Key Takeaways
- 768 CVEs were publicly reported as exploited in the wild; up 20% YoY
- Spikes in volume of CVE reporting link back to key industry events and new sources
- In 2024, 23.6% of KEVs were known to be exploited on or before the day their CVEs were publicly disclosed
- There were over 100 unique sources to be the first to report an CVE with third-party vendors leading the charge (i.e. Security companies (e.g., CheckPoint, Aqua Security, Fortinet, F5), government agencies (e.g., DOD, CISA, NHS), and non-profits (e.g., Shadow Server)
2024 marked another banner year for threat actors targeting the exploitation of vulnerabilities. Exploitation disclosures came from various sources, including product companies, security vendors, government agencies, non-profits, and media outlets worldwide. This blog post examines broader trends across exploited vulnerabilities where exploitation was first publicly disclosed in 2024, leveraging insights from VulnCheck KEV, a free community resource launched at the beginning of 2024.
Growth in Publicly Reported Exploitation
In 2024, VulnCheck identified 768 CVEs that were publicly reported as exploited in the wild for the first time. This is an increase of 20% from 2023 when there were 639 CVEs that were publicly reported as exploited in the wild for the first time. During 2024, 1% of the CVEs published were reported publicly as exploited in the wild, aligning closely with historical trends outlined in our State of Exploitation Report. This number is expected to grow as exploitation is often discovered long after a CVE is published.
How many vulnerabilities are reported to be exploited each month for the first time?
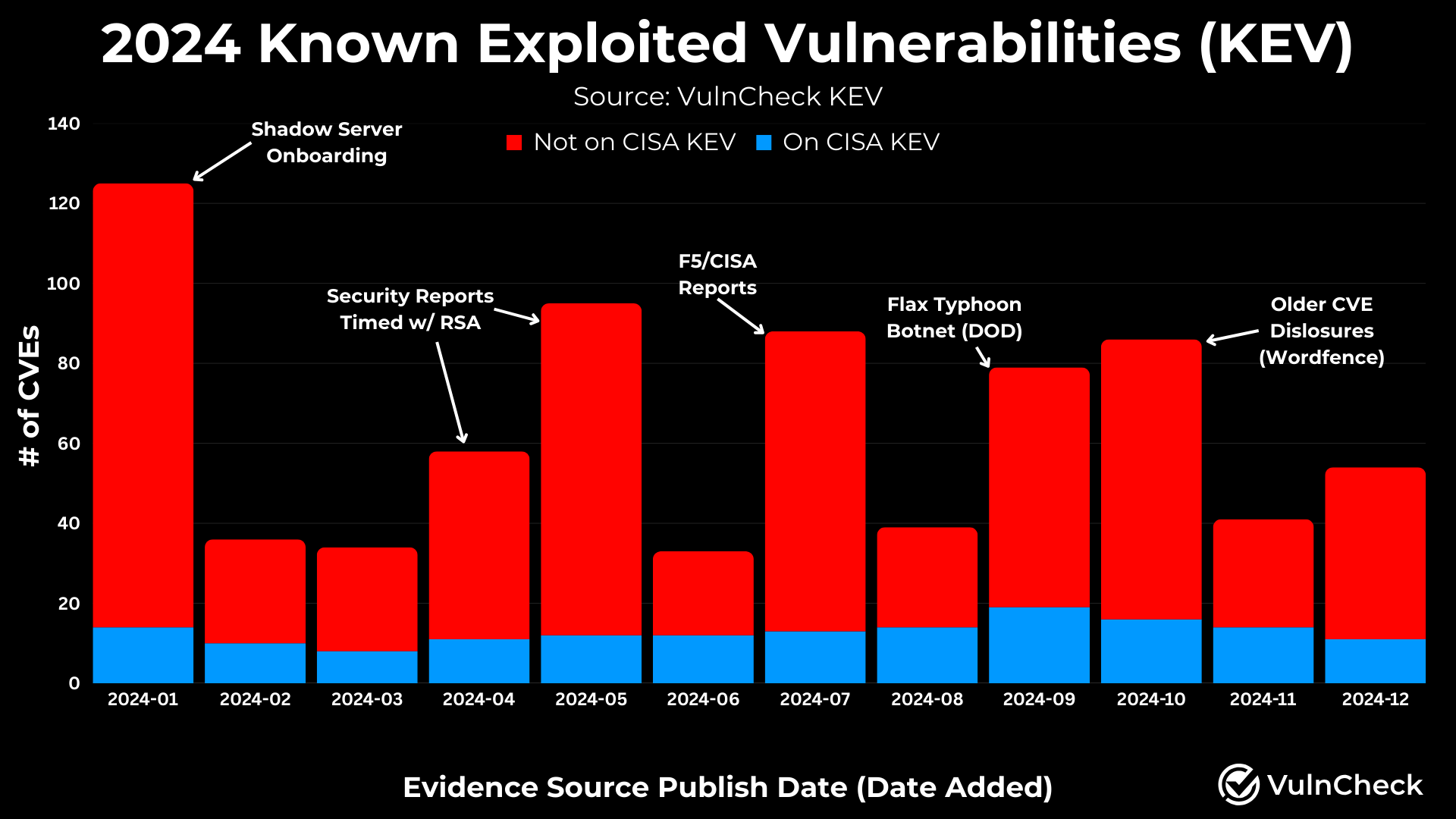
By analyzing reported exploitation by month, we gain a better understanding of the volume of CVEs that are likely to require immediate attention as they are discovered to be exploited in the wild. While the baseline of exploited CVEs ranged from 30-50 per month, notable spikes were observed during certain periods:
- April/May: Increased reports during RSA and end-of-quarter reports.
- Onboarding of New Sources: The onboarding of ShadowServer into January.
- F5/CISA & DOD Reports: Industry reports, including the Flax Typhoon botnet disclosure.
- Wordfence Disclosures: We coordinated with Wordfence, which issued CVEs for vulnerabilities they had evidence for but no CVE ID.
These spikes underscore how industry events and new resources impact reporting volumes on exploitation.We encourage organizations to publicly disclose any instances where there is exploitation activity.
How Quickly are Vulnerabilities Being Exploited?
