Key Takeaways
- VulnCheck now provides an automated approach to providing broader visibility into differences between VulnCheck KEV and CISA KEV through a Jupyter Notebook publicly available on GitHub.
- During 2024 (year-to-date), VulnCheck KEV added 717 new known exploited vulnerabilities (average of 59.8/month) vs. 170 added to CISA KEV (average of 14.2/month).
- During 2024 (year-to-date), VulnCheck KEV added 410 unique vendors with one or more KEV vs. 56 unique vendors in CISA KEV.
- The top 10 vendors by number of exploited vulnerabilities in 2024 include Microsoft (55), Apache (18), Ivanti (17), Apple (16), D-Link (14), Oracle (14), Google (13), Cisco (11), Progress (11) and VMware (11).
- The top 10 products with exploited vulnerabilities in 2024 include Microsoft Windows (30), Google Chrome / Chromium (11), Apple IOS products (9), Apache OFBiz (6), Ivanti Connect Secure (6), Citrix Netscaler (6), Apple Safari (5), Cisco ASA / FTD (5), QNAP QTS (5), and openSSL (5).
Video Walkthrough: Vulncheck KEV Jupyter Notebook
Last month, we forewent our monthly update on known exploited vulnerabilities (KEVs) and put that work towards building an automated approach to reviewing KEV trends that is easy for anyone to copy, modify and use. Our goal is to provide broader visibility into differences between VulnCheck KEV and CISA KEV using a public Jupyter Notebook that is automatically updated on a daily basis.
The Jupyter Notebook is available on VulnCheck’s Github Github to use and works with our free community edition if you want to build your own Vulncheck KEV dashboard.
2024 Known Exploited Vulnerabilities Statistics (CISA KEV vs. Vulncheck KEV)

The first area we explored was the volume differences between VulnCheck KEV and CISA KEV. To visualize this, we created a top-level dashboard highlighting key statistics for 2024, including: The total number of KEVs added. VunCheck KEV added 717 new known exploited vulnerabilities, while CISA KEV added 170.
