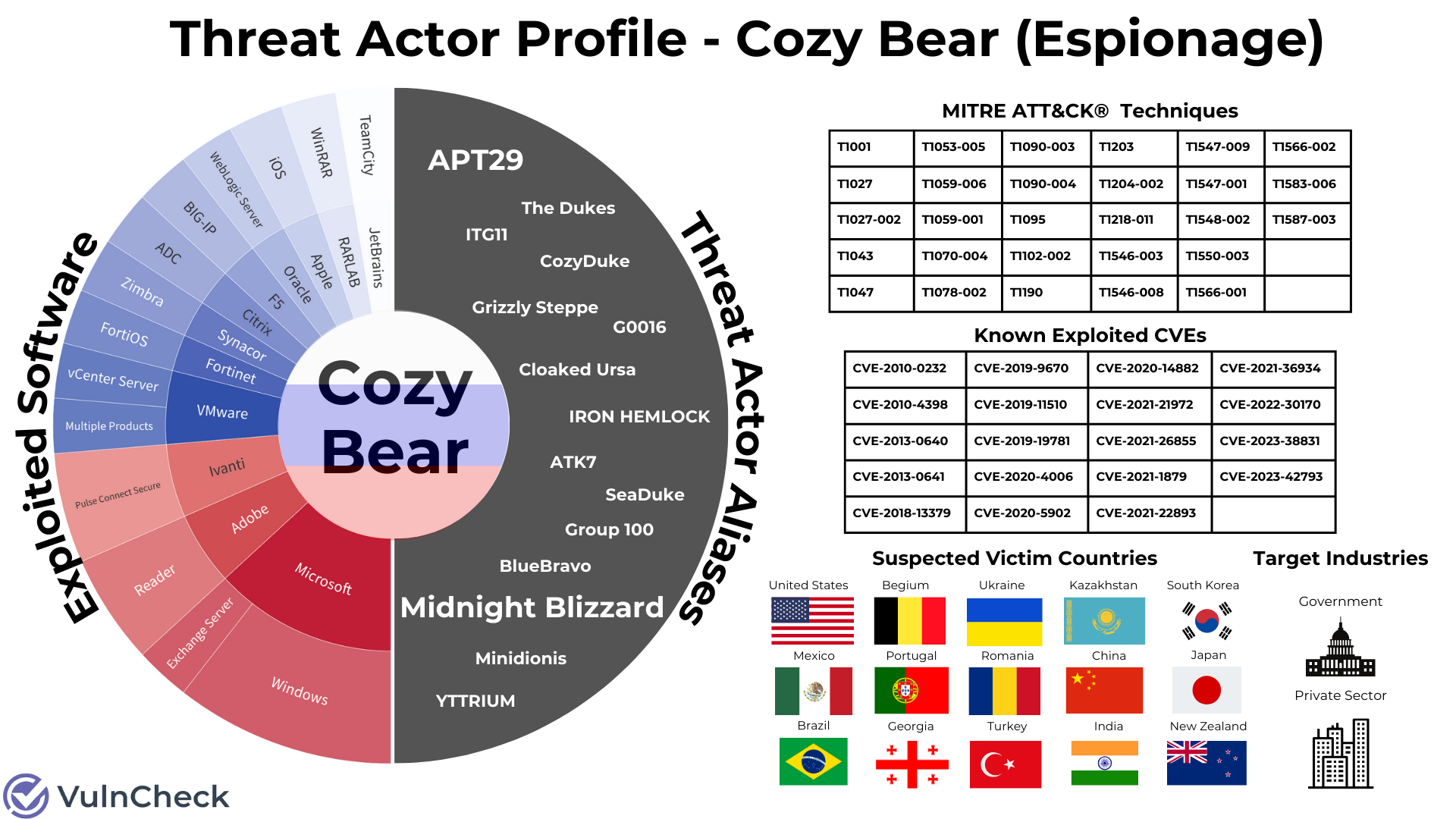
Taking a data-driven approach to visualizing the profile of threat actors can provide meaningful information without the time-consuming process of sifting through lengthy reports of information.
