VulnCheck Initial Access Intelligence equips organizations and security teams with detection artifacts including Suricata signatures, YARA rules, PCAPs, and private exploit PoCs to defend against initial access vulnerabilities that are either already being exploited or likely to be exploited soon.
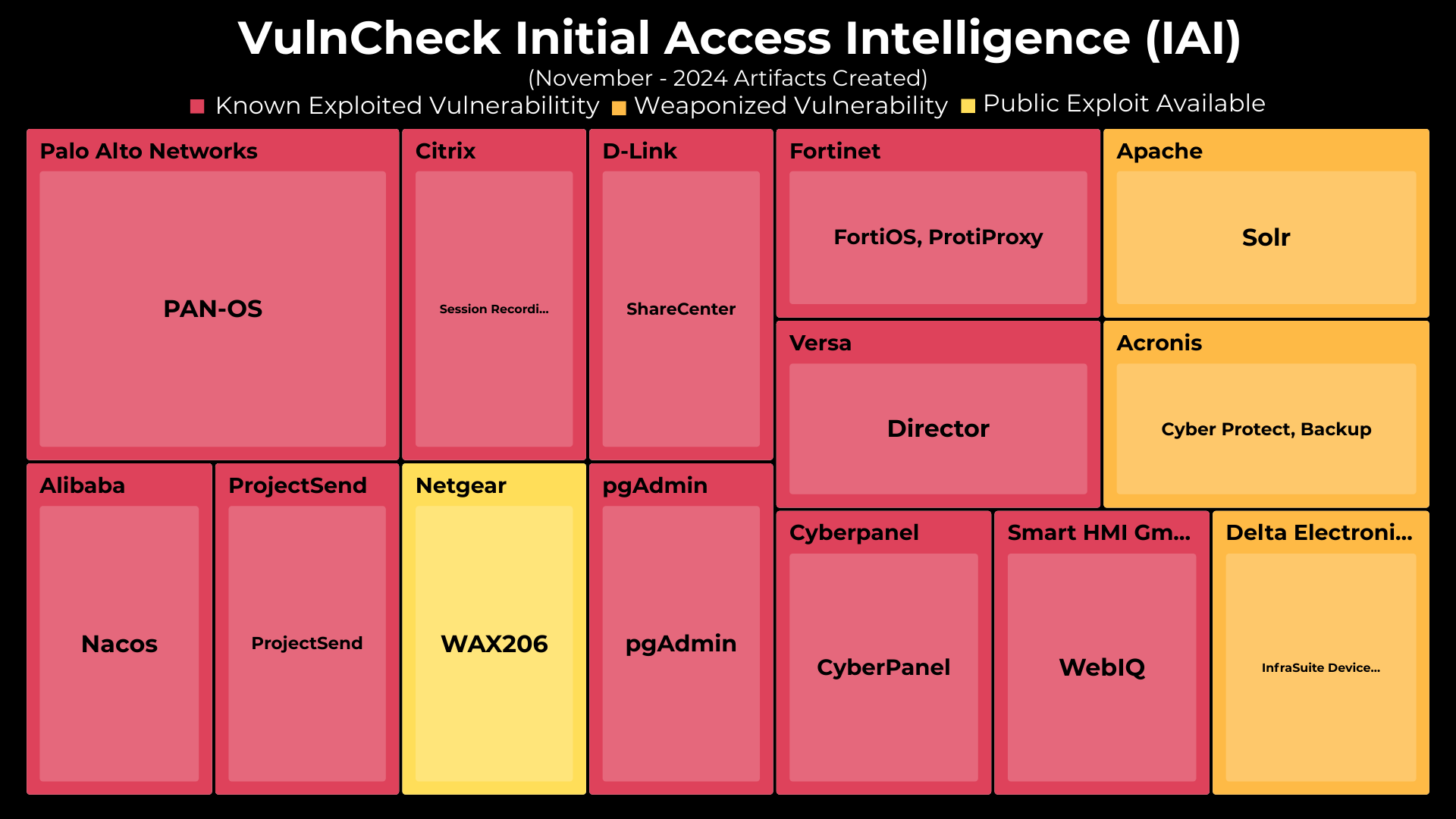
In November 2024, VulnCheck released Initial Access Intelligence (IAI) artifacts for 15 CVEs, covering 14 different vendors and products. 11 of the 14 have confirmed exploitation activity as of December 11th, 2024. The release of these detection artifacts include widely used edge devices from vendors including Palo Alto, Citrix, D-Link, Fortinet and Netgear.
