Introduction
As part of our Exploit Intelligence service, VulnCheck tracks vulnerabilities exploited in the wild. Prioritizing known exploited vulnerabilities for remediation is a smart strategy to minimize vulnerability risk. However, that strategy breaks down when some exploited vulnerabilities are overlooked. Consider the growing gap between vulnerabilities VulnCheck tracks as exploited in the wild and the CISA KEV Catalog:
Exploited in the Wild Vulnerabilities Published in 2022
For CVE published in 2022, VulnCheck is tracking 37 more exploited vulnerabilities than the CISA KEV Catalog. One vulnerability that we’re tracking and KEV isn’t is CVE-2022-35914, a trivial unauthenticated and remote command execution vulnerability affecting GLPI. GLPI is open source software that can serve as a helpdesk, asset manager, administrator, and more. Their website displays logos of well-known customers such as Airbus, La Poste, and beIN Sports. The website further describes success cases where customers have deployed the software in business critical roles.
Exposing critical IT management software to the internet is a mistake the security industry sees often. Censys can find approximately 15,000 internet-facing GLPI instances.
Top 10 Countries with Internet-Facing Non-Virtualized GLPI Instances
Shodan doesn’t see half as many instances as Censys, but it is able to create an interesting historical graph of internet-facing GLPI services.
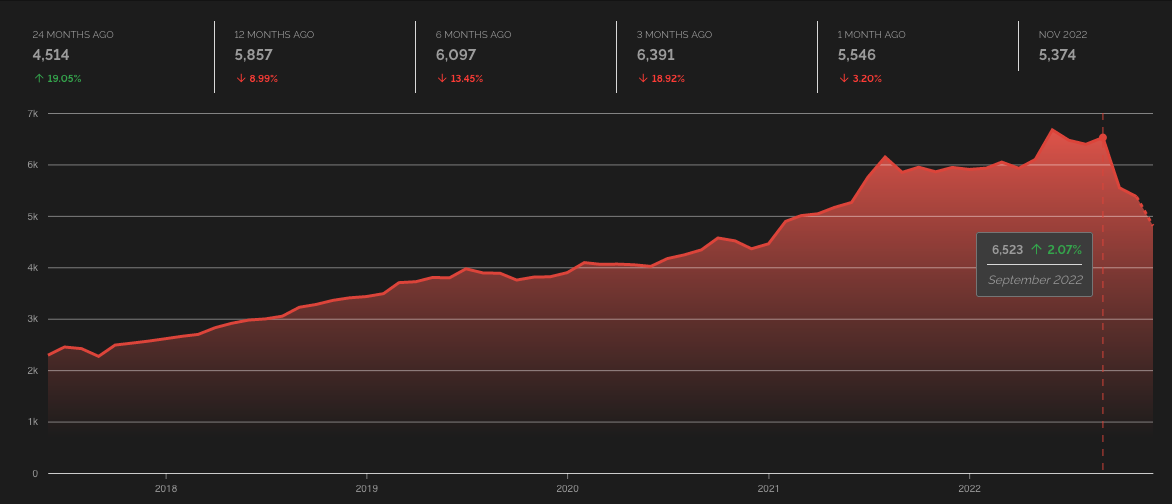
Since September 2022, Shodan has seen a steep drop off of GLPI. We believe the reason for this drop off can be explained using the exploitation timeline for CVE-2022-35914.
CVE-2022-35914 Vulnerability Timeline
Using VulnCheck’s Exploit Intelligence API, we’ve compiled the following timeline for CVE-2022-35914:
GLPI announces the release of version 10.3 and a fix for a “command injection” assigned CVE-2022-35914.
CVE-2022-35914 is published to NVD.
The first public proof of concept exploit is posted to GitHub.
A full disclosure blog is published.
A tweet containing a proof of concept exploit is posted.
GLPI publishes an important message, stating CVE-2022-35914 has been exploited “massively.”
Shadowserver tweets that they’re seeing exploitation attempts on their honeypots.
A pull request is created for a CVE-2022-35914 Metasploit module.
The Metasploit module is merged into the master branch and archived on packet storm.
A curl-based one-line proof of concept is posted to GitHub.
A “mass” scanner is advertised for sale on Twitter.
There is a lot going on here, but there are a few parts that are specifically worth calling out. First, there is a critical five day gap between GLPI announcing the security patch and the CVE being published to NVD. For better or worse, vulnerabilities often don’t “exist” in the security industry until they’ve been published by MITRE and NVD. That’s five days where this vulnerability was known to the world, but much of the security industry remained ignorant.
A proof of concept exploit was published to GitHub a little more than two weeks after the GLPI security patch was issued. That was rapidly followed by a full disclosure blog and, a few days later, GLPI announced “massive” exploitation in the wild. While not ideal, that's about as good a timeline defenders can reasonably expect for such a straightforward vulnerability. Ultimately, defenders had 18 days to patch before a full disclosure blog was released.