Let’s explore how we can accomplish this through the exercise in exploring a threat actor with a simple question… What do Cozy Bear, APT29, Midnight Blizzard, Zimbra, Exchange, TeamCity, CVE-2023-42793, CVE-2021-1879, China, United States, TI053-005 and TI548-002 all have in common?
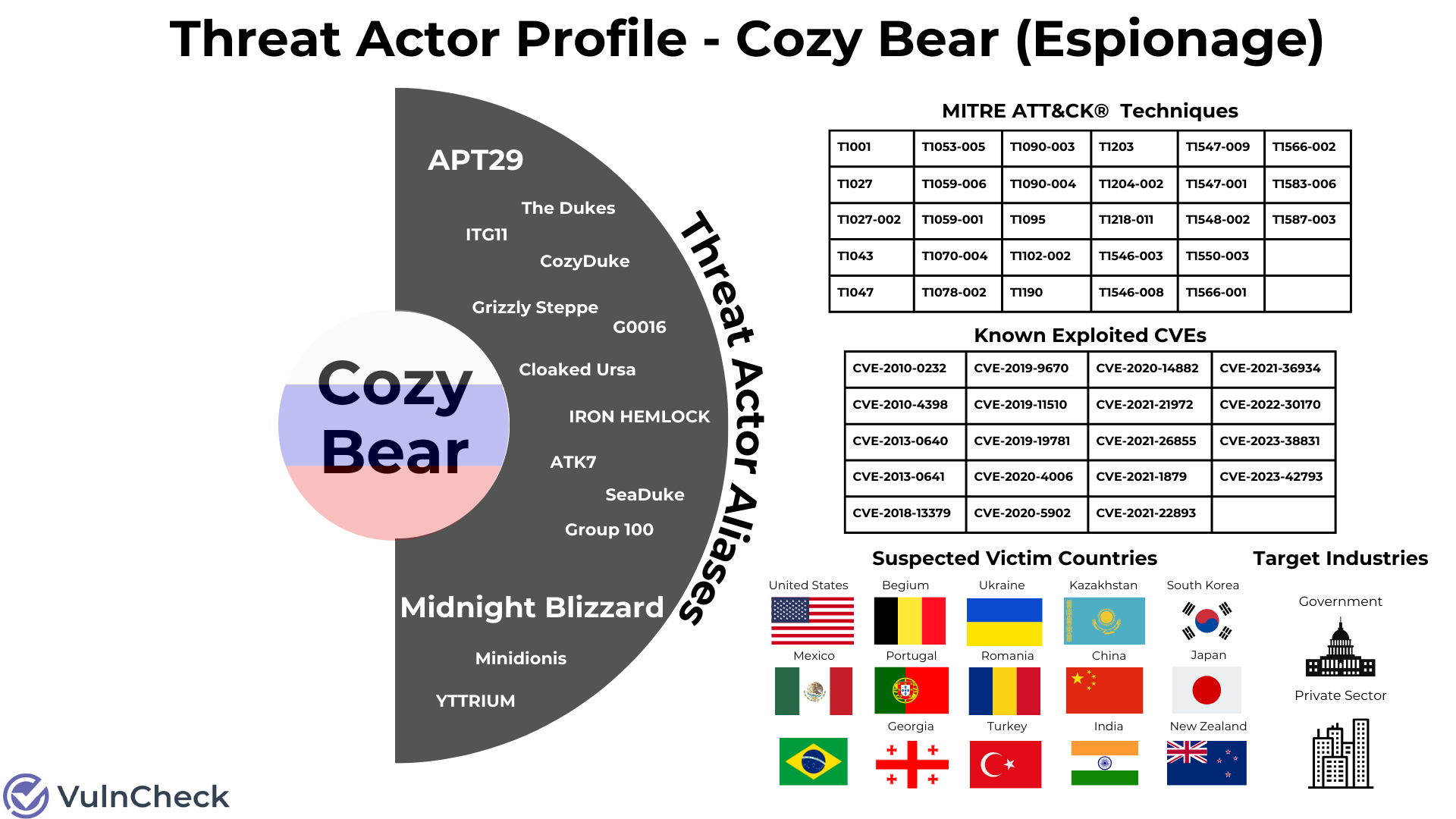
They are all associated with the same threat actor often referred to as Cozy Bear (Crowdstrike), APT29 (Mandiant), Midnight Blizzard (Microsoft), or one of the other 13 names the Russian nation-state threat actor has been given.
