Key Takeaways
- In November, Mitre released the 2024 CWE Top 25 Most Dangerous Software Weaknesses list.
- Today, VulnCheck issued a report re-evaluating the rankings with a threat-centric approach.
- For each CWE, VulnCheck calculated the total number of CVEs, the count of known exploited vulnerabilities (KEVs), and the KEV-to-CVE ratio for the same period covered in Mitre's research.
- Findings suggest that while all vulnerabilities can pose risks, Mitre’s list heavily prioritizes vulnerability counts without considering real-world exploitation context.
- VulnCheck research repeatedly shows that vulnerabilities known to be exploited in the wild should be treated with urgency and remediated as soon as possible.
- The report questions whether CWEs like CWE-352 - Cross-Site Request Forgery and CWE-476 - Null Pointer Dereference even deserve a spot on the list.
- VulnCheck also highlights a handful of CWEs that are worth mentioning but not on Mitre’s top 25 list, including CWE-284: Improper Access Control, CWE-843:Type Confusion, and more
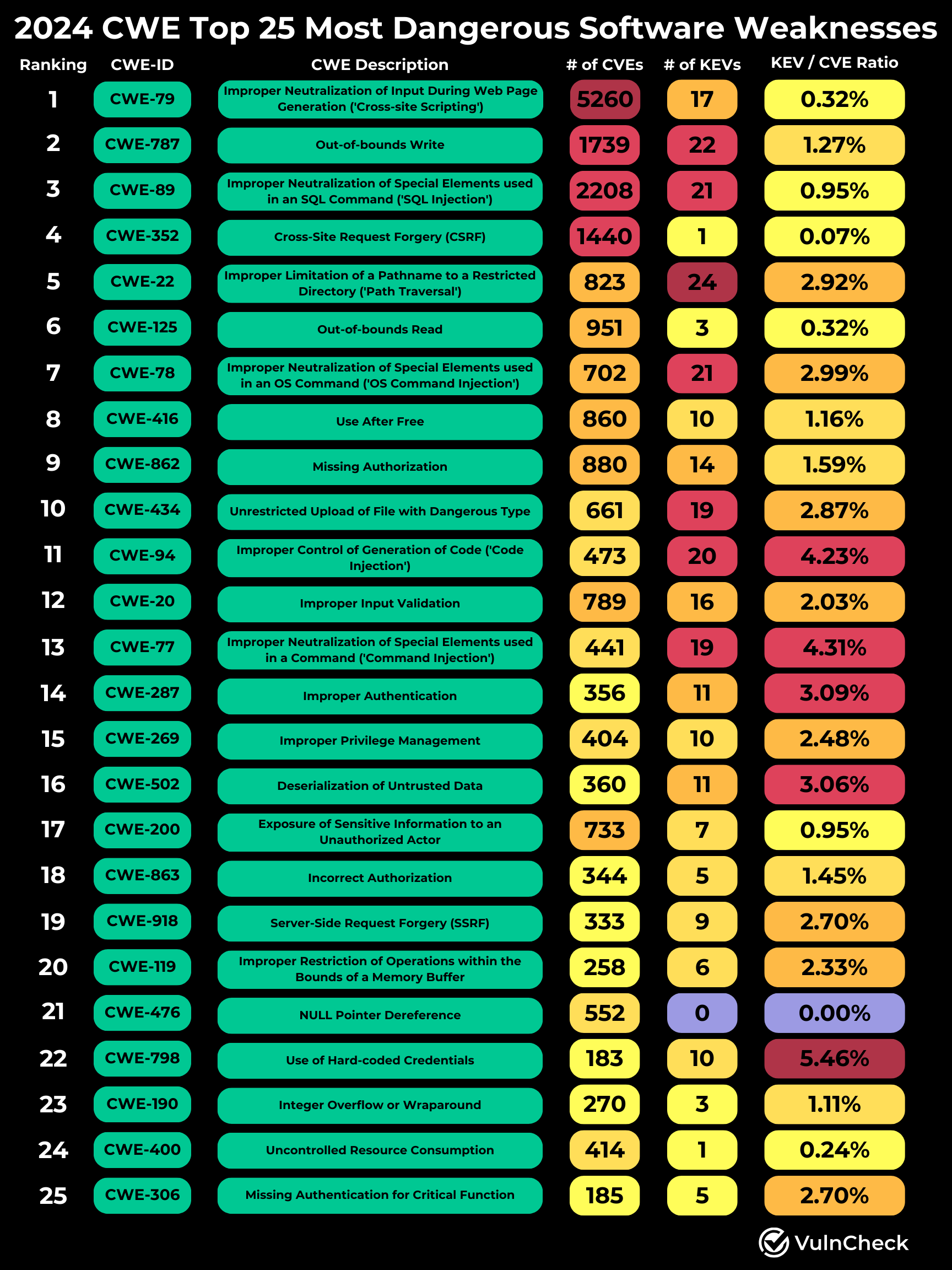
In November, Mitre released its annual research on the Top 25 most dangerous software weaknesses. This research calculates a "danger score" based on a combination of frequency and severity. We thought it would be interesting to re-evaluate the rankings with a threat-centric approach using broader exploitation evidence to see if we could help answer the question, “Are the Top 25 CWEs Truly the Most Dangerous Software Weaknesses in 2024?."
