In this series, we will explore vulnerability disclosure and exploitation, drawing insights from VulnCheck’s Exploit and Vulnerability Intelligence service.
Our goal is to offer valuable perspectives for the security community, starting with an exploration of the last decade's trends in vulnerability disclosure, exploitation, weaponization and exploit availability from 2014 to 2023.
A Look into the Last Decade of Vulnerability Exploitation… 2014 - 2023
Overview
Over the past decade, security teams have faced unwavering persistence by threat actors, evolving their tactics in response to security measures. While credential compromise and phishing made up the historical bulk of threat actor activity, as security controls such as MFA have become more widely adopted, adversaries have shifted their tactics to expand their reach using the exploitation of vulnerabilities to gain initial access into an organization.
Mandiant's M-Trends 2024 Report highlights a significant shift towards exploiting vulnerabilities, with 38% of intrusions in 2023 initiated through exploitation[1] and Verizon’s 2024 Data Breach Investigations Report (DBIR), reports a massive 180% increase in vulnerability exploitation.[2]
As we analyze CVE data, a clear pattern emerges: a surge in vulnerability disclosure, publicly available exploits, and known exploitation. This exponential growth underscores the pressing urgency of vulnerability management.
Key Findings
Growth Trends
- CVEs with known exploitation grew at a 19.7% annual growth rate.
- CVE disclosure grew at a rate of 14.1% annual growth rate
- CVEs with Publicly available Proof-of-Concept exploits grew at a rate of 11.8%
Exploitation Trends
- 1.1% of vulnerabilities are publicly known to have been exploited in the wild.
- 2% of vulnerabilities are known to be weaponized
- 31% of vulnerabilities have Proof-of-Concept Exploit Code
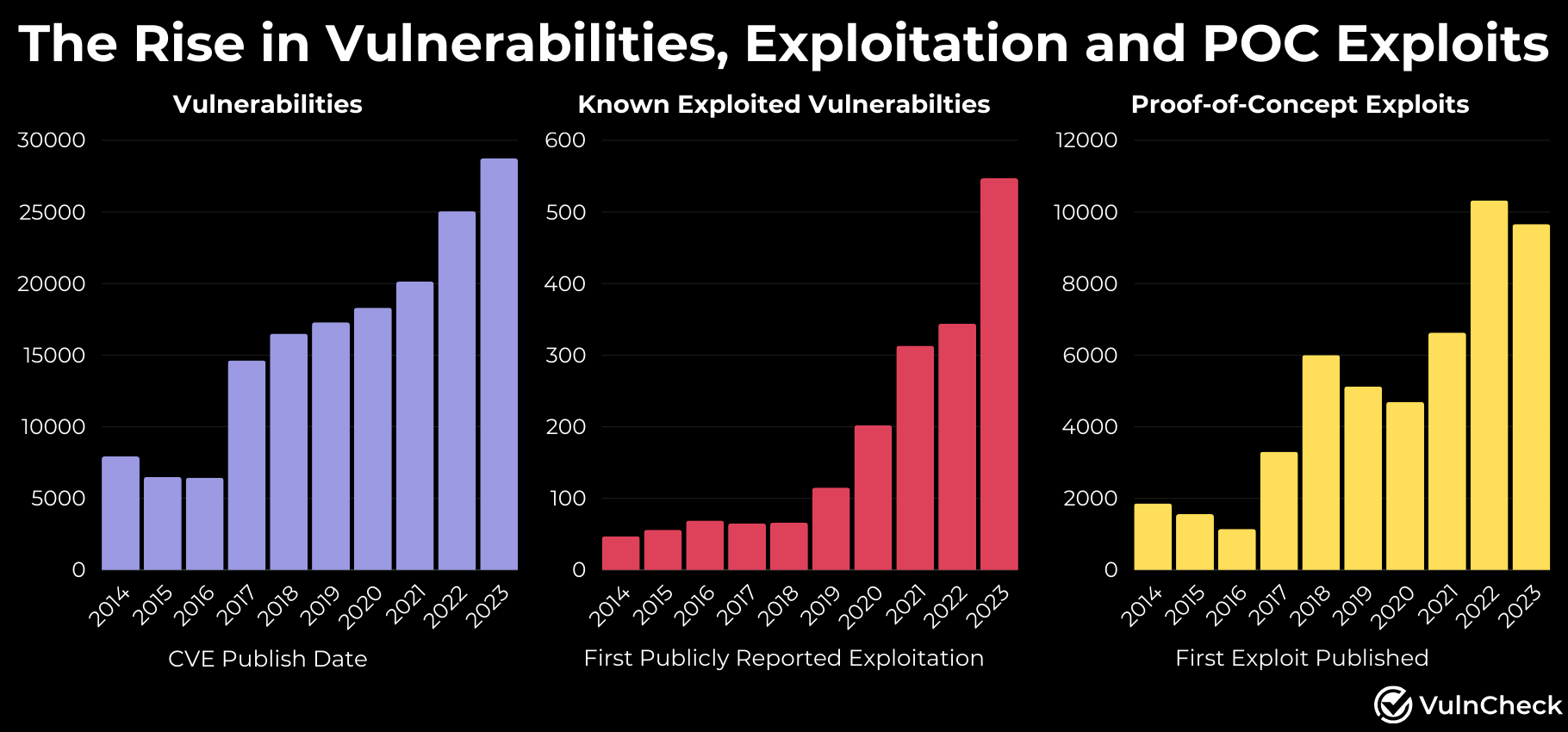
The Rise in Vulnerabilities, Exploitation and POC Exploits
Between 2014 and 2023, we witnessed a rapid escalation in vulnerabilities, publicly available exploits, and known exploitation. During this period, CVE disclosures surged at a 14.1% annual growth rate, unique CVEs with publicly available exploits increased by 11.8% annually, and the number of unique CVEs with known exploitation skyrocketed by 19.7% annually.
As the trend of increased vulnerability disclosure continues its rapid ascent, we note a similar rise in known exploitation and the availability of proof-of-concept exploits. This alignment serves as a clear indicator for security teams to anticipate a rise in known exploited vulnerabilities and the availability of POC exploit code.

Zooming In: Known Exploited Vulnerabilities, Weaponization, and Exploits