The average number of KEVs added per month. Vulncheck averaged 59.8 KEVs per month, while CISA averaged 14.2 per month. The number of unique vendors with at least one KEV. There are 410 unique vendors that had 1 or more KEV added to VulnCheck, while CISA covered 56 vendors. The number of unique products represented. VulnCheck added KEVs with 1 or more KEV while CISA added 98.
This dashboard provides a clear comparison of vendor and product coverage between VulnCheck KEV and CISA KEV.
Exploring CISA KEV & VulnCheck KEV by Vendor & Product
Given the significant disparity in the number of vendors and products between CISA KEV and VulnCheck KEV, we created an interactive explorer to help visualize and explore the data. To achieve this, we used an interactive treemap within a Jupyter notebook. To interact with these treemaps, simply download the Jupyter notebook and open it in a tool like VS Code.
Exploring VulnCheck KEV Vendors / Products
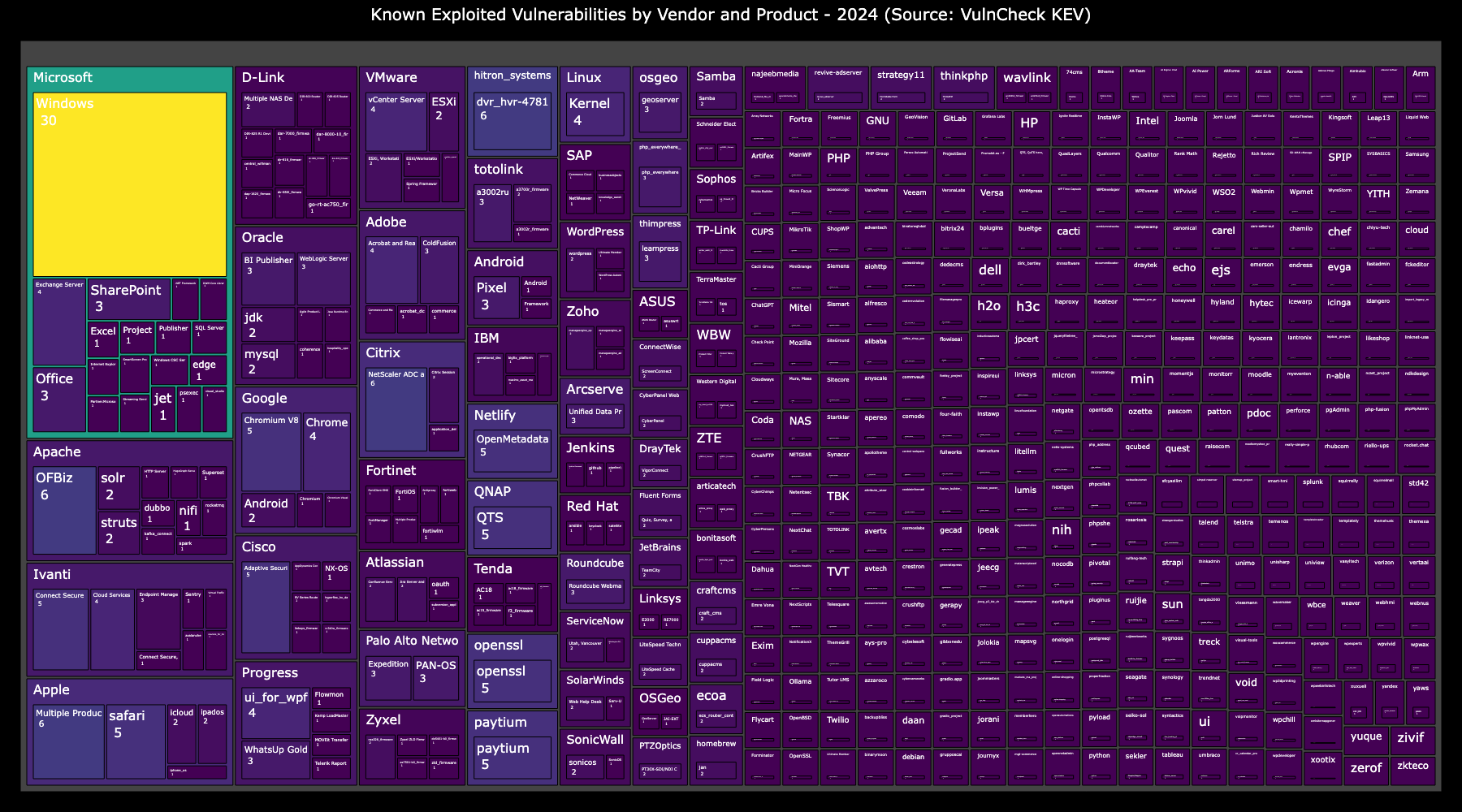
Based on exploit intelligence first captured by VulnCheck in 2024, the top 10 vendors by number of exploited vulnerabilities include Microsoft (55), Apache (18), Ivanti (17), Apple (16), D-Link (14), Oracle (14), Google (13), Cisco (11), Progress (11) and VMware (11).
Based on exploit intelligence first captured by VulnCheck in 2024, the top 10 products by exploited vulnerabilities include Microsoft Windows (30), Google Chrome / Chromium (11), Apple IOS products (9), Apache OFBiz (6), Ivanti Connect Secure (6), Citrix Netscaler (6), Apple Safari (5), Cisco ASA / FTD (5), QNAP QTS (5), and openSSL (5).
This data highlights the persistent targeting by threat actors across various platforms, including operating systems, browsers, web services, and network edge devices. Notably, products such as Hiltron DVR, Netlify OpenMetadata, and Paytium were omitted from this list due to the issuance of multiple CVEs for similar vulnerabilities simultaneously or their relatively lower prevalence.