To do this, we analyzed CVEs from the same time period and mapped known exploitations to the CVEs associated with each CWE using VulnCheck KEV, which is a free community resource. For each CWE, we calculated the total number of CVEs, the count of known exploited vulnerabilities (KEVs), and the KEV-to-CVE ratio for the same period covered in Mitre's research (June 1, 2023 – June 1, 2024).
Using these metrics, we created a chart to visualize the 2024 Top 25 Most Dangerous CWEs. To enhance clarity, we applied color gradients to represent the density of each metric, offering a more intuitive view into how these factors might impact the rankings.
Exploring The CWE Top 25 Most Dangerous Software Weaknesses
Mapping to CVE Counts
We first examined the CVE counts, which appear to closely align with the CWE rankings. This correlation is unsurprising since the count or frequency of CVEs is a core component of the Danger Score calculation. Incorporating severity, as measured by CVSS, has only a marginal impact on the rankings.
Mapping to Known Exploitation Vulnerabilities
Next, we explored how known exploitation might influence the Top 25 CWE rankings. Using VulnCheck KEV, we calculated the number of vulnerabilities that have evidence of exploitation to understand how CWEs would rank based solely on the volume of Known Exploited Vulnerabilities (KEVs) published during the same time period using VulnCheck KEV.
KEV to CVE Ratio
We then calculated the KEV to CVE ratio for each CWE to assess its potential impact on rankings. This calculation provided insights into how weighting CWEs with a threat component could significantly reorder the Top 25 CWEs. We considered using a weighted calculation but decided to keep it simple with the KEV to CVE ratio for this analysis.
A look into the Top 25 CWE Outliers
To better analyze the outliers among the Top 25 CWEs, we used a bubble chart for CWE’s with 100 or more CVEs and 1 or more KEVs associated with them. This visualization maps the volume of vulnerabilities on the x-axis, the KEV-to-CVE ratio on the y-axis, and represents the number of KEVs with bubble sizes.
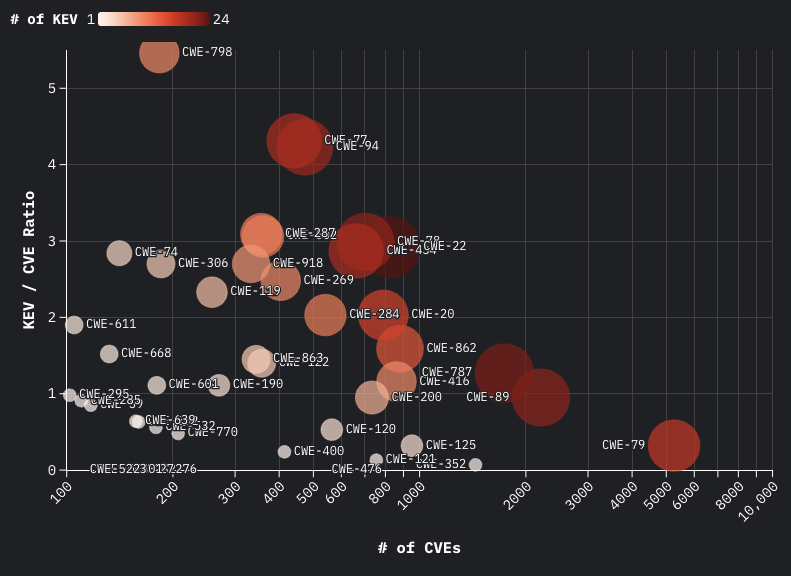
CWE Outlier observations
CWEs w/ Higher KEV-to-CVE Ratio and Lower CVE count
CWE-798 - Hard Coded Credentials Six KEVs associated with Hitron DVR systems were published with the same description for different products. If these were treated as a single CVE, the KEV-to-CVE ratio would drop to 2.73%.
