The CISA top routinely exploited vulnerabilities report is always a good read. While it's pretty late in the year, it offers a unique opportunity to reflect on the previous year’s exploitation trends and understand which vulnerabilities posed the greatest threats in 2023 to government organizations. Each year, the report sparks questions about why certain vulnerabilities made the list and what makes them particularly significant.
This year, we decided to explore the vulnerabilities that top CISA's list using VulnCheck Intelligence to better understand the impact and threats associated with these vulnerabilities and the detection coverage VulnCheck provides defenders.
Key Takeaways
- Exploit Availability: 14 of 15 CVEs in CISA's 2023 report have 8+ POC exploits; 13 have weaponized exploits, with 5 weaponized before public exploitation.
- Threat Actor Activity: 60 named threat actors linked to 13 CVEs; North Korea’s Silent Chollima targeted 9, while Log4j (CVE-2021-44228) remains the most exploited.
- Detection Coverage: VulnCheck provides Initial Access artifacts for 12 CVEs, enabling visibility into vulnerable hosts and detection of malicious activity.
- Host Exposure: Tens of thousands of potentially vulnerable hosts identified
- CISA’s 2023 Top Routinely Exploited Vulnerabilities report seems reasonable with the research we performed that demonstrates clear exploit availability and threat actor activity.
Exploit Proof-of-Concepts(POC) Availability
We already know the vulnerabilities in the report have confirmed exploitation. Next, we thought it would be valuable to examine exploit availability for the CVEs in CISA's report.
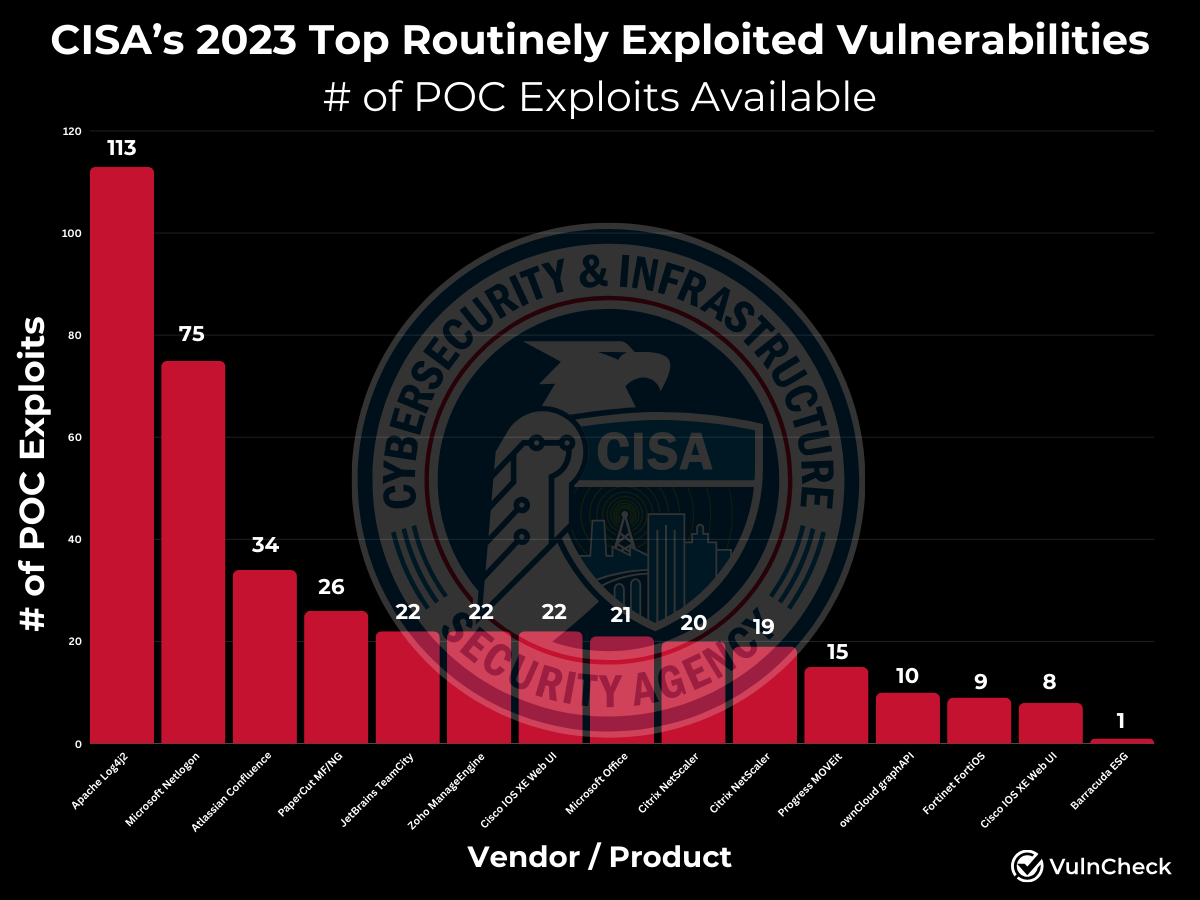
Exploit Availability:
- 14 out of 15 CVEs have 8 or more proof-of-concept (POC) exploits available. (For context, out of all CVEs, only 1,658 have 8 or more POC exploits available signifying a significant threat.)