Now let’s zoom further into the CVE data from 2014 and 2023 to get more perspective on exploitation, weaponization and the availability of Proof-of-Concept Exploits. This analysis offers foundational insights that can drive improved vulnerability prioritization outcomes.
How Many Vulnerabilities are Known to Be Exploited in the Wild?
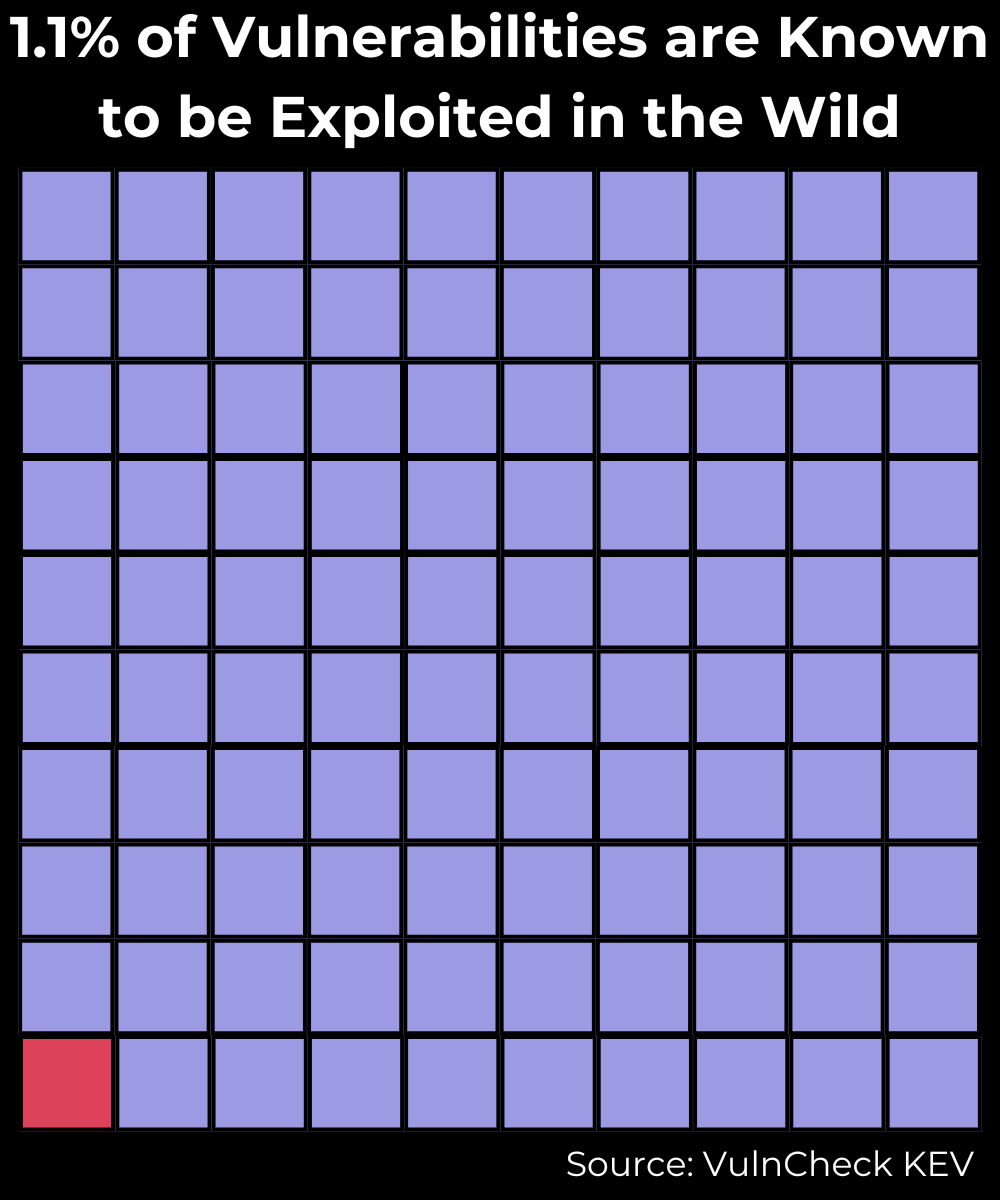
Analysis using VulnCheck’s Know Exploited Vulnerabilities (KEV) catalog reveals that between 2014 and 2023, 1.1% of all published vulnerabilities were exploited in the wild. We highly recommend prioritizing known exploitation as an immediate and optimal starting point for addressing vulnerabilities, particularly those that pose the highest threat to an organization, especially when exposed to the internet.
VulnCheck Known Exploited Vulnerabilities Catalog is the most comprehensive index of publicly referenceable vulnerabilities known to be exploited in the wild and encompasses all data from CISA KEV. We offer this to the community at no cost.
How Many Vulnerabilities are Known to be Weaponized?
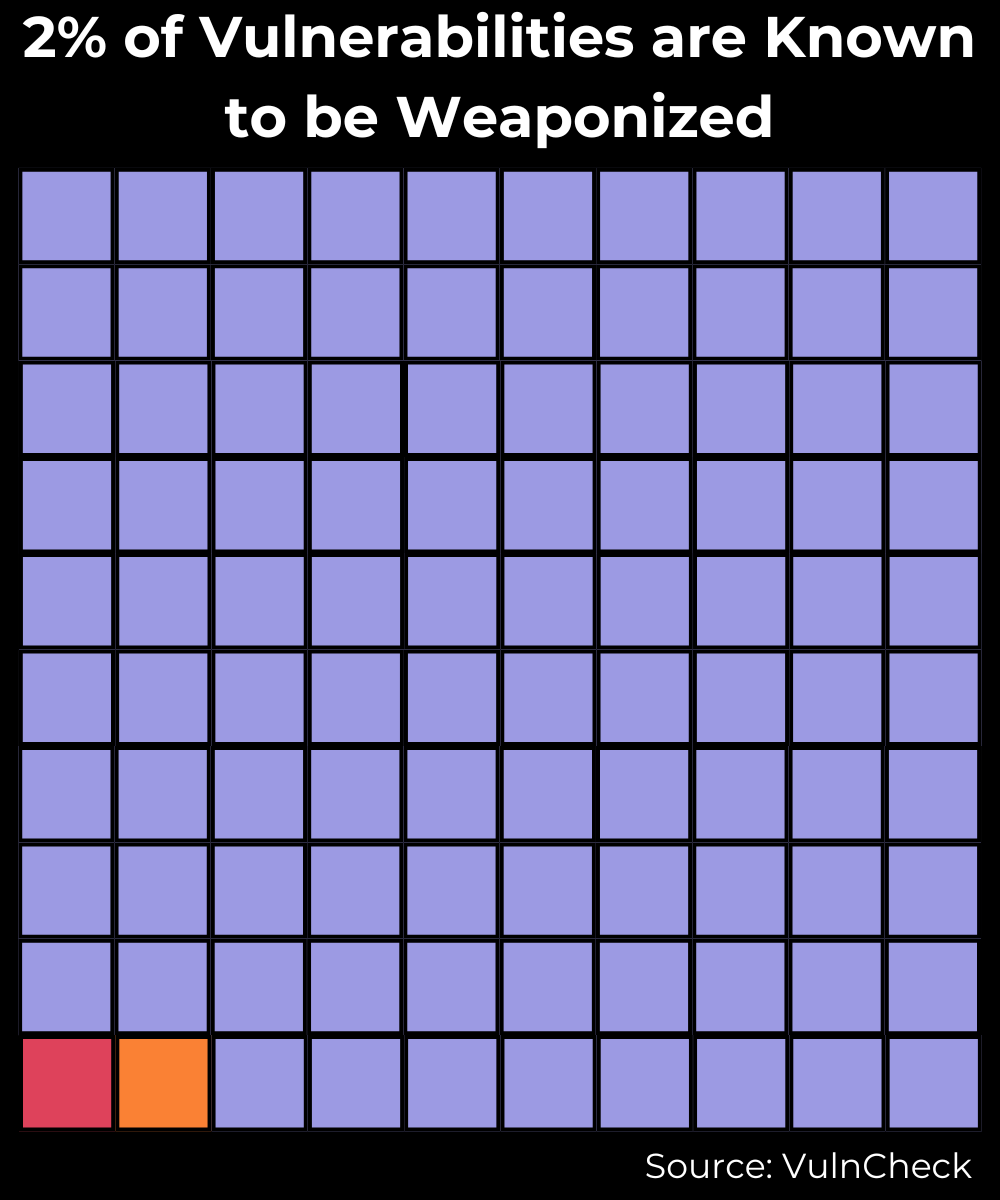
Expanding our analysis to encompass weaponized vulnerabilities uncovers that between 2014 and 2023, 2% of all disclosed vulnerabilities have been weaponized. Given their heightened risk, weaponized vulnerabilities naturally warrant prioritized attention for remediation, as they possess a high likelihood of being exploited in the wild, if not already.
