO Command Injection | 2024-09-30 | CVE-2024-45519 | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ |
Go Exploit Framework
VulnCheck's exploit proof of concept (PoC) and version scanner code is written in the Go programming language. They are provided with a Dockerfile for ease of use. The exploits leverage an Open Source Software (OSS) shared library, which VulnCheck has authored and maintains, called go-exploit.
Learn More About VulnCheck Initial Access Intelligence
Learn more about how you can leverage Initial Access Intelligence detection artifacts to detect & respond to remote code execution (RCE) vulnerabilities here: https://docs.vulncheck.com/products/initial-access-intelligence/introduction