Exploring CISA KEV by Vendors / Products
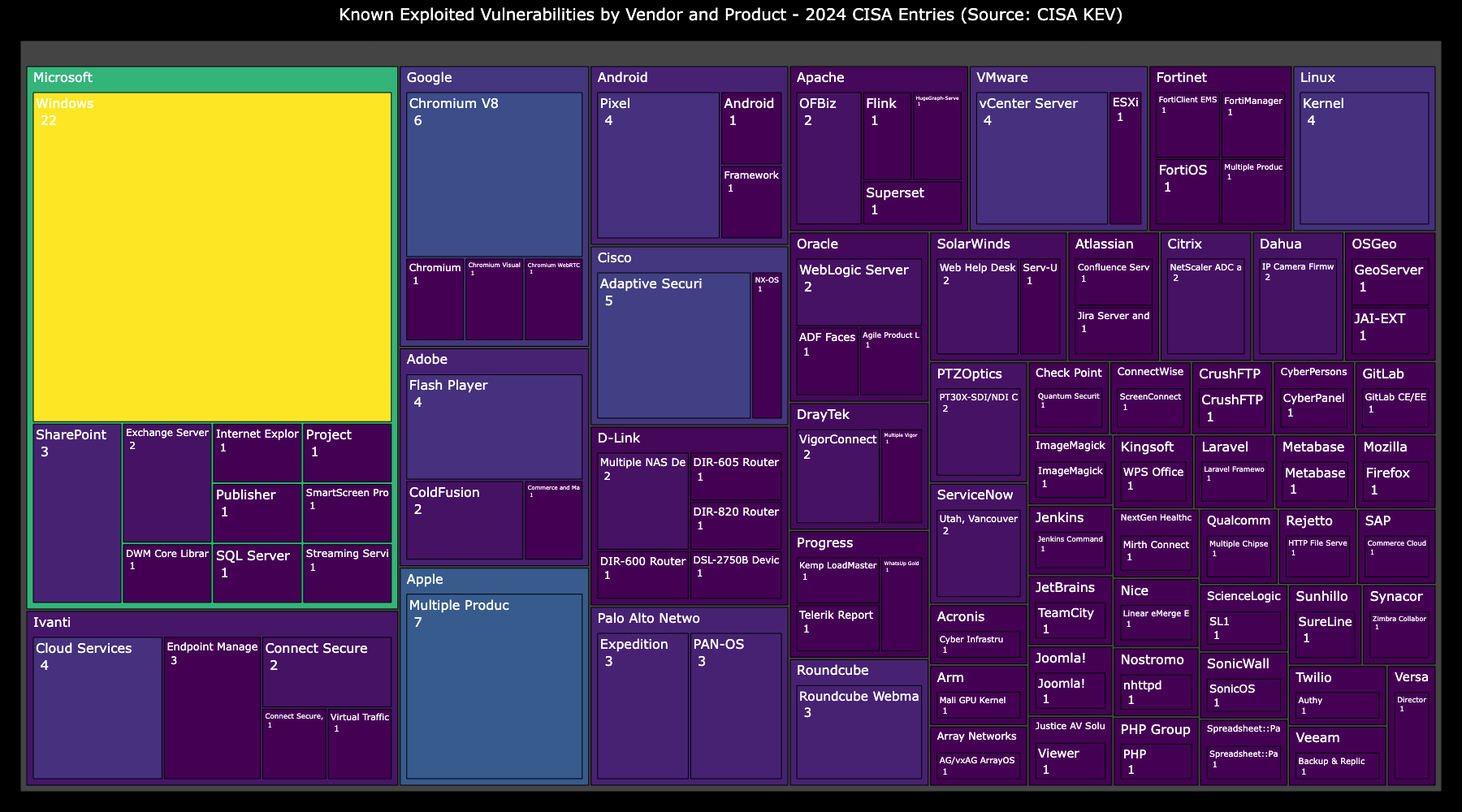
The top 10 vendors by number of vulnerabilities that CISA added to KEV in 2024 include Microsoft (34), Ivanti (11), Adobe (7), Apple (7), Android (6), CIsco (6) D-Link (6), Palo Alto Networks (6), Apache (5), and VMware (5).
The top 10 products added to CISA KEV include Microsoft Windows (22), Google Chrome/Chromium (9), Cisco ASA / FTD (5), Apple IOS Products (5), Abode Flash Player (4), Android Pixel (4), VMware Vcenter (4), Linux Kernel (4)
Additionally, there’s a notable distinction in the vulnerabilities added to the CISA KEV list. Many, such as those in Adobe Flash, had exploitation evidence publicly available years prior. This underscores differences between newly exploited vulnerabilities and the re-emergence of previously known vulnerabilities, a topic I’ll explore later in this post.
Comparing 2024 KEVS added to CISA KEV and VulnCheck KEV by day, month and year
To understand the frequency at which Known Exploited Vulnerabilities (KEVs) were added throughout the year, we created a calendar chart inspired by Jerry Gamblin’s cve.icu project. These visualizations highlight the additional patterns for KEVs across CISA KEV and VulnCheck KEV.