When it comes to the anatomies of threat actors, there are many different attributes, techniques and tactics to be explored. Using VulnCheck’s Threat Actor API Endpoint, I now have quick access to broad intelligence on threat actors. Pivoting to additional vulnerability/exploitation data that I can use to expand a threat actor’s profile in the future. But, before I jump into the weeds too deep, let’s start by exploring the basic anatomy of a single threat actor: Cozy Bear.
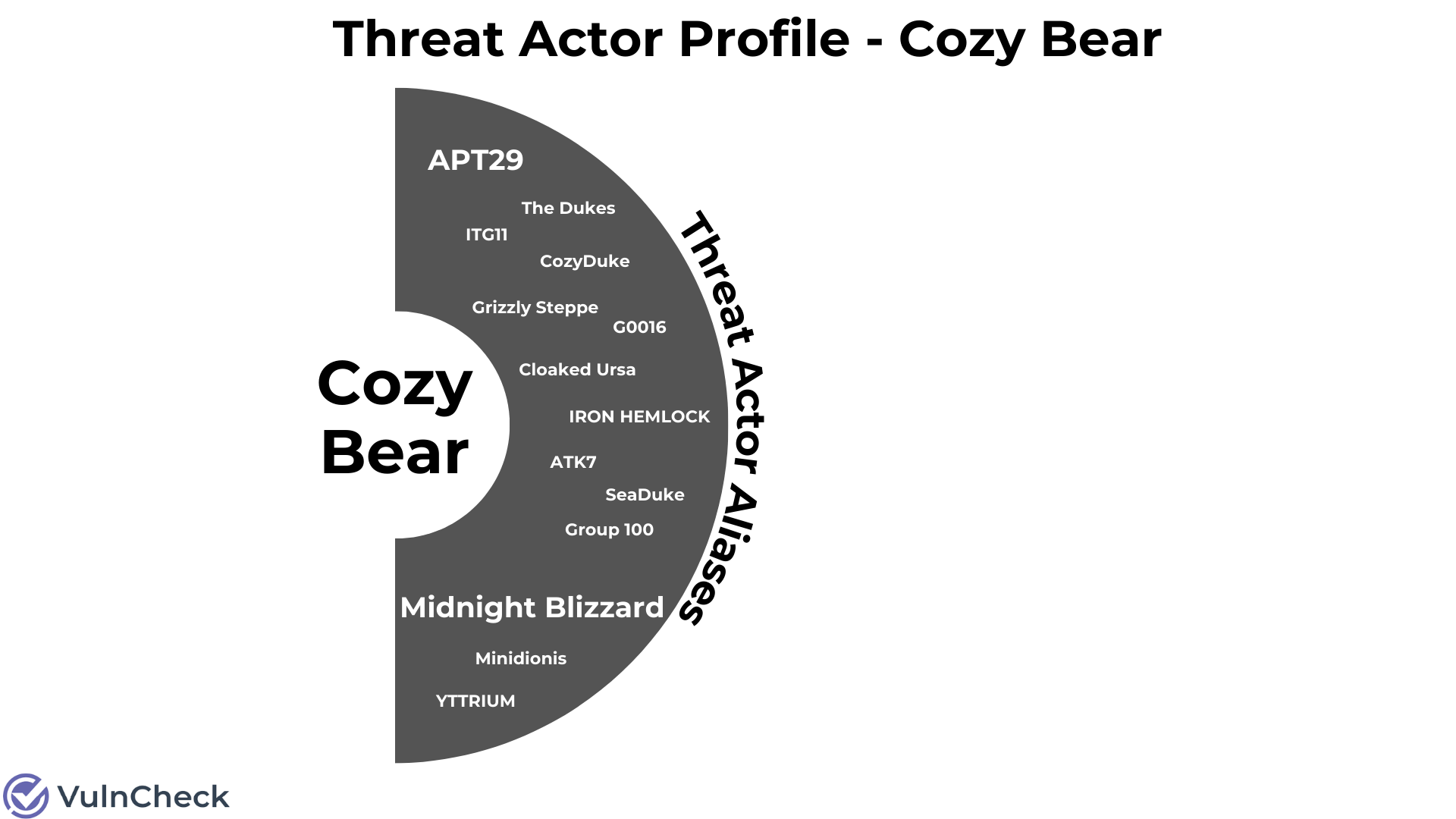
Threat Actor Identifiers / Aliases
We can start by exploring a threat actor using one of multiple names or IDs generated by Mitre, MISP, Malpedia, Crowdstrike and/or Microsoft. Here we can see that Cozy Bear is the name of the threat actor that is used by Crowdstrike that we default to using as the primary name. Microsoft refers to the same threat actor as “Midnight Blizzard,” and both Mandiant and Mitre refer to it as “APT 29.” In total there are 15 threat actor names associated with Cozy Bear… that we know of.
