In Q1 2025, VulnCheck identified evidence of 159 CVEs publicly disclosed for the first time as exploited in the wild. The disclosure of known exploited vulnerabilities was from 50 different sources. We continue to see vulnerabilities being exploited at a fast pace with 28.3% of vulnerabilities being exploited within 1-day of their CVE disclosure. This trend continues from a similar pace we saw in 2024. This demonstrates the need for defenders to move fast on emerging threats while continuing to burn down their vulnerability debt.
Here are the key take-aways from our analysis and coverage of known exploited vulnerabilities:
- 159 KEVs were publicly disclosed in Q1-2025
- 28.3% of KEVs had exploitation evidence disclosed in < 1-day of a CVE being published
- 25.8% of KEVs are still awaiting or undergoing analysis by NIST NVD
- 3.1% of KEVs have been assigned the new "Deferred" status by NIST NVD
- 2 KEVs reported publicly have reserved but unpublished CVEs
- 1 KEV reported is now rejected
What Product Categories, Vendors and Products were Reported as Being Exploited?
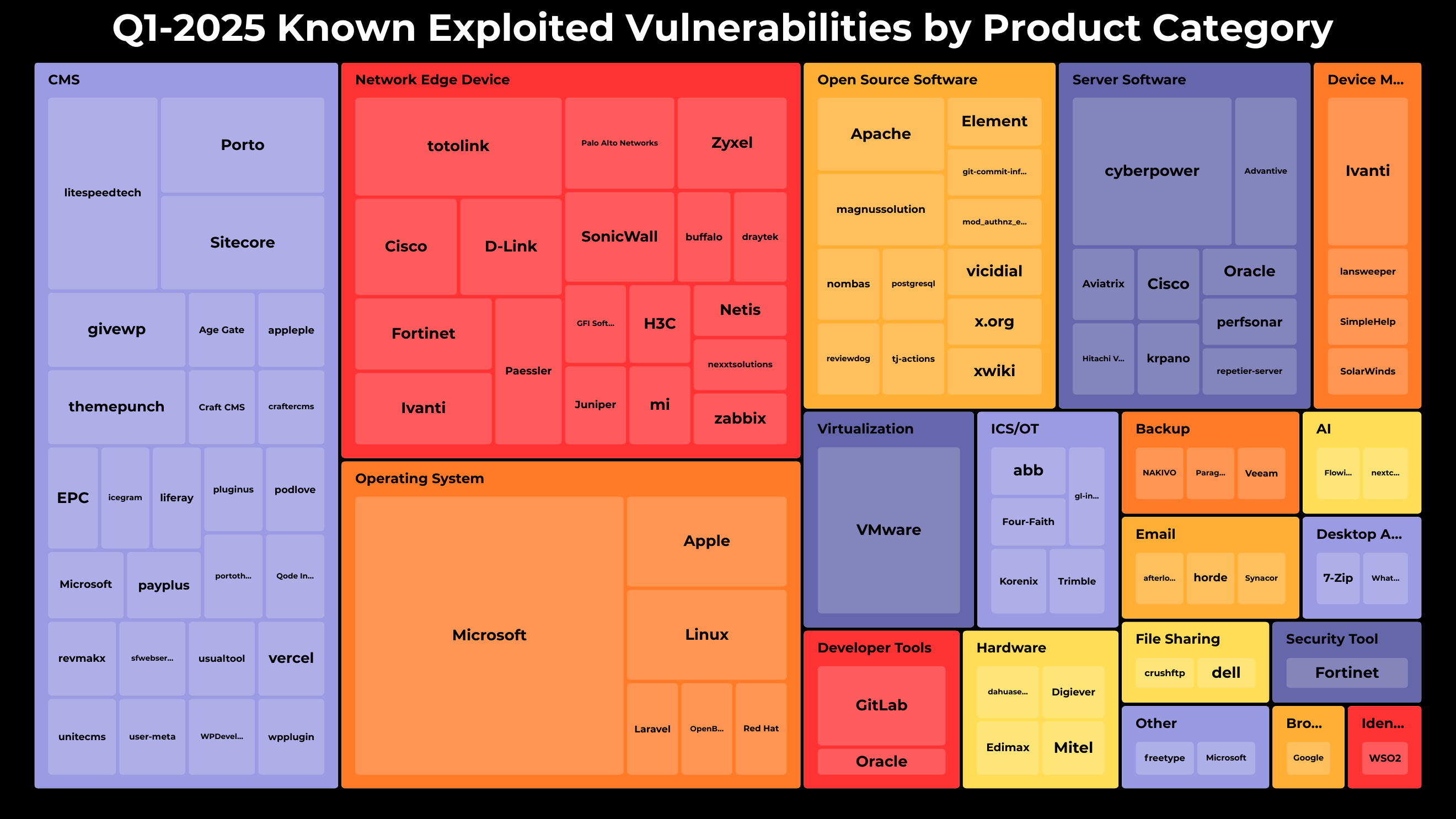
The top five categories associated with new KEVs in Q1 2025 were:
- Content Management Systems (CMS) (35)
- Network Edge Devices (29)
- Operating Systems (24)
- Open Source Software (14)
- Server Software (14)
These categories commonly include systems that are either internet-facing or accessible to end users. Notably, a relatively low number of KEVs were tied to desktop applications and browsers, which have historically been more frequently exploited. It will be interesting to see if this shift continues in the coming quarters.