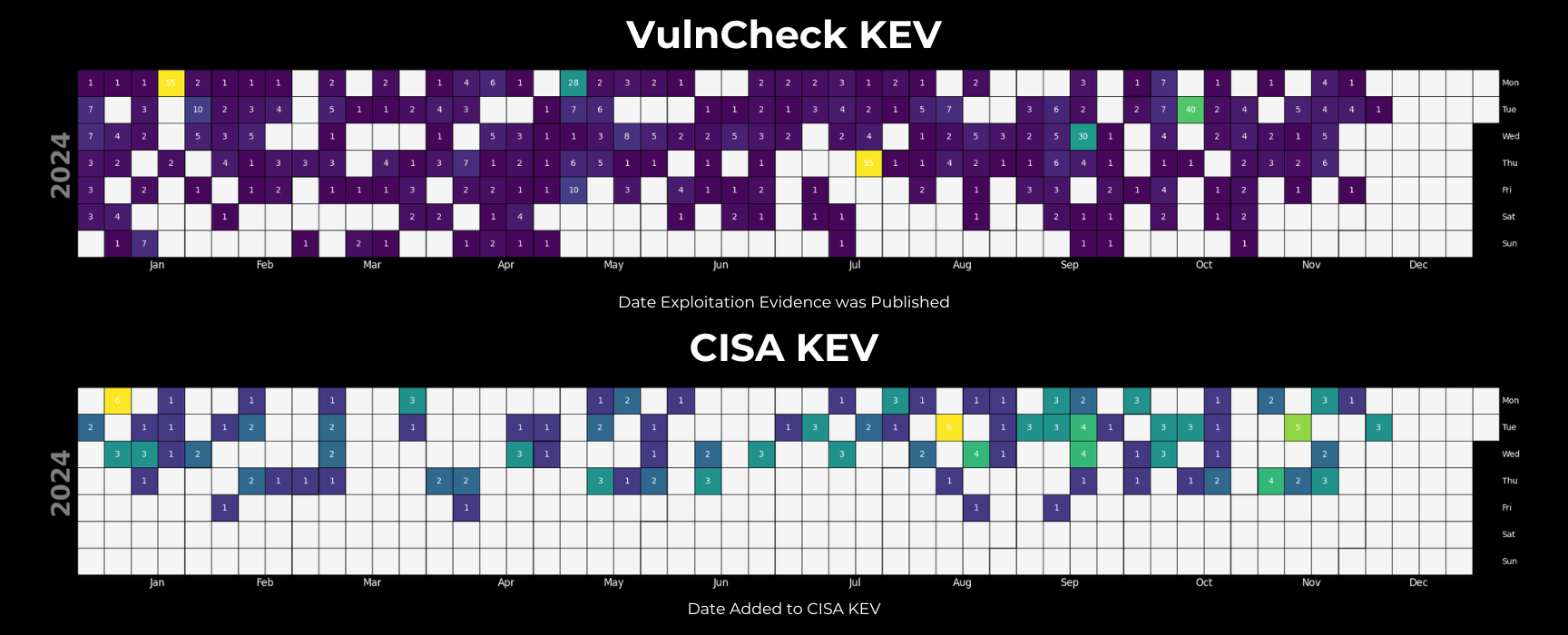
Looking at VulnCheck KEV, we see a consistent amount of exploitation activity seen for the first time throughout the year, with some larger numbers highlighted in yellow. These tend to be quarterly industry reports disclosing a larger number of vulnerabilities with observed exploitation. The highest number of vulnerabilities with exploitation evidence being added to VulnCheck KEV in a single day was 55. It’s also interesting to see a lull during US holiday seasons like Thanksgiving. We're not sure if it's security researchers or threat actors that take a break. LOL
When we look at CISA KEV, the number of vulnerabilities added is much sparser and tends to group during the weekend days, specifically Monday - Thursday, with only 4 instances of a KEV being reported on Fridays. CISA has not issued a single KEV during the weekend this year.