A common concern is how quickly vulnerabilities are exploited after disclosure. In 2024, 23.6% of KEVs were known to be exploited on or before the day their CVEs were publicly disclosed, a slight decrease from 2023's 27%. Despite the buzz around "zero-day" exploitation, these findings indicate that exploitation can happen at any time in a vulnerability's lifecycle.
 Source: VulnCheck Exploitation Timelne Jupyter Notebook
Source: VulnCheck Exploitation Timelne Jupyter Notebook
Who is the First to Publicly Report Exploitation?

Of the 768 CVEs first reported as exploited in 2024, 112 unique sources provided initial evidence. These sources include:
- Third Parties: Security companies (e.g., CheckPoint, Aqua Security, Fortinet, F5), government agencies (e.g., DOD, CISA, NHS), and non-profits (e.g., Shadow Server).
- Product Companies: Microsoft, Google, Apple, Cisco, Ivanti, and others frequently disclosed exploitation of their own products, as well as third-party vulnerabilities.
- Social Media / Blogs: Infosec Exchange, X, Linkedin, Medium
VulnCheck KEV was created to provide security teams with early and broad visibility into exploited vulnerabilities regardless of where the disclosure happens. Our mission remains to empower defenders by offering this resource free of charge.
Considerations / Bias
We make a strong effort to be as transparent as possible with our research and you can also validate it yourself with free access to VulnCheck KEV. Here are some considerations that might pose Bias in our research:
- We onboarded ShadowServer over a three month period starting in November 2023. Several of these CVEs are likely to have been identified prior to us adding this as a source so there is likely an increase in the number of CVEs associated with Shadow Server that could be attributed to an earlier date.
- We worked with Wordfence to coordinate the disclosure of CVEs that were being exploited which we outlined above.
- It’s possible there are other resources for public exploitation that we haven’t captured. Therefore, if you are aware of any CVEs we missed exploitation evidence on, please let us know. Generally, we find that things that are widely exploited tend to surface publicly pretty quickly.
About VulnCheck
VulnCheck is helping organizations not just to solve the vulnerability prioritization challenge - we’re working to help equip any product manager, security team and threat hunting team to get faster and more accurate intelligence with infinite efficiency using VulnCheck solutions.
We knew that we needed better data, faster across the board, in our industry. So that’s what we deliver to the market. We’re going to continue to deliver key insights on vulnerability management, exploitation and major trends we can extrapolate from our dataset to continuously support practitioners.
Are you interested in learning more? If so, VulnCheck's Exploit & Vulnerability Intelligence has the broadest coverage.