Leading vendors and products impacted included:
- Microsoft Windows (15)
- Broadcom VMware (6)
- Cyber PowerPanel (5)
- Litespeed Technologies (4)
- Totolink Routers (4)
How Quickly Was Exploitation Evidence Reported?

When we look at the time from CVE disclosure to exploitation evidence, we can better understand how quickly vulnerabilities are being exploited. We observed 28.3% of KEVs had exploitation evidence disclosed in < 1-day of a CVE being published. 2 KEVs are still in reserved status and 1 was rejected. This appears to be marginally faster than what we saw in 2024 as threat actors continue to move fast on new vulnerabilities.
How Many Vulnerabilities were Reported as Exploited Each Week/Month for the First Time?

What began as a slow start to the year (likely seasonal) quickly shifted, with a surge toward the back half of the quarter in public exploitation disclosures leading to 159 Known Exploited Vulnerabilities (KEVs) reported in Q1 2025. On average, 11.4 KEVs were disclosed weekly, and 53 per month. While CISA KEV added 73 vulnerabilities during the quarter, only 12 showed no prior public evidence of exploitation.
For defenders, this trend provides valuable insight for capacity planning around emerging, vulnerability-related threats.
Who Was the First to Publicly Report Exploitation?
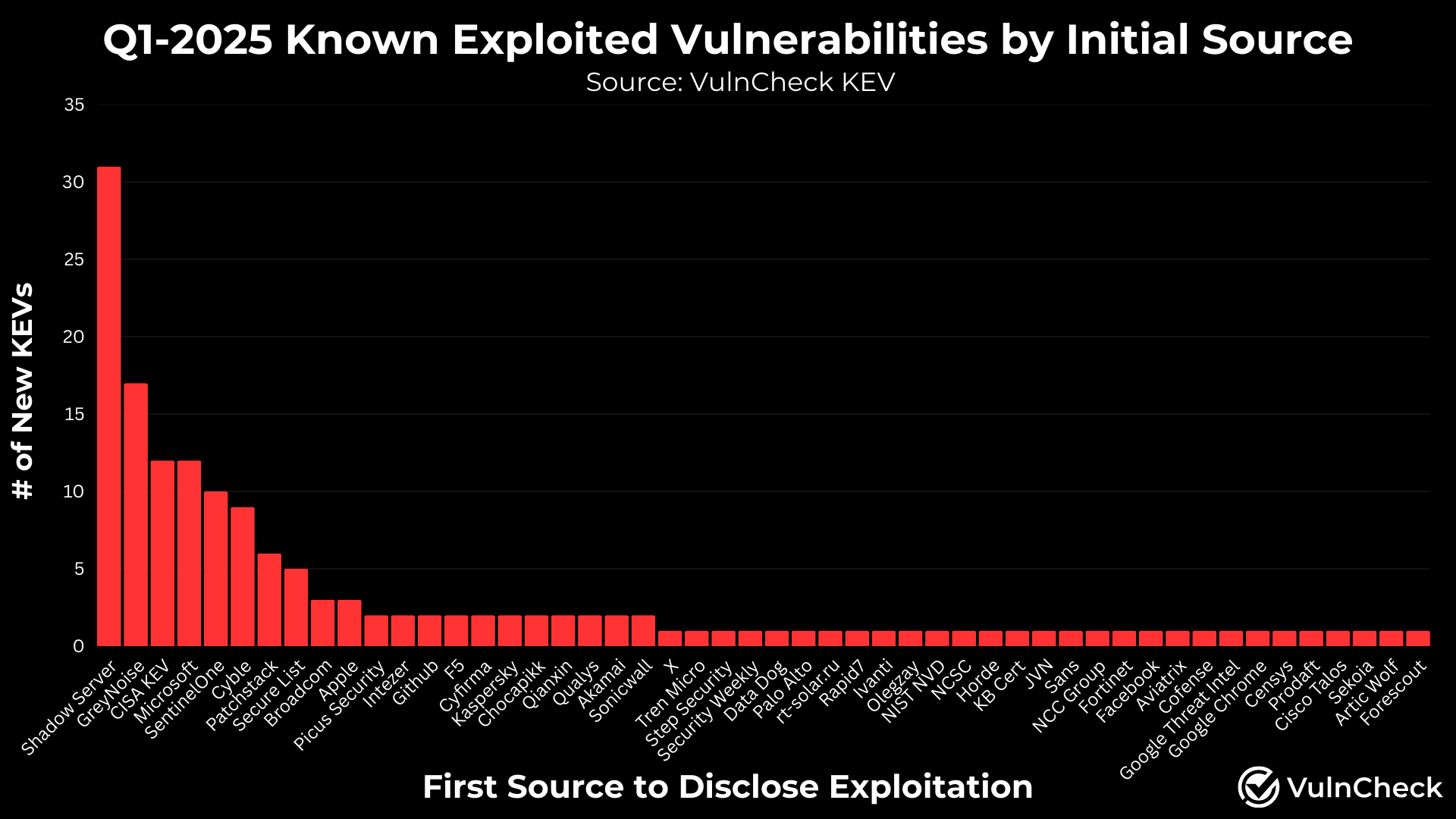
In Q1 2025, there were 159 vulnerabilities with publicly disclosed evidence of exploitation sourced from 50 different organizations. Notably, the data showed a long-tail distribution of these disclosures, a valuable trend for defenders seeking actionable threat intelligence. By comparison, Q4 2024 saw 190 exploitation disclosures tied to CVEs. However, 39 were older WordPress vulnerabilities with previously known exploitation activity. After coordinating with Wordfence to assign CVEs, these were officially published, inflating the Q4 total. Excluding them, the adjusted number would be 151. Top contributors to disclosing exploitation evidence publicly included:
- Shadow Server (31)
- GreyNoise (17)
- CISA KEV (12)
- Microsoft (12)
- Sentinel One (10)
- Cyble (9)
- Patchstack (6)
- Secure List (5)
What are the Current NVD/CVE Statuses of Q1-2025 KEVS?