CWE-77 - Improper Neutralization of Special Elements used in a Command ('Command Injection') This CWE shows a high prevalence of KEVs tied to a wide range of noteworthy products, including network devices and ICS equipment. Examples include Ivanti Sentry, Ivanti Connect Secure, VMware Aria, Totolink, Tenda, Palo Alto PanOS, Nextgen MirthConnect, Honeywell firmware, and D-Link, among others.
CWE-94 - Improper Control of Generation of Code ('Code Injection') There is a notable prevalence of KEVs linked to widely used technology and open-source projects. Examples include Apache OFBiz/RocketMQ, OpenMetadata, CrushFTP, Cisco ASA, Microsoft Windows, Citrix Netscaler, Ivanti Sentry, and others.
CWEs w/ Lower KEV-to-CVE Ratio and Higher CVE count
CWE-79 - Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting') Nearly half of the KEVs identified are associated with WordPress plugins. Other notable technologies with known exploitation outside the WordPress ecosystem include Citrix Netscaler, Roundcube (email), and Zimbra (email). We noticed that 37% of all CVEs associated with CWE-79 come from WordPress CNAs, making the WordPress plugin ecosystem a major factor in elevating CWE-79 to the top of the CWE’s most dangerous list.
CWE-89 - Improper Neutralization of Special Elements used in an SQL Command ('SQL Injection') Several prevalent technologies, such as Progress MOVEit, SonicWall Analytics, PostgreSQL, Ivanti EMM, Fortinet FortiClient, and F5 Big-IP, have KEVs tied to this CWE, suggesting it’s deserving of a top spot on the list.
CWE-787 - Out-of-bounds Write Based on the technologies impacted and the volume of KEVs, this CWE stands out as one of the more dangerous weaknesses, suggesting it deserves its high ranking. Affected technologies include Google Chrome/Edge, VMware vCenter, VMware ESXi, Microsoft Windows, GNU glibc, Fortinet FortiOS, Rockwell Automation devices, Ivanti Connect Secure, Cisco IOS/XE, Adobe Acrobat, and others.
CWE-352 - Cross-Site Request Forgery (CSRF) Despite ranking 4th on the list, only a single KEV was identified for this CWE, which is tied to a WordPress plugin. This raises questions about whether CSRF deserves to be in the top 25, let alone being placed so high on the list.