Example JSON Threat Actor Names:
"threat_actor_name": "Cozy Bear",
"date_added": "2016-08-04",
"mitre_id": "G0016",
"misp_id": "b2056ff0-00b9-482e-b11c-c771daa5f28a",
"malpedia_url": "https://malpedia.caad.fkie.fraunhofer.de/actor/apt29",
"vendor_names_for_threat_actors": [
{
"vendor_name": "CrowdStrike",
"threat_actor_name": "Cozy Bear"
},
{
"vendor_name": "Microsoft",
"threat_actor_name": "Midnight Blizzard",
"url": "https://learn.microsoft.com/en-us/microsoft-365/security/intelligence/microsoft-threat-actor-naming"
}
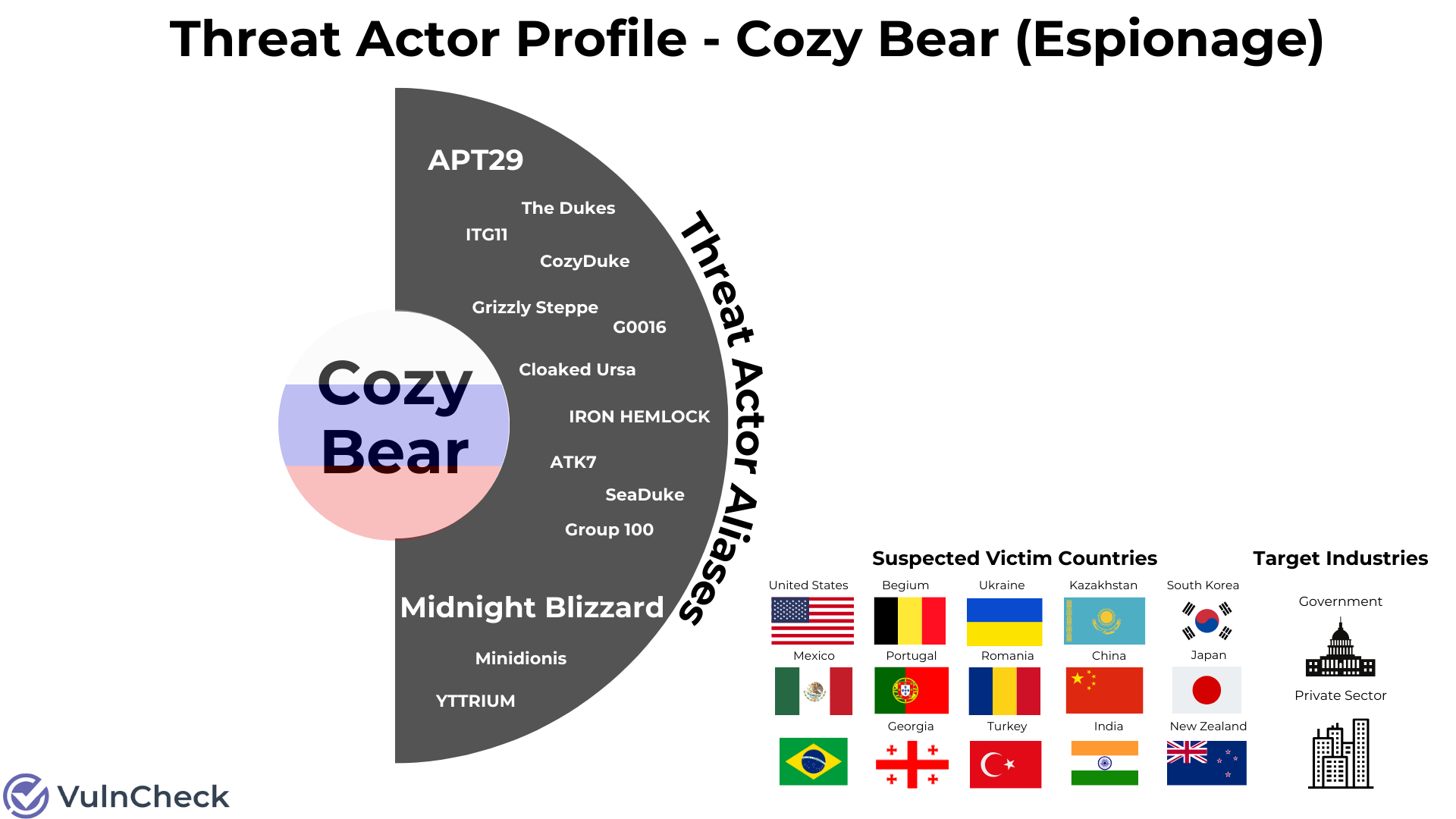
MISP Suspected Victims / Target Category / Incident Type / Threat Actor Operating Country / Synonyms
Now we need to bring some color to the threat actor’s profile. Using MISP data we learn that the threat actor is a Russian state sponsor, focused on cyber espionage, targeting government and private sector entities located in the United States, China, New Zealand, Ukraine, Romania, Georgia, Japan, South Korea, Belgium, Kazakhstan, Brazil, Mexico, Turkey, Portugal and India. Country flags bring color to the threat actor profile. This is the threat actor profile version of Bob Ross’ “Happy Trees!”.
Example JSON MISP Data:
"misp_threat_actor": {
"description": "A 2015 report by F-Secure describe APT29 as: 'The Dukes are a well-resourced, highly dedicated and organized cyberespionage group that we believe has been working for the Russian Federation since at least 2008 to collect intelligence in support of foreign and security policy decision-making. The Dukes show unusual confidence in their ability to continue successfully compromising their targets, as well as in their ability to operate with impunity. The Dukes primarily target Western governments and related organizations, such as government ministries and agencies, political think tanks, and governmental subcontractors. Their targets have also included the governments of members of the Commonwealth of Independent States;Asian, African, and