What defines a weaponized vulnerability?
It's one that has either been exploited in the wild or has an available exploit capable of delivering a significant payload.
How many Vulnerabilities have a Publicly Available Proof-of-Concept Exploit?
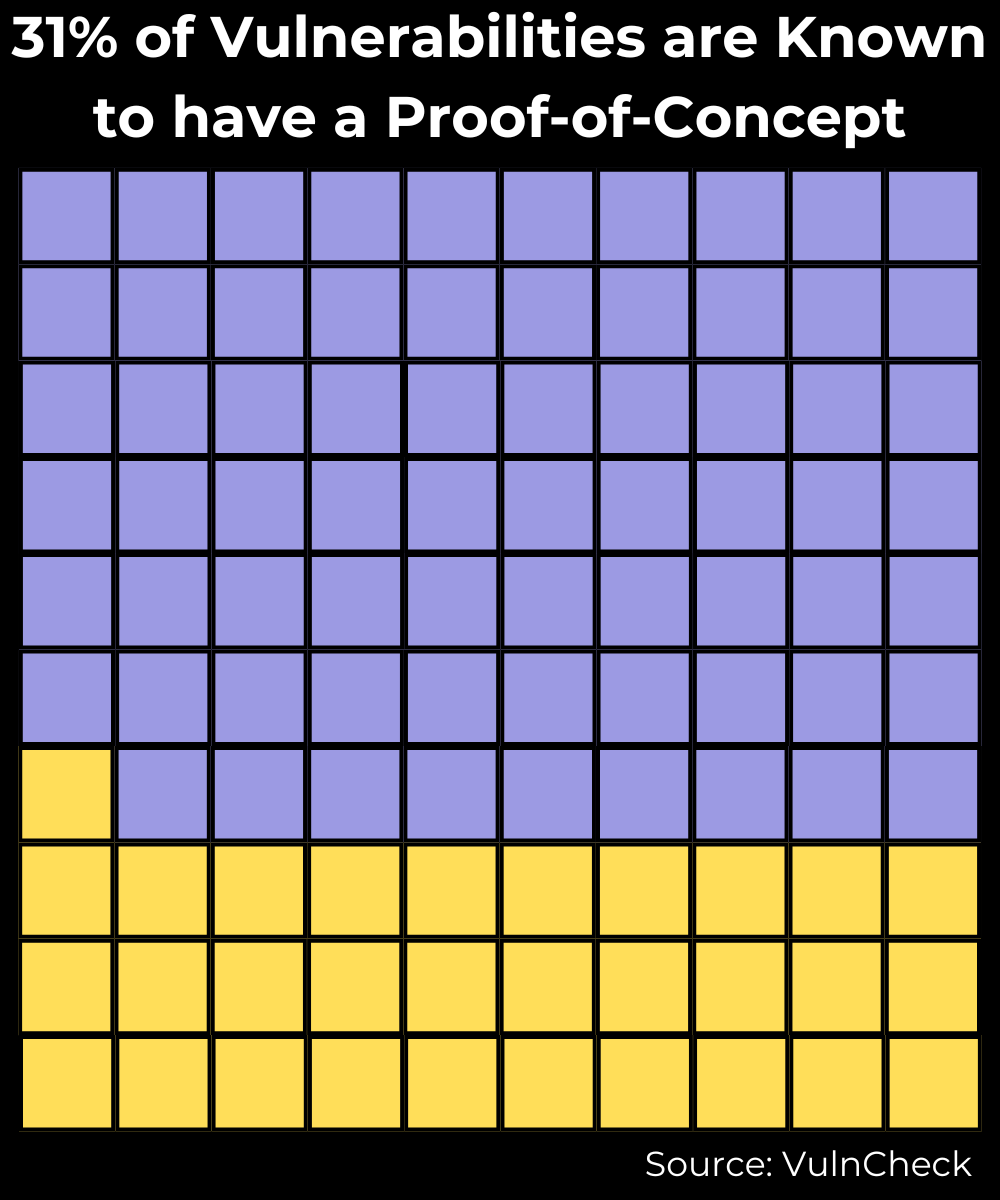
Expanding our analysis to encompass vulnerabilities with a Proof-of-Concept (POC) exploit, we find that between 2014 and 2023, 31% of vulnerabilities have at least one POC exploit available.
How many Vulnerabilities Exploited in the Wild have a Publicly Available Proof-of-Concept Exploit?
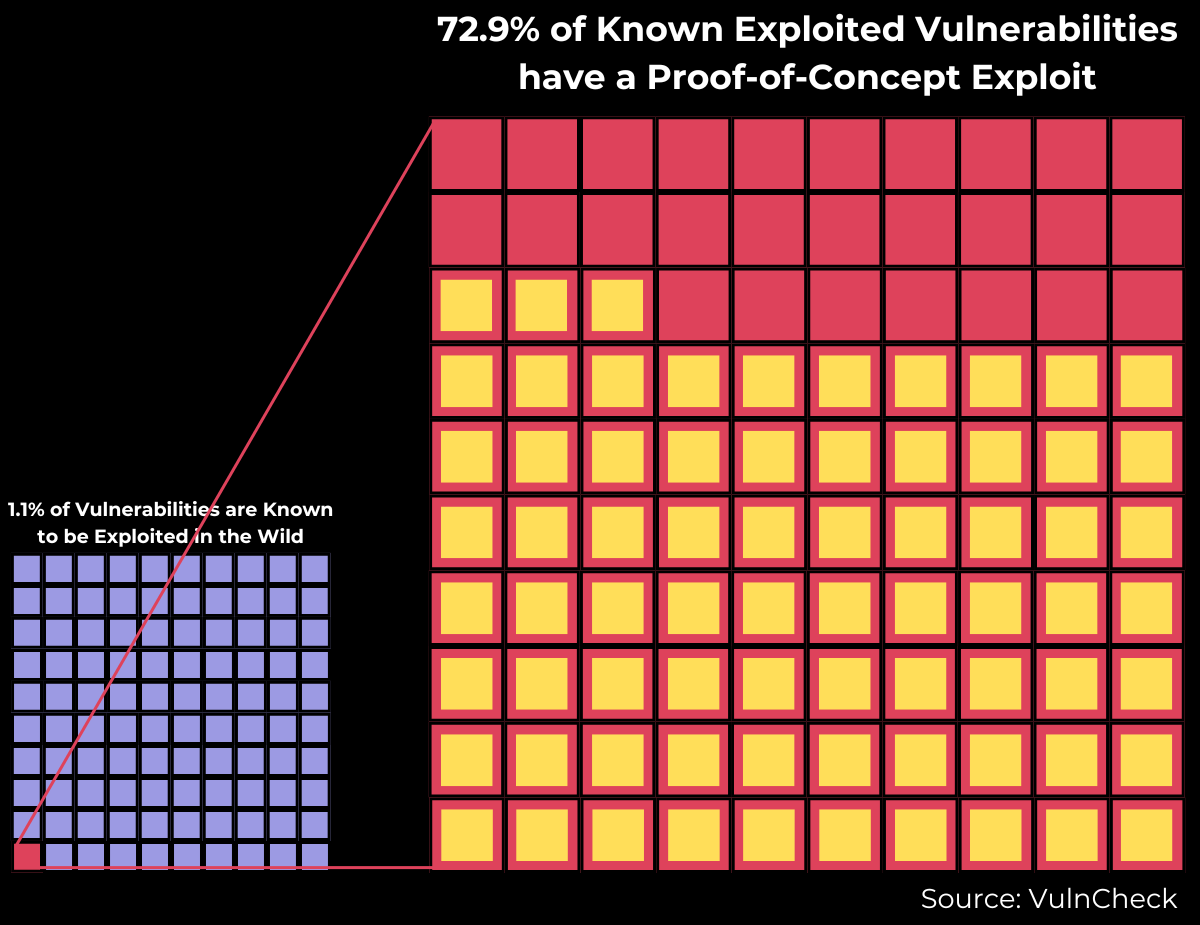 Interestingly, over the same period, 72.9% of vulnerabilities known to be exploited in the wild are associated with a POC exploit. This underscores that vulnerabilities with a known POC pose a significantly higher threat than those without. We will dive deeper into this correlation as we continue our research.
Interestingly, over the same period, 72.9% of vulnerabilities known to be exploited in the wild are associated with a POC exploit. This underscores that vulnerabilities with a known POC pose a significantly higher threat than those without. We will dive deeper into this correlation as we continue our research.
Considering Data Biases