Researcher and attacker interest continued through October. Shadowserver tweeted about active exploitation in the middle of the month, and a Metasploit module was merged into the master branch in late October. In November a simple curl-based one-line proof of concept was published. This is worth noting because other proof of concepts were complicated by scraping a valid sid, when any old value would do.
albinolobster@mournland:~$ curl -s -d 'sid=foo&hhook=exec&text=id' -b 'sid=foo' http://10.12.70.206/glpi/vendor/htmlawed/htmlawed/htmLawedTest.php | egrep '\ \[[0-9]+\] =\>'| sed -E 's/\ \[[0-9]+\] =\> (.*)<br \/>/\1/'
uid=33(www-data) gid=33(www-data) groups=33(www-data)
Finally, as recently as December a “mass scanner” was advertised on Twitter. Although the asking price of $10 seems suspect. But regardless, the timeline and Shodan chart depicting a drop off after September 2022 compliment each other. GLPI instances appear to have been removed from the internet as exploitation ramped up. GLPI’s announcement and ShadowServer’s tweet about exploitation in the wild leave little doubt that CVE-2022-35914 has been exploited in the wild.
Active Exploitation
A couple of months have passed since GLPI and ShadowServer shared their observations regarding active exploitation of CVE-2022-35914. We think it’s useful to know if the vulnerability is still under active exploitation. There are two sources that can help us quickly answer that question. First, ShadowServer maintains a useful honeypot dashboard that lists all the vulnerabilities they’ve seen exploited recently. While not hugely exploited, we can see CVE-2022-35914 exploitation attempts remain ongoing.
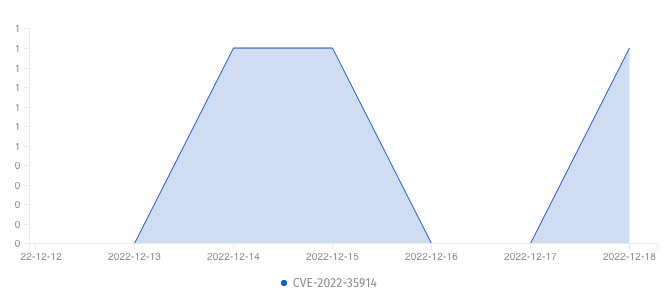
The other source we can turn to is GreyNoise. GreyNoise doesn’t have a tag for CVE-2022-35914, but we can query the API to get a list of malicious IP addresses attempting to reach the htmlLawedTest.php file containing the exploited debug functionality.
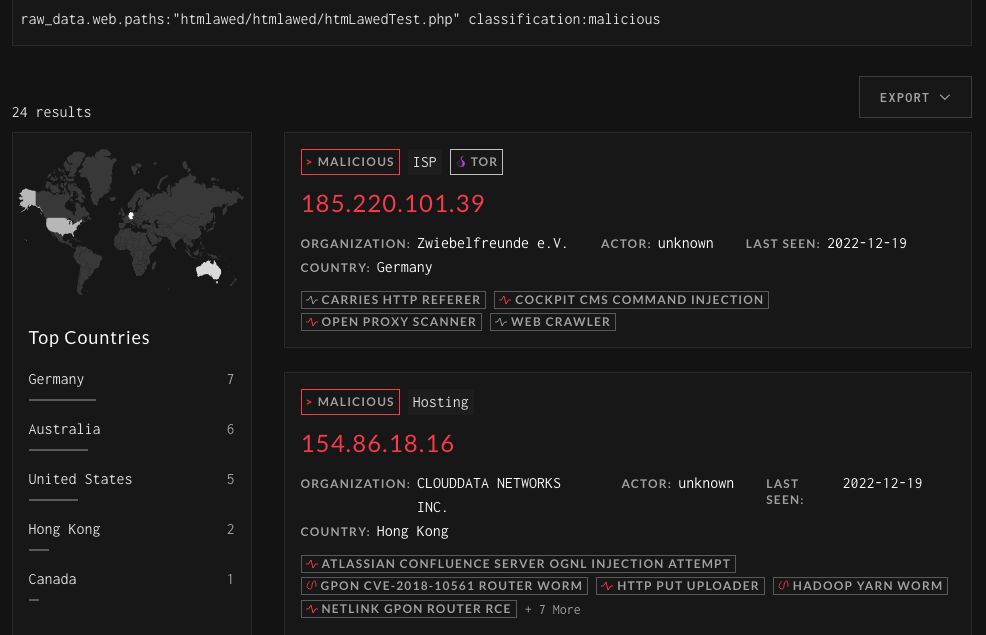
Both ShadowServer and GreyNoise indicate that exploitation attempts in the wild are ongoing. But are there still vulnerable hosts on the internet to exploit? To answer that question, we scanned the GLPI hosts that Shodan has indexed. The fix for CVE-2022-39514 was to remove htmlLawedTest.php from GLPI, as is was for test purposes only. Determining if a host is vulnerable is as simple as seeing if they still have htmLawedTest.php or not. We found only ~10% of internet-facing GLPI servers are currently vulnerable.
Internet-facing GLPI Servers Affected by CVE-2022-3914
Of course, the fact that there are hundreds of exploitable GLPI hosts is likely still interesting to attackers. The software is likely associated with a business and critical data. In fact, the software reminds us of Zoho ManageEngine Service Desk Plus that was extensively exploited by APT in 2021.
Conclusion
Prioritizing the remediation of vulnerabilities exploited in the wild is a solid vulnerability management strategy. But relying on a single source of information with an incomplete dataset could result in disaster. In this blog, we presented a vulnerability in crucial business software that has been exploited in the wild, but hasn’t been included in the CISA KEV Catalog. This is just one example of an overlooked vulnerability. There are many others, and we’ll visit more in the future.
For more information on vulnerabilities exploited in the wild, but not in CISA KEV, register for a VulnCheck account today by loading https://vulncheck.com and clicking “Log In”.