Historical Exploitation Evidence Availability Before CISA KEV (All CISA KEVs)
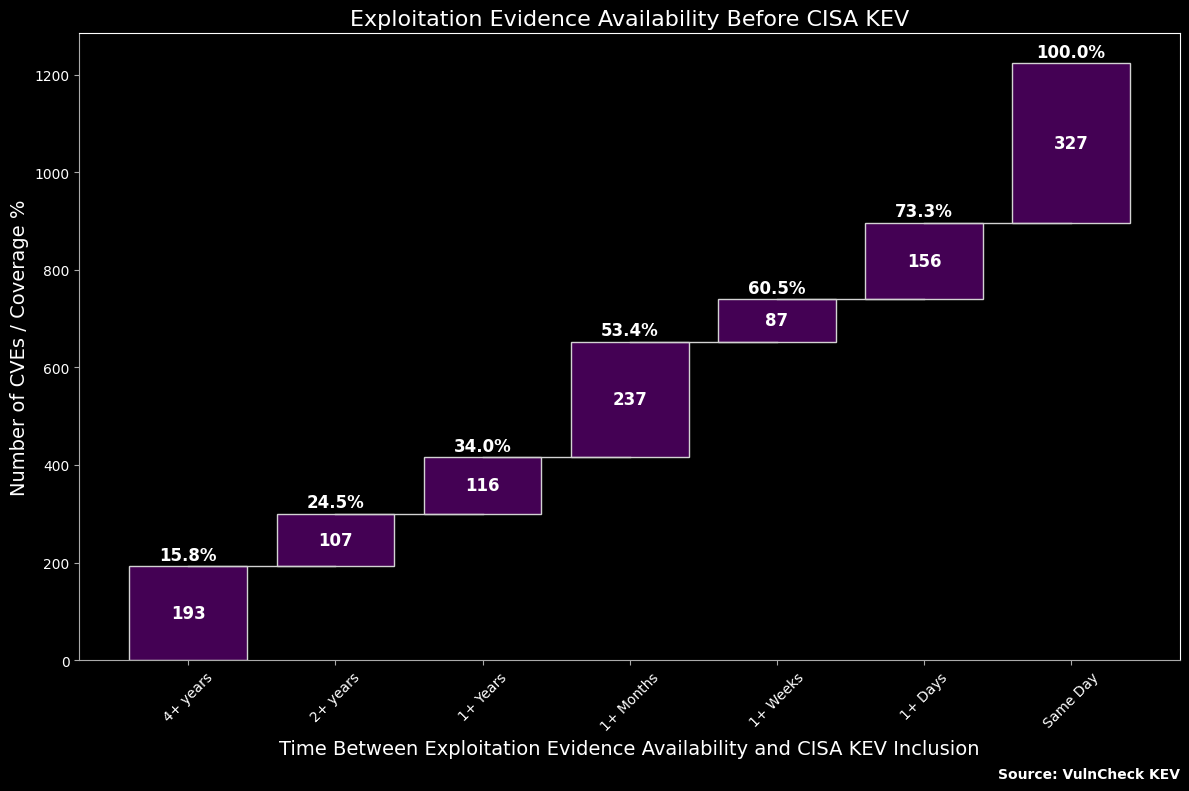
Next, we analyzed the time gap between vulnerabilities being added to CISA KEV and the availability of publicly documented exploitation evidence in VulnCheck KEV. By reviewing all historical CISA KEVs and mapping the dates of publicly available exploitation evidence.
Time Gap Insights: In 53.4% of cases, exploitation evidence is publicly available more than one month prior to the vulnerability being added to CISA KEV.
Same-Day Evidence: When exploitation evidence and CISA KEV updates coincide on the same day, it typically occurs during Patch Tuesday, when exploitation evidence is widely documented and known to be coming from reliable sources.
On occassion we see unique evidence published from CISA that wasn't available elsewhere which is a smaller subset of the 327 vulnerabilities in the same day evidence bucket.
Explore VulnCheck KEV and CISA KEV Yourself
The Jupyter Notebook used to generate this research is a free resource that uses VulnCheck’s Python SDK and community edition making it available to all.
Get started today
- Signup for VulnCheck Community
- Download the Jupyter Notebook
- Enter your API key from VulnCheck
- Make modifications and explore VulnCheck KEV and CISA KEV
About VulnCheck
VulnCheck is helping organizations not just to solve the vulnerability prioritization challenge - we’re working to help equip any product manager, CSIRT/PSIRT or SecOps team and Threat Hunting team to get faster and more accurate with infinite efficiency using VulnCheck solutions.
We knew that we needed better data, faster across the board, in our industry. So that’s what we deliver to the market. We’re going to continue to deliver key insights on vulnerability management, exploitation and major trends we can extrapolate from our dataset to continuously support practitioners.
Are you interested in learning more? If so, VulnCheck's Exploit & Vulnerability Intelligence has broad threat actor coverage. Register and demo our data today.