Middle Eastern governments;organizations associated with Chechen extremism;and Russian speakers engaged in the illicit trade of controlled substances and drugs. The Dukes are known to employ a vast arsenal of malware toolsets, which we identify as MiniDuke, CosmicDuke, OnionDuke, CozyDuke, CloudDuke, SeaDuke, HammerDuke, PinchDuke, and GeminiDuke. In recent years, the Dukes have engaged in apparently biannual large - scale spear - phishing campaigns against hundreds or even thousands of recipients associated with governmental institutions and affiliated organizations. These campaigns utilize a smash - and - grab approach involving a fast but noisy breakin followed by the rapid collection and exfiltration of as much data as possible.If the compromised target is discovered to be of value, the Dukes will quickly switch the toolset used and move to using stealthier tactics focused on persistent compromise and long - term intelligence gathering. This threat actor targets government ministries and agencies in the West, Central Asia, East Africa, and the Middle East; Chechen extremist groups; Russian organized crime; and think tanks. It is suspected to be behind the 2015 compromise of unclassified networks at the White House, Department of State, Pentagon, and the Joint Chiefs of Staff. The threat actor includes all of the Dukes tool sets, including MiniDuke, CosmicDuke, OnionDuke, CozyDuke, SeaDuke, CloudDuke (aka MiniDionis), and HammerDuke (aka Hammertoss). '",
"meta": {
"attribution-confidence": "50",
"cfr-suspected-state-sponsor": "Russian Federation",
"cfr-suspected-victims": [
"United States",
"China",
"New Zealand",
"Ukraine",
"Romania",
"Georgia",
"Japan",
"South Korea",
"Belgium",
"Kazakhstan",
"Brazil",
"Mexico",
"Turkey",
"Portugal",
"India"
],
"cfr-target-category": [
"Government",
"Private sector"
],
"cfr-type-of-incident": [
"Espionage"
],
"country": "RU",
"refs": [
"https://labsblog.f-secure.com/2015/09/17/the-dukes-7-years-of-russian-cyber-espionage/",