ProjectSend Exploitation Discovery
In November we discovered public-facing ProjectSend instances that appeared to have been exploited by attackers. As of November 25th, 99% of ProjectSend instances remained vulnerable and have not upgraded to the patched version released in August. Public exploits have pre-dated CVE assignment by months, including Nuclei templates and a weaponized Metasploit module. So we issued a CVE and released our research and initial artifacts for the vulnerability. Learn more about the research in our Project Send Blog Post
Initial Access Intelligence - November Breakdown
To provide better visibility into these updates, we’ve broken down November’s Initial Access Intelligence Artifacts by CVE. For each CVE, we provide a range of detection tools including:
- Exploits
- Version scanners
- PCAPs
- Suricata rules
- Snort rules
- YARA rules
- Greynoise/Censys/Shodan/FOFA/ZoomEye Queries
- Target Docker Containers
November 2024 Initial Access Artifacts
| Artifact Name | Date Added | cve | Exploit | Version Scanner | pcap | Suricata Rule | Snort Rule | Yara |
|---|---|---|---|---|---|---|---|---|
| Derby SQL based RCE | 2024-11 | CVE-2021-29442 | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ |
| ProjectSend Incorrect Authorization Webshell Upload | 2024-11 | CVE-2024-11680 | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ |
| Palo Alto Networks PAN-OS Management Interface Authentication Bypass Vulnerability | 2024-11 | CVE-2024-0012 | ✅ | ✅ | ✅ | ✅ | ✅ | |
| Palo Alto Networks PAN-OS Management Interface Command Injection Vulnerability | 2024-11 | CVE-2024-9474 | ✅ | ✅ | ✅ | ✅ | ✅ | |
| Citrix Session Recording (Virtual Apps and Desktops) .NET Deserialization | 2024-11 | CVE-2024-8069 | ✅ | ✅ | ✅ | ✅ | ||
| D-Link ShareCenter Command Injection | 2024-11 | CVE-2024-10914 | ✅ | ✅ | ✅ | ✅ | ✅ | |
| Netgear WAX206 | 2024-11 | CVE-2024-20017 | ✅ | |||||
| pgAdmin OAuth2 Information Disclosure | 2024-11 | CVE-2024-9014 | ✅ | ✅ | ✅ | ✅ | ✅ | |
| Fortinet FortiOS Out-of-Bound Write | 2024-11 | CVE-2024-21762 | ✅ | ✅ | ✅ | |||
| Versa Director Favicon Upload (authenticated) | 2024-11 | CVE-2024-39717 | ||||||
| Apache Solr Authentication Bypass | 2024-11 | CVE-2024-45216 | ✅ | ✅ | ✅ | ✅ | ✅ | |
| Acronis Cyber Protect Unauthenticated RCE | 2024-11 | CVE-2022-3405 | ✅ | ✅ | ✅ | ✅ | ||
| CyberPanel OPTIONS Command Injection | 2024-11 | CVE-2024-51378 | ✅ | ✅ | ✅ | ✅ | ||
| Smart HMI WebIQ File Leak | 2024-11 | CVE-2024-8752 | ✅ | ✅ | ✅ | ✅ | ✅ | |
| Delta Electronics InfraSuite Device Master Deserialization | 2024-11 | CVE-2023-47207 | ✅ | ✅ | ✅ | ✅ |
Go Exploit Framework
In October, we expanded the capabilities of go-exploit to include a new command and control feature called ShellTunnel which captures reverse shell traffic and routes it through an intermediary attacker-controlled server before reaching the main C2 server. https://vulncheck.com/blog/go-exploit-shelltunnel
For those new to go-exploit, VulnCheck's exploit proof of concept (PoC) and version scanner code is written in the Go programming language. They are provided with a Dockerfile for ease of use. The exploits leverage an Open Source Software (OSS) shared library, which VulnCheck has authored and maintains, called go-exploit.
Learn More About VulnCheck Initial Access Intelligence
Learn more about how you can leverage Initial Access Intelligence detection artifacts to detect & respond to remote code execution (RCE) vulnerabilities here: https://docs.vulncheck.com/products/initial-access-intelligence/introduction