- For these 14 CVEs, at least one POC was accessible before or on the same day the first evidence of exploitation was publicly disclosed.
The Exception:
The primary outlier is the Barracuda Email Security Gateway (ESG) CVE. Caitlin Condon pointed out a POC that was posted by the Rapid7 team which we’ve included. This case stands out because Barracuda effectively EOL’d (end-of-lifed) the device after widespread compromise. It’s a rare example of a vendor deciding to discontinue a product line after significant exploitation.
Weaponized Exploits:
- 13 out of 15 CVEs have weaponized exploits available.
- Of these, 5 weaponized exploits were available before any public evidence of exploitation.
What Do We Mean by “Weaponized Exploits”?
A weaponized exploit refers to an exploit that is explicitly malicious, such as cases where the exploit is contained within malware (e.g., a malicious Microsoft Word document), or facilitates "point & click" exploitation (e.g., works against all or most targets and works reliably, such as exploits in MetaSploit, VulnCheck Initial Access Intelligence, CANVAS, or Core Impact). Additionally, weaponized exploits typically have secondary payloads, droppers, or implants.
Threat Actor Attribution
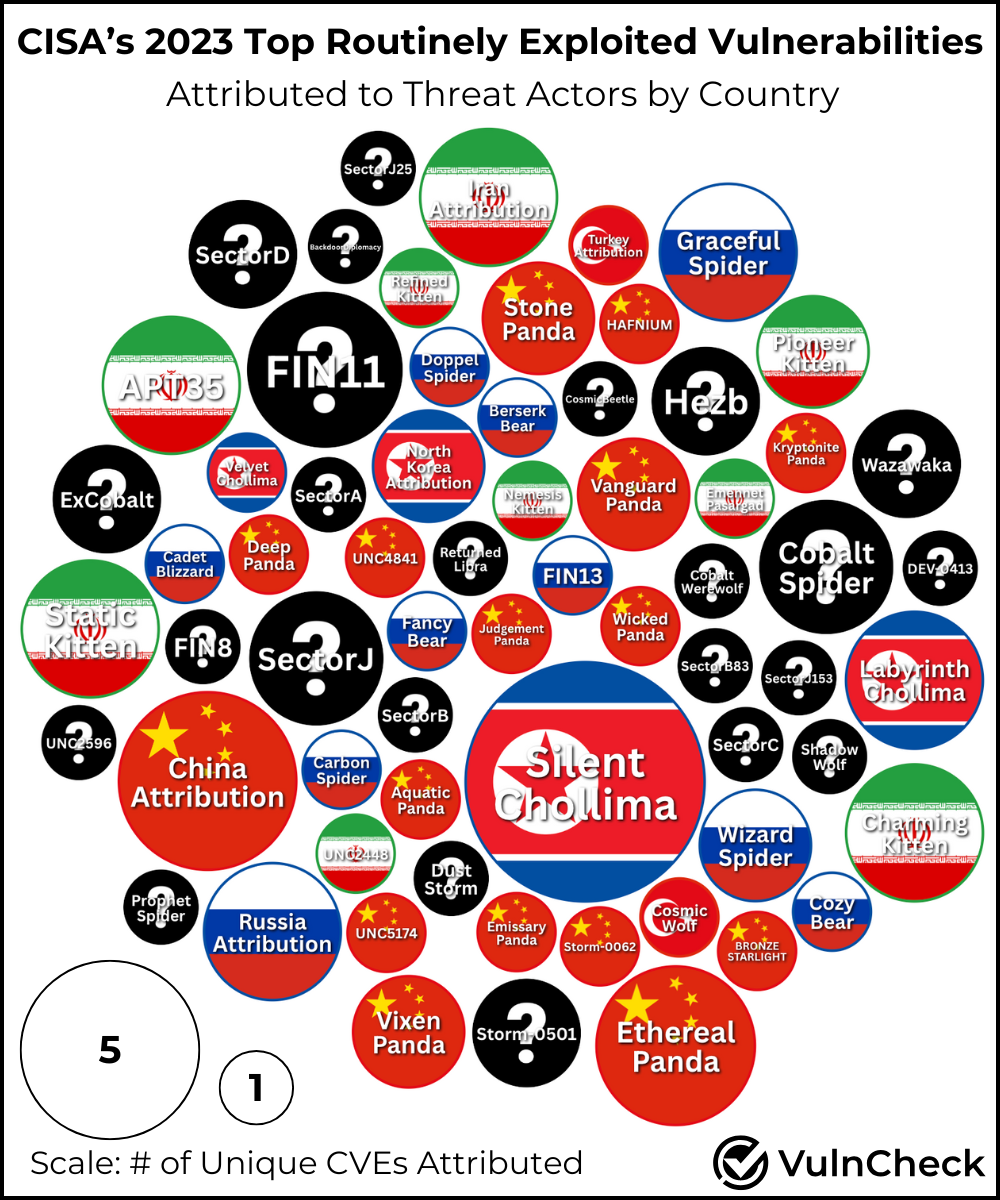
We identified 60 named threat actors associated with at least one of the CVEs in CISA’s 2023 list. 13 out of 15 CVEs in the report have named threat actors tied to them. The two CVEs without a threat actor attributed were associated with OwnCloud GraphAPI and Barracuda ESG. Additionally, we noted five more associations where the origin country was identified, but the specific threat actor was not named which we included in the chart.
Among the threat actors, North Korea’s Silent Chollima stands out, targeting 9 out of 15 CVEs in the report. Not surprisingly, the Log4j CVE (CVE-2021-44228) is associated with the most threat actors overall, with 31 named threat actors linked to its exploitation.
A quick breakdown of threat actor activity by country shows the usual suspects including: China, Russia, Iran, and North Korea with a single threat actor tied to Turkey. Here’s how the number of threat actors stack up by country:
| Country | # of Threat Actors |
|---|---|
| Unknown | 24 |
| China | 15 |
| Russia | 9 |
| Iran | 8 |
| North Korea | 3 |
| Turkey | 1 |
Detecting Exploitation w/ VulnCheck Initial Access
Out of the 15 CVEs highlighted in CISA's 2023 report, 12 have VulnCheck Initial Access artifacts which demonstrates our commitment to ensuring broad coverage of vulnerabilities that are likely to become or are exploited in the wild. These artifacts provide defenders with visibility into potential vulnerability exposures. They also aid in detecting the malicious use of exploits targeting these vulnerabilities within an organization’s environment.