"https://www2.fireeye.com/rs/848-DID-242/images/rpt-apt29-hammertoss.pdf",
"https://www.us-cert.gov/sites/default/files/publications/AR-17-20045_Enhanced_Analysis_of_GRIZZLY_STEPPE_Activity.pdf",
"https://www.fireeye.com/blog/threat-research/2017/03/dissecting_one_ofap.html",
"https://www.cfr.org/interactive/cyber-operations/dukes",
"https://pylos.co/2018/11/18/cozybear-in-from-the-cold/",
"https://cloudblogs.microsoft.com/microsoftsecure/2018/12/03/analysis-of-cyberattack-on-u-s-think-tanks-non-profits-public-sector-by-unidentified-attackers/",
"https://www.secureworks.com/research/threat-profiles/iron-hemlock",
"https://attack.mitre.org/groups/G0016",
"https://unit42.paloaltonetworks.com/atoms/cloaked-ursa/",
"https://go.recordedfuture.com/hubfs/reports/cta-2023-0127.pdf"
],
"synonyms": [
"Group 100",
"COZY BEAR",
"The Dukes",
"Minidionis",
"SeaDuke",
"YTTRIUM",
"IRON HEMLOCK",
"Grizzly Steppe",
"G0016",
"ATK7",
"Cloaked Ursa",
"TA421",
"Blue Kitsune",
"ITG11",
"BlueBravo"
]
CVEs Associated with Threat Actor (Evidence Backed)
We can expand our research to explore CVEs tied to the threat actor which is evidence backed by reputable sources. This should send some joy down the spine of any vulnerability management team as they verify any of these CVEs exist in their most recent scan data.
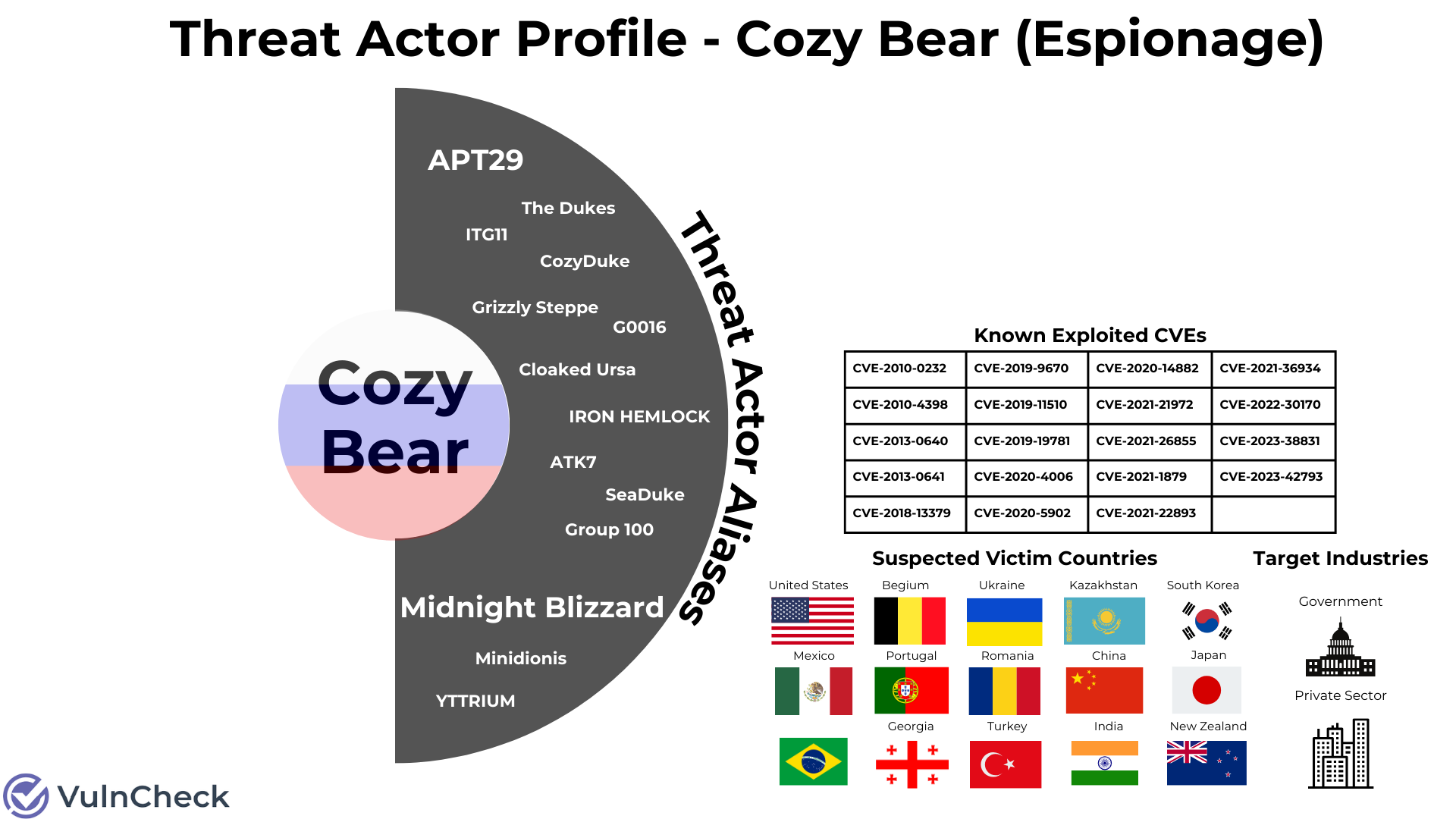
Example JSON CVE References:
"cve_references": [
{
"url": "https://www.recordedfuture.com/russian-apt-toolkits",
"date_added": "2016-08-04",
"cve": [
"cve-2010-0232",
"cve-2010-4398",
"cve-2013-0640",
"cve-2013-0641"
]
},
{
"url": "https://media.defense.gov/2020/jul/16/2002457639/-1/-1/0/ncsc_apt29_advisory-quad-official-20200709-1810.pdf",
"date_added": "2020-07-16",
"cve": [
"cve-2018-13379",
"cve-2019-9670",
"cve-2019-11510",
"cve-2019-19781"
]
MITRE Attack Techniques / Aliases
Now we can really spice things up for the SOC analyst team with the addition of MITRE Att&ck references used by the threat actor.
Example JSON Mitre Att&ck:
"mitre_attack_group": {
"name": "APT29",
"aliases": [
"APT29",
"YTTRIUM",
"The Dukes",
"Cozy Bear",
"CozyDuke"
],
"description": "APT29 is threat group that has been attributed to the Russian government and has operated since at least 2008. This group reportedly compromised the Democratic National Committee starting in the summer of 2015. ",
"techniques": [
{
"technique_id": "T1001",
"technique_name": "Data Obfuscation",
"sub_technique": "002",
"sub_technique_name": "Steganography",
"tactic": [
"command-and-control"
]
},
{
"technique_id": "T1027",
"technique_name": "Obfuscated Files or Information",
"tactic": [
"defense-evasion"
]
},
{
"technique_id": "T1027",
"technique_name": "Obfuscated Files or Information",
"sub_technique": "002",
"sub_technique_name": "Software Packing",
"tactic": [
"defense-evasion"
]
Expanding Vendors / Products
Lastly, we will pull the vendors and products associated with the CVEs we learned about to create a colorful data visualization that will catch the attention of any CISO / Board. And that completes the threat actor profile… for now!

A New View into Threat Actors
We’ve gracefully been able to shift the threat actor narrative here from a fear-driven approach associated with threat actors to one that orients around data rather than fictional characters. In the future, I would like to expand on this example profile with additional context pivoting across other data sources associated with vulnerabilities and suspected victims. We can learn about the threat actors from the treasure trove of data I’ve discovered since starting at VulnCheck. It also fits perfectly into a PowerPoint slide deck to share at your next leadership meeting.
About VulnCheck
Are you interested in exploring threat actors? Do you want to track the vulnerabilities they are exploiting in the wild? If so, VulnCheck's Exploit & Vulnerability Intelligence has broad threat actor coverage. Register and demo our data today.