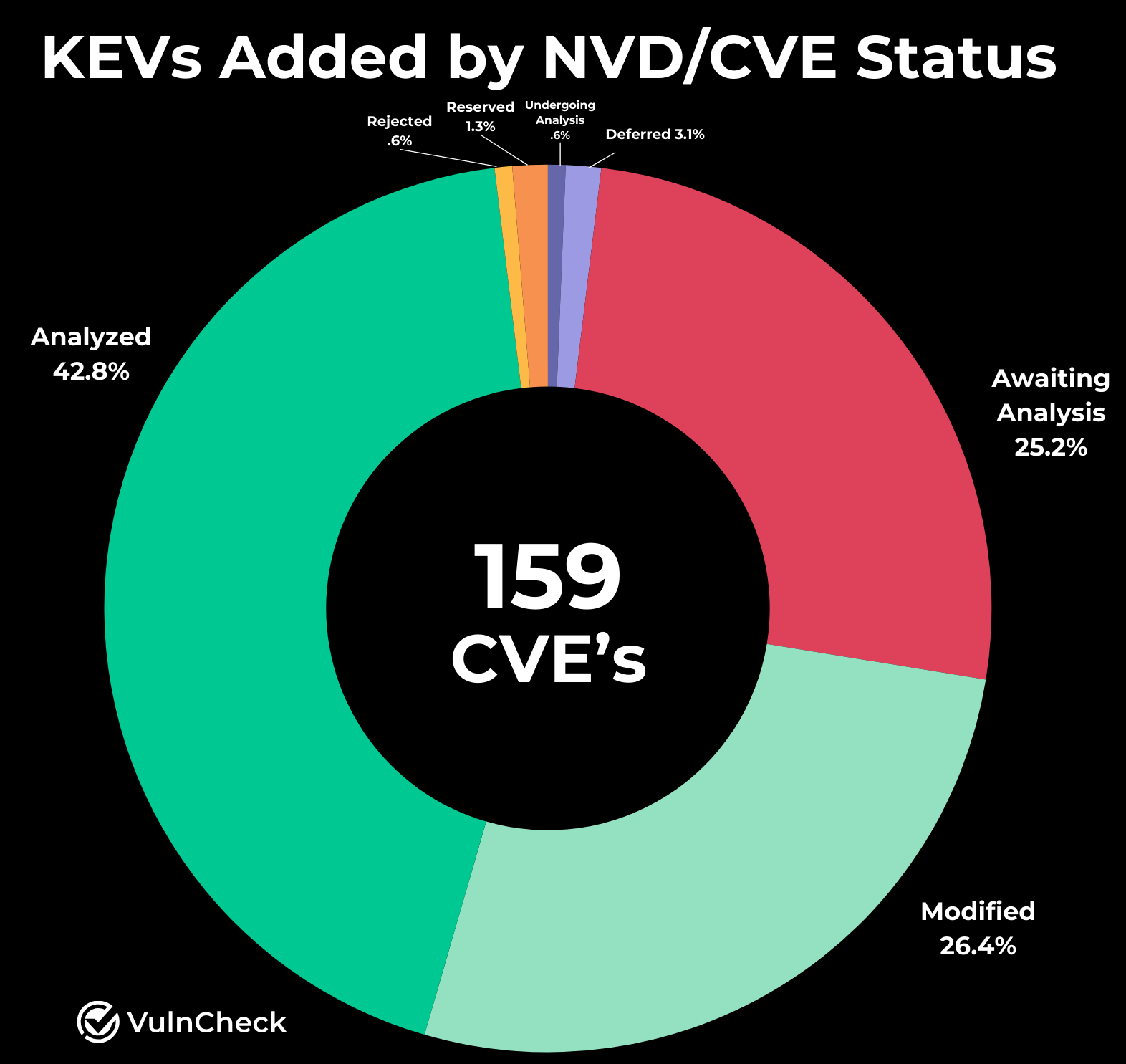
We wanted to explore the current NVD/CVE statuses of vulnerabilities’ with known exploitation to identify potential gaps in NIST’s NVD coverage. Our analysis found that 25.8% are still awaiting or undergoing analysis, 3.1% have been assigned the new "Deferred" status, and 69.2% are marked as "Analyzed" or "Modified."
A Look at Q1 2025 Known Exploited Vulnerabilities Mapped to Scoring System

When examining the emerging threat use case through the lens of CVSS and EPSS scoring, we used the EPSS scores on the day exploitation evidence became publicly available and any available CVSS score at the time of research. We found that only a handful of vulnerabilities had elevated EPSS scores on the same day as exploitation disclosure, despite being known to have been exploited. This suggests that EPSS is largely a trailing indicator rather than a predictive tool for emerging threats.
Organizations should exercise caution when relying on vulnerability scoring systems for emerging threats.
About VulnCheck
VulnCheck is helping organizations not just to solve the vulnerability prioritization challenge - we’re working to help equip any product manager, security team and threat hunting team to get faster and more accurate intelligence with infinite efficiency using VulnCheck solutions. We knew that defenders needed better data, faster across the board, in our industry. So that’s what we deliver to the market. We deliver key insights on vulnerability management, exploitation and major trends we can extrapolate from our dataset to continuously support practitioners.
Join the VulnCheck Community today and get access to our VulnCheck NVD++ and the VulnCheck KEV in 30 seconds or less.