For each CVE, we provide a range of detection tools including:
- Exploits
- Version scanners
- PCAPs
- Suricata rules
- Snort rules
- YARA rules
- Greynoise/Censys/Shodan/FOFA/ZoomEye Queries
- Target Docker Containers
| artifactName | Date Added | cve | exploit | versionScanner | pcap | suricataRule | snortRule | yara |
|---|---|---|---|---|---|---|---|---|
| ManageEngine SAML Transform Code Execution | 2023-01-19 | CVE-2022-47966 | ✅ | ✅ | ✅ | ✅ | ✅ | |
| PaperCut NG/MF Authentication Bypass and Code Execution | 2023-04-24 | CVE-2023-27350 | ✅ | ✅ | ✅ | ✅ | ✅ | |
| Progress MOVEit Transfer SQL Injection (guestaccess.aspx) | 2023-06-05 | CVE-2023-34362 | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ |
| Fortigate SSL VPN enc Heap Overflow | 2023-07-11 | CVE-2023-27997 | ||||||
| Citrix NetScaler Stack-Based Buffer Overflow | 2023-08-14 | CVE-2023-3519 | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ |
| JetBrains TeamCity Authentication Bypass | 2023-09-27 | CVE-2023-42793 | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ |
| Confluence Setup Reset Vulnerability | 2023-10-10 | CVE-2023-22515 | ✅ | ✅ | ✅ | ✅ | ✅ | |
| Cisco IOS XE Add Admin User | 2023-10-16 | CVE-2023-20198 | ✅ | ✅ | ✅ | ✅ | ||
| Citrix NetScaler Information Disclosure (Memory Leak) | 2023-10-25 | CVE-2023-4966 | ✅ | ✅ | ✅ | ✅ | ||
| Cisco IOS XE IPv6 Command Injection | 2023-11-02 | CVE-2023-20273 | ✅ | ✅ | ✅ | ✅ | ||
| ownCloud graphapi Information Disclosure | 2023-12-06 | CVE-2023-49103 | ✅ | ✅ | ✅ | ✅ | ||
| Apache Skywalking Log4Shell | 2023-12-11 | CVE-2021-44228 | ✅ | |||||
| ManageEngine ADManager Log4Shell | 2023-12-11 | CVE-2021-44228 | ✅ | |||||
| Apache Struts2 If-Modified-Since Header Log4Shell | 2022-11-23 | CVE-2021-44228 | ✅ | ✅ | ✅ | ✅ | ✅ | |
| Apache Struts2 URI Log4Shell | 2022-11-25 | CVE-2021-44228 | ✅ | ✅ | ✅ | ✅ | ✅ | |
| Ubiquiti UniFi Controller Authentication Log4Shell | 2022-11-25 | CVE-2021-44228 | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ |
| Apache JSPWiki URI Log4Shell | 2022-11-28 | CVE-2021-44228 | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ |
| Apache OFBiz Visitor Cookie Log4Shell | 2022-11-30 | CVE-2021-44228 | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ |
| Apache Druid HTTP DELETE Log4Shell | 2022-12-01 | CVE-2021-44228 | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ |
| Apache James POP3 Authentication Log4Shell | 2022-12-02 | CVE-2021-44228 | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ |
| Apache James SMTP Mail From Log4Shell | 2022-12-05 | CVE-2021-44228 | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ |
| Ivanti MobileIron Authentication Log4Shell | 2022-12-06 | CVE-2021-44228 | ✅ | ✅ | ✅ | ✅ | ✅ |
A Look into Potentially Vulnerable Hosts
Taking a step further to see the impact of these vulnerabilities, we looked up potentially vulnerable hosts over a 3-day period in VulnCheck IP Intelligence to see the breadth of potential targets available to threat actors. For vulnerabilities VulnCheck has developed detection artifacts for, VulnCheck measures their potential exposure on the open Internet.
| Host Type | Potentially Vulnerable Hosts |
|---|---|
| Cisco IOS XE | 92277 |
| Cisco IOS XE | 92277 |
| Fortinet FortiOS | 199570 |
| Citrix Netscaler | 24377 |
| Citrix Netscaler | 24377 |
| Apache Log4J | 65245 |
| Zoho Manage Engine | 9213 |
| OwnCloud GraphAPI | 18086 |
| Progress MOVEit | 2461 |
| JetBrains TeamCity | 2004 |
| Atlassian Confluence | 3229 |
| Papercut NG/MF | 1496 |
Our Final Thoughts
CISA’s 2023 Top Routinely Exploited Vulnerabilities Report highlights vulnerabilities that, based on our research, are highly targeted by threat actors. The report provides valuable insights into technologies frequently used within the federal government and commonly targeted. Organizations should evaluate their exposure to these technologies, enhance visibility into potential risks, leverage robust threat intelligence, maintain strong patch management practices, and implement mitigating controls, such as minimizing internet-facing exposure of these devices wherever possible.
About VulnCheck
VulnCheck is helping organizations not just to solve the vulnerability prioritization challenge - we’re working to help equip any product manager, security team and threat hunting team to get faster and more accurate intelligence with infinite efficiency using VulnCheck solutions.
We knew that we needed better data, faster across the board, in our industry. So that’s what we deliver to the market. We’re going to continue to deliver key insights on vulnerability management, exploitation and major trends we can extrapolate from our dataset to continuously support practitioners.
Are you interested in learning more? If so, VulnCheck's Exploit & Vulnerability Intelligence has the broadest coverage.