We all carry our own biases when it comes to data and it's interpretation, and I'd like to offer some perspective on our observations. The primary focus of this series is examining VulnCheck data, which is sourced from hundreds of indexes. However, it's important to acknowledge that data biases persist. Therefore, we welcome feedback and additional insights that broaden our understanding.
For instance, Cyentia’s report, “Prioritization to Prediction: Volume 1”[3], noted that 2% of published vulnerabilities had observed exploits in the wild. This closely aligns with VulnCheck’s definition of weaponization, suggesting consistency in trends over time, albeit from an earlier time period. We'd like to explore other reports on exploitation more and remain open to collaboration so please share your thoughts on any other sources we can learn. Personally, I'd suggest exploring Cyentia's Prioritization to Prediction Vol. 9 and Bitsight's Global View of CISA KEV Catalog which I plan to draw comparisons with throughout this series when I have the chance.
Expanding Our Research
The aim of this post has been to lay down foundational research on vulnerability disclosure, known exploitation, weaponized vulnerabilities, and vulnerabilities with Proof-of-Concept exploits. While I’m not offering an immediate silver bullet for vulnerability prioritization, my hope is that this series provides useful insights that will provide an evidence-based understanding into vulnerabilities and exploitation. We do know that focusing on remediating known exploitation and weaponized vulnerabilities offers a substantial return on investment and is a useful place to start, especially when they're internet-facing on initial access devices.
For those eager to dive deeper, I encourage you to research along with me as we explore the vulnerability and exploitation landscape. You can start by utilizing VulnCheck Community a free resource including VulnCheck KEV and VulnCheck NVD++. In our next post, we’ll prioritize exploring exploitation across 2023 at a deeper level.
Until then...
Cheers, Patrick
References:
[1] Mandiant M-Trends 2024 Special Report
[3] Prioritization to Prediction: Volume 1
About VulnCheck
VulnCheck is helping organizations not just to solve the vulnerability prioritization challenge - we’re working to help equip any product manager, CSIRT/PSIRT or SecOps team and Threat Hunting team to get faster and more accurate with infinite efficiency using VulnCheck solutions.
We knew that we needed better data, faster across the board, in our industry. So that’s what we deliver to the market. We’re going to continue to deliver key insights on vulnerability management, exploitation and major trends we can extrapolate from our dataset to continuously support practitioners.
Are you interested in learning more? If so, VulnCheck's Exploit & Vulnerability Intelligence has broad threat actor coverage. Register and demo our data today.