CWEs with no Exploitation Evidence During this Time Period
CWE-476 - Null Pointer Dereference We didn’t see any evidence during this time period of CVEs with this CWE being exploited. The most recent known exploited vulnerability we could find with CWE-476 was published in 2019 and is CVE-2019-10097.
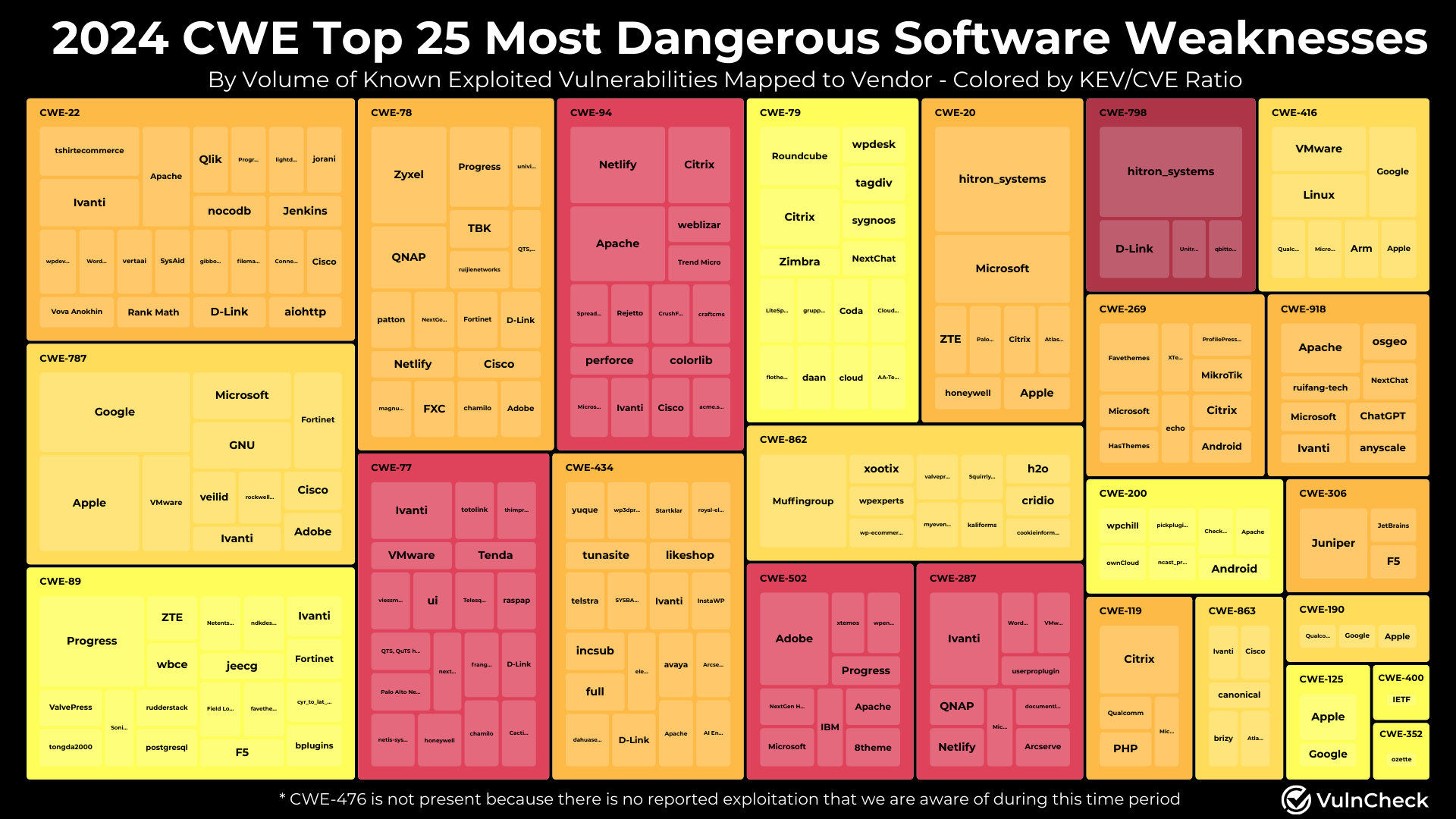
Exploring CWEs by Vendors with Known Exploited Vulnerabilities
We assembled this treemap of CWEs from the top 25 list that includes vendors. Looking at Vendors can help us better understand what vulnerabilities being exploited might be in more broadly adopted technology. We also colorized the treemap based on the KEV to CVE ratio from the research above.
Other Noteworthy CWEs Not on the CWE Top 25 List
There are a handful of CWEs that are worth mentioning that did not make the top 25 most dangerous list…
| CWE | Description | CVEs | KEVs | Notable Vendor(s) / Product(s) |
|---|---|---|---|---|
| CWE-284 | Improper Access Control | 541 | 11 | Adobe Cold Fusion, Linksys RE7000/E2000, Microsoft Windows, Citrix Content Collaboration, Apache HugeGraph |
| CWE-843 | Access of Resource Using Incompatible Type ('Type Confusion') | 96 | 6 | Google Chrome / Apple OS/IOS |
| CWE-288 | Authentication Bypass Using an Alternate Path or Channel | 33 | 5 | Jetbrains Teamcity, F5 BigIP, ConnectWise Screenconnect, Cisco ASA |
| CWE-122 | Heap-based Buffer Overflow | 357 | 5 | Microsoft Windows, Gnu glibc, Fortinet FortiOS |
| CWE-74 | Buffer Copy without Checking Size of Input ('Classic Buffer Overflow') | 141 | 4 | Terra Master OS, IBM Operational Decision Manager, Atlassian Confluence |
Are the Top 25 CWEs Truly the Most Dangerous Software Weaknesses in 2024?
Our research shows that while all vulnerabilities can be dangerous, the 2024 CWE Top 25 Most Dangerous CWEs heavily prioritize vulnerability counts without considering real-world exploitation context. To address this, we developed an alternative CWE ranking based on the number of Known Exploited Vulnerabilities from the same period, offering a practical perspective on the most commonly exploited weaknesses.
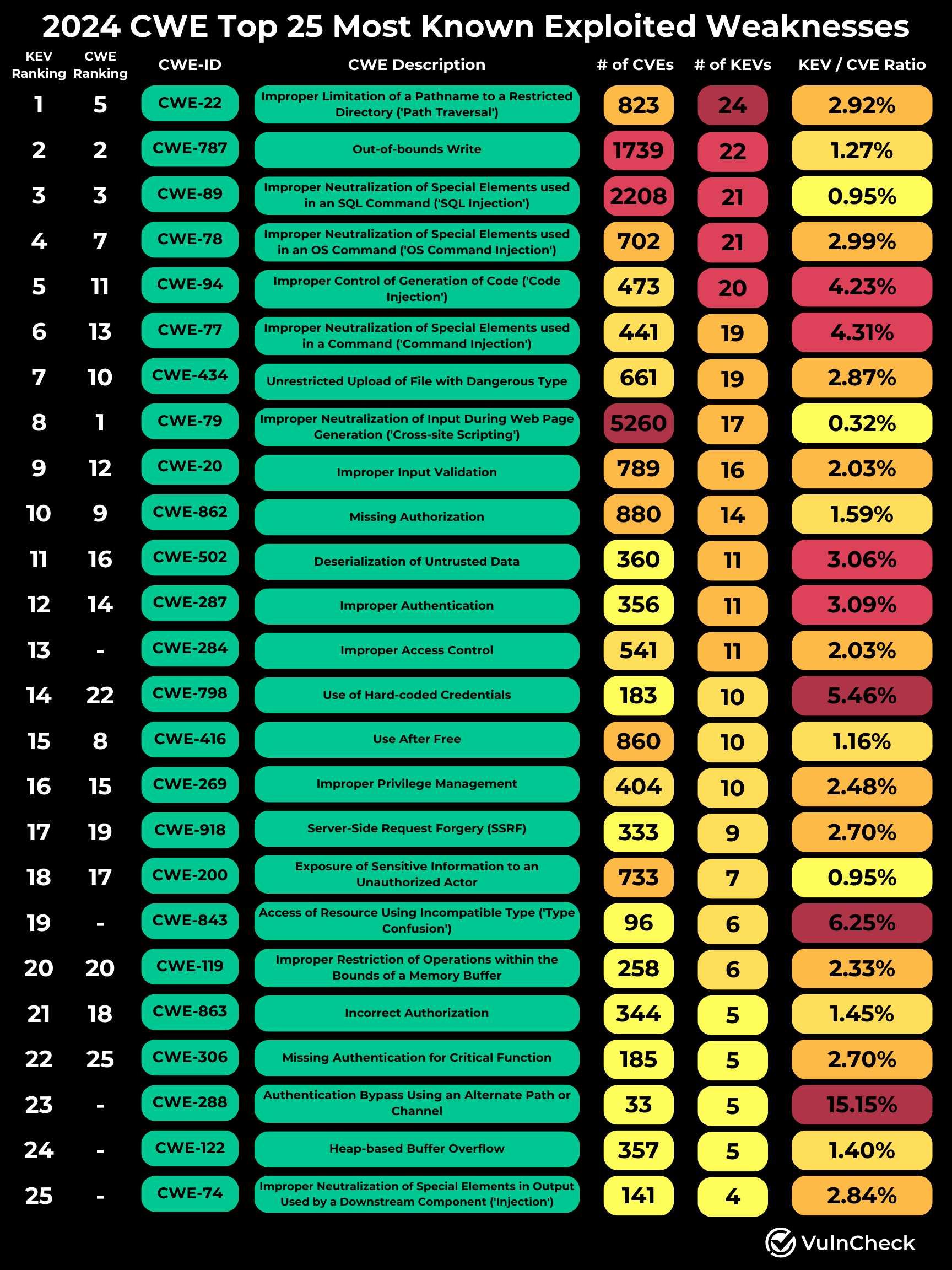
Considerations
We decided to rank CWEs based on number of exploited vulnerabilities per CWE rather than the KEV-to-CVE ratio. This is largely due to the high number of CWEs with low single digit KEVs(1-3) and a small number of CVEs (<100). If we were to rank based on a scoring system in the future, we would definitely want to consider use weighting in the calculation. We encourage others to research as well.
About VulnCheck
VulnCheck is helping organizations not just to solve the vulnerability prioritization challenge - we’re working to help equip any product manager, CSIRT/PSIRT or SecOps team and Threat Hunting team to get faster and more accurate with infinite efficiency using VulnCheck solutions.
We knew that we needed better data, faster across the board, in our industry. So that’s what we deliver to the market. We’re going to continue to deliver key insights on vulnerability management, exploitation and major trends we can extrapolate from our dataset to continuously support practitioners.
Are you interested in learning more? If so, VulnCheck's Exploit & Vulnerability Intelligence has broad threat actor coverage